| View previous topic :: View next topic |
| Author |
Message |
Bedopies
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 25 Feb 2019
Posts: 13
|
 Posted: Mon Apr 11, 2022 11:03 am Post subject: Weird createThread call and no functions "Enumerate DLL Posted: Mon Apr 11, 2022 11:03 am Post subject: Weird createThread call and no functions "Enumerate DLL |
 |
|
Im reversing an app and I got some problems.
I tried to use Scylla in x64dbg to dump binary but I got 0 valid apis and finally Imports in IDA are empty.
I tried pe-sieve64.exe /imp 3 and later 5 /shellc /pid 3096 but there's lack of imports in IDA too.
In CE -> Enumerate DLL's and Symbols there's a lot more DLLs and their functions (that's why I think there's lack of Imports in previous dumps)
(?) Also, if I check CE -> Enumerate DLL's and Symbols little bit later than usual, I can see DLL's only without any functions.
How can this thing be achieved?
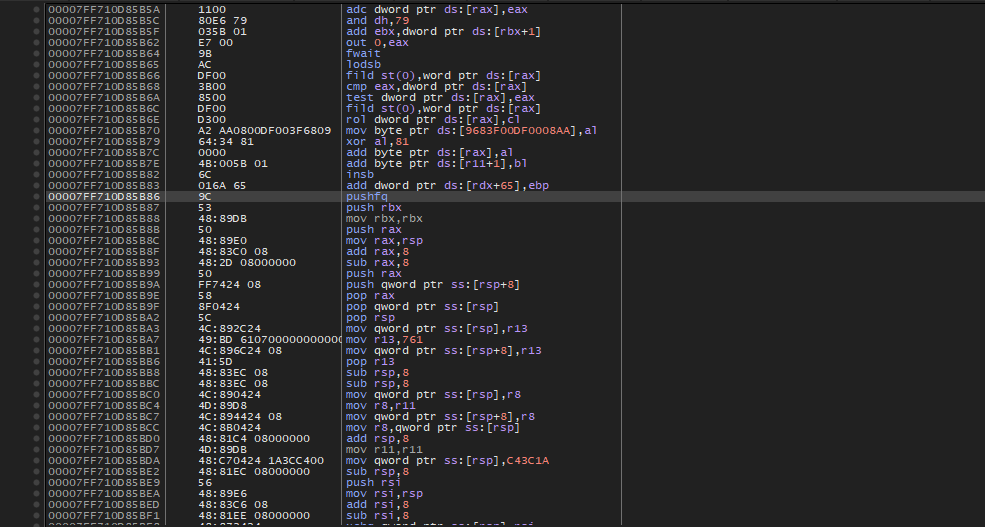
Additionally (the app is multi-threaded), I tried to see where CreateThread is called and it's really weird for me. What is goin on here? Screen in attachment.
| Description: |
| createThread call location |
|
| Filesize: |
107.83 KB |
| Viewed: |
2781 Time(s) |
|
|
|
| Back to top |
|
 |
TsTg
Master Cheater
 Reputation: 5 Reputation: 5
Joined: 12 Dec 2012
Posts: 340
Location: Somewhere....
|
 Posted: Mon Apr 11, 2022 11:55 am Post subject: Posted: Mon Apr 11, 2022 11:55 am Post subject: |
 |
|
seems like a very well obfuscated and packed executable file, you need to identify what the exe is actually packed with first, there are some tools (cant say the names, so please google exe detect tools) they might help with that. the picture you posted is a code starting with some junk code, used alot to prevent tracing and mislead the reverse engineering.
one question tho: is this location the entrypoint of the new thread, or it was supposed to be where CreateThread() API got called ?
|
|
| Back to top |
|
 |
Bedopies
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 25 Feb 2019
Posts: 13
|
 Posted: Mon Apr 11, 2022 12:14 pm Post subject: Posted: Mon Apr 11, 2022 12:14 pm Post subject: |
 |
|
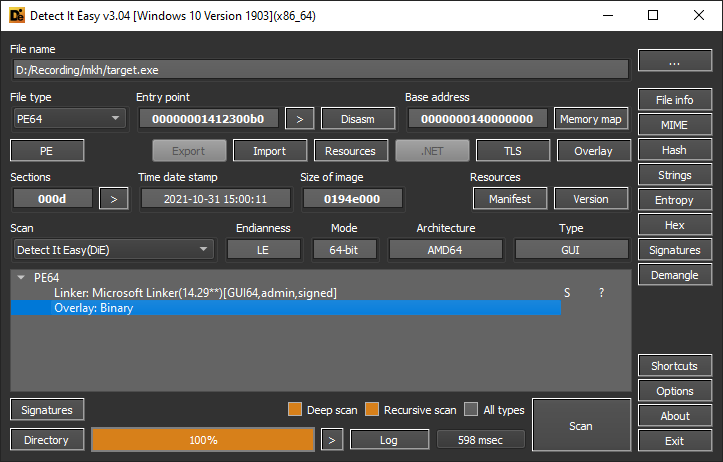
Tools to identify (at least this one started with 'D' letter) said nothing (attachment). The code from the picture is showing the location where I got redirected when did "Step Out" / from callstack (the createThread lpStartAddress is diffrent address, forwarding to "normal", easier function).
