| View previous topic :: View next topic |
| Author |
Message |
zanor29
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 25 Nov 2020
Posts: 2
|
 Posted: Wed Nov 25, 2020 3:24 am Post subject: Unable to get dll module symbols in driver protected game Posted: Wed Nov 25, 2020 3:24 am Post subject: Unable to get dll module symbols in driver protected game |
 |
|
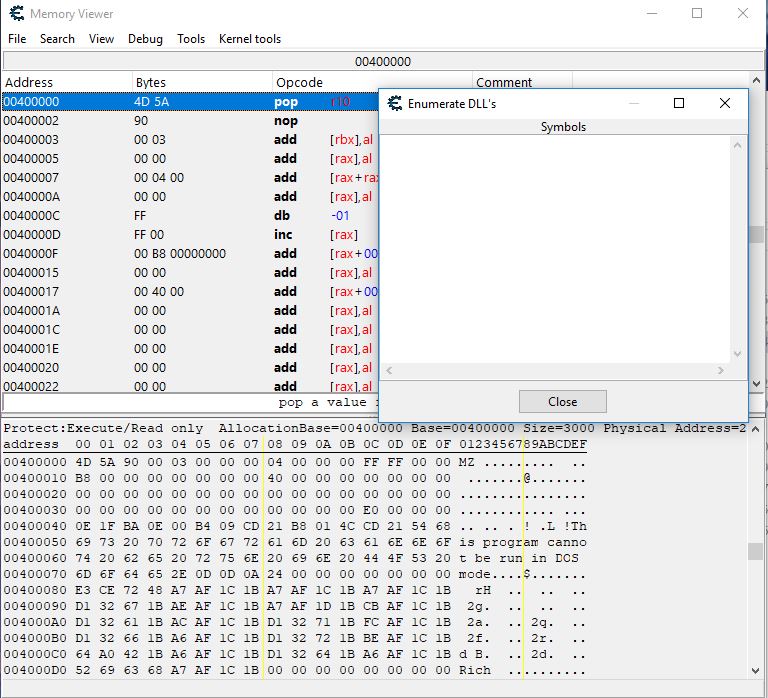
As the title says, I cannot see any dll symbols when attaching CE to a driver protected game. Already changed CE settings to kernel routines for OpenProcess and Read/Write
The driver protected game uses ObRegisterCallbacks to strip userland access
In the following image, this is from attaching to a driver protected game
This is the exe base address, it reads fine but cannot retrieve any dll symbols
Using 7.2 btw
Is there a way around this?
I also tried process hacker without admin, with its driver, it can view module information on admin and driver protected process
| Description: |
|
| Filesize: |
129.15 KB |
| Viewed: |
1172 Time(s) |
|
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 472 Reputation: 472
Joined: 09 May 2003
Posts: 25876
Location: The netherlands
|
 Posted: Wed Nov 25, 2020 4:32 am Post subject: Posted: Wed Nov 25, 2020 4:32 am Post subject: |
 |
|
try this lua code before opening the process
| Code: |
autoAssemble(string.format([[
NtOpenProcess:
jmp %x
]],dbk_NtOpenProcess),true)
|
(Also, you can use the windows symbols to find the ObregisterCallback pointers, and remove the one that you don't want to intercept openProcess)
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
zanor29
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 25 Nov 2020
Posts: 2
|
 Posted: Wed Nov 25, 2020 8:40 pm Post subject: Posted: Wed Nov 25, 2020 8:40 pm Post subject: |
 |
|
| Dark Byte wrote: | try this lua code before opening the process
| Code: |
autoAssemble(string.format([[
NtOpenProcess:
jmp %x
]],dbk_NtOpenProcess),true)
|
(Also, you can use the windows symbols to find the ObregisterCallback pointers, and remove the one that you don't want to intercept openProcess) |
Tried the lua script, didn't work
As of removing the callback, I used pchunter to remove it's PreOperation callback and it BSOD'd me with kernel_security_check_failure
|
|
| Back to top |
|
 |
|

 Reputation: 472
Reputation: 472