Btw. The entry point of the binary seems like packer for me (thats why I tried to dump binary at runtime), but to be honest I dont know what is the visual diffrence between packer and virtualization.
| Description: |
|
| Filesize: |
25.79 KB |
| Viewed: |
2755 Time(s) |
|
|
|
| Back to top |
|
 |
TsTg
Master Cheater
 Reputation: 5 Reputation: 5
Joined: 12 Dec 2012
Posts: 340
Location: Somewhere....
|
 Posted: Mon Apr 11, 2022 12:24 pm Post subject: Posted: Mon Apr 11, 2022 12:24 pm Post subject: |
 |
|
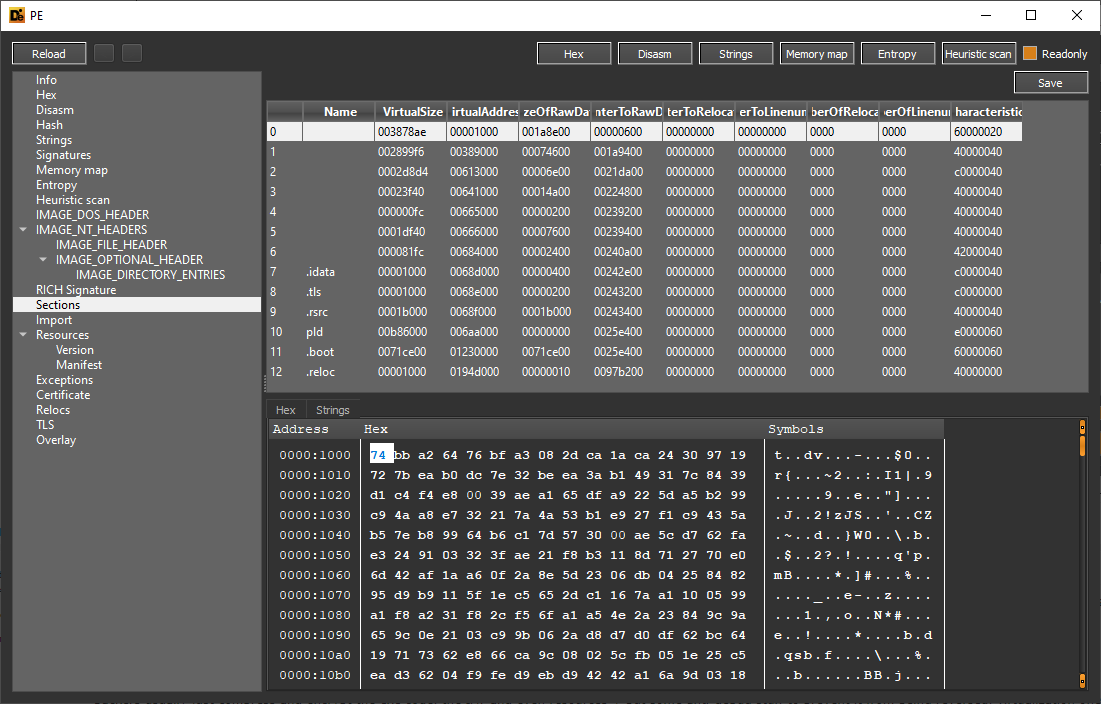
can you post a picture with the section names (the > button on the left) and another for the entropy (button on the right), and there is a a tool ExeInfo Pe, give that a try.
| Quote: | | visual diffrence between packer and virtualization. |
packers usually just compress and encrypt the exe code, the IAT and even resources + put some anti-debug stuff to prevent it from being reversed, virtualization ones is harder to work on as they create a sort of custom cpu instructions and run it inside the application process, where those instructions are translated back-and-forth in order for the app to run
|
|
| Back to top |
|
 |
Bedopies
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 25 Feb 2019
Posts: 13
|
 Posted: Mon Apr 11, 2022 1:17 pm Post subject: Posted: Mon Apr 11, 2022 1:17 pm Post subject: |
 |
|
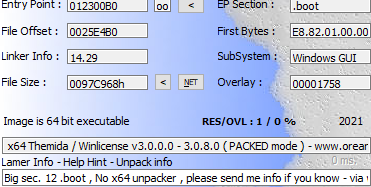
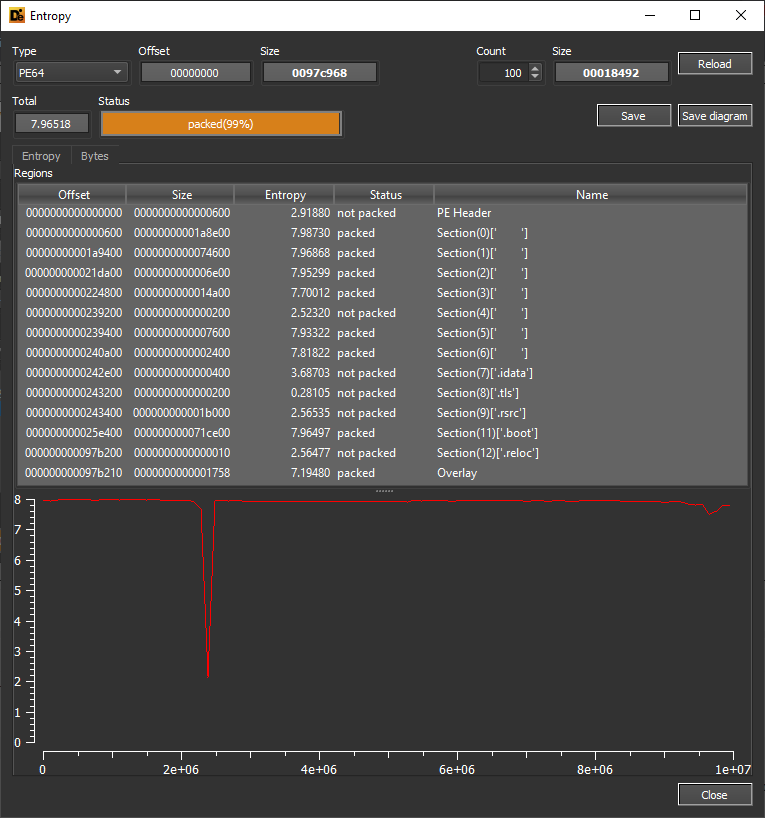
I gave exeinfo a try, and that "Themida Debugger detected" was not a bait (I thought it was the bait because it was too easy to bypass CallBack / Terminate process / IsDebuggerPresent lol).
| Description: |
|
| Filesize: |
40.18 KB |
| Viewed: |
2737 Time(s) |
|
| Description: |
|
| Filesize: |
65.71 KB |
| Viewed: |
2737 Time(s) |
|
| Description: |
|
| Filesize: |
39.97 KB |
| Viewed: |
2735 Time(s) |
|
|
|
| Back to top |
|
 |
TsTg
Master Cheater
 Reputation: 5 Reputation: 5
Joined: 12 Dec 2012
Posts: 340
Location: Somewhere....
|
 Posted: Mon Apr 11, 2022 2:45 pm Post subject: Posted: Mon Apr 11, 2022 2:45 pm Post subject: |
 |
|
hmm so it is Themida protected, and that is a complex one that uses the virtualization technique, it can be "de-virtualized" but its far from being a easy task as far as i know, there are some tools that might be released one day for that, please have a look at this page https://ieeexplore.ieee.org/document/9139515 where it explains how such protectors work.
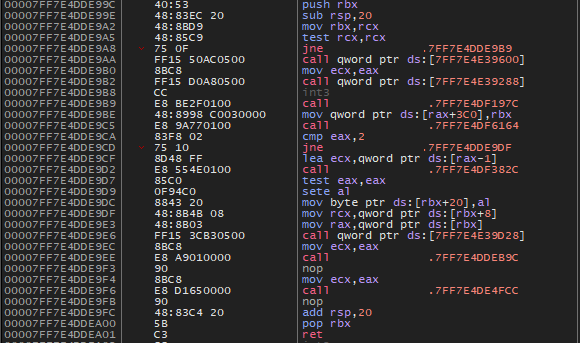
| Quote: | | The code from the picture is showing the location where I got redirected when did "Step Out" / from callstack (the createThread lpStartAddress is diffrent address, forwarding to "normal", easier function). |
can you post a picture showing how that normal code area look like ?
|
|
| Back to top |
|
 |
Bedopies
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 25 Feb 2019
Posts: 13
|
 Posted: Mon Apr 11, 2022 3:35 pm Post subject: Posted: Mon Apr 11, 2022 3:35 pm Post subject: |
 |
|
What do You think? Its packed or it's virtualized?
I picked this one (I mean target) because:
- I want to learn something more (First time I saw ObRegisterCallback),
- I want to know how this thing is working
Example function at lpStartAddress argument what at least looks normal (attachment, I censored "target name" just in case lol)
| Description: |
|
| Filesize: |
30.44 KB |
| Viewed: |
2699 Time(s) |
|
|
|
| Back to top |
|
 |
TsTg
Master Cheater
 Reputation: 5 Reputation: 5
Joined: 12 Dec 2012
Posts: 340
Location: Somewhere....
|
 Posted: Tue Apr 12, 2022 3:14 pm Post subject: Posted: Tue Apr 12, 2022 3:14 pm Post subject: |
 |
|
looks somewhat clean routine for sure (except for the int3 above, probably moves to a handler that do some checks, etc), it could be a simple packing, it could be also have some virtualization on some pieces of the code, cant tell unless you have a look at the entire file...
it may not be possible to fully unpack it, but i believe there is a way you can inline-patch it, as far as i know, you need to make a proper entrypoint after the anti-debug stuff was done, find some checksum values to bypass the crc checks.
|
|
| Back to top |
|
 |
|

 Reputation: 5
Reputation: 5 Reputation: 5
Reputation: 5 Reputation: 5
Reputation: 5 Reputation: 5
Reputation: 5






