 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
KevinD
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 15 Apr 2020
Posts: 39
|
 Posted: Wed Jul 15, 2020 6:11 am Post subject: WriteProcessMemory pointer C ++ 64 bits ? Posted: Wed Jul 15, 2020 6:11 am Post subject: WriteProcessMemory pointer C ++ 64 bits ? |
 |
|
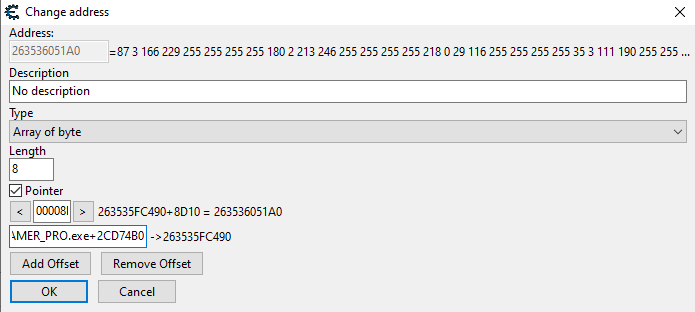
Hello, I would like to know how we can recover a pointer address in C ++ (64 bits)?
In order to change a value with WriteProcessMemory.
example my baseadress = base;
WriteProcessMemory (hProc, (LPVOID) (((uint8_t *) base) + ?????, & array, number_BYTE, NULL);
| Description: |
|
| Filesize: |
104.89 KB |
| Viewed: |
2256 Time(s) |
|
|
|
| Back to top |
|
 |
DanyDollaro
Master Cheater
![]() Reputation: 3 Reputation: 3
Joined: 01 Aug 2019
Posts: 334
|
 Posted: Mon Jul 27, 2020 8:48 am Post subject: Posted: Mon Jul 27, 2020 8:48 am Post subject: |
 |
|
First you need to get the base address of the module, there are various functions that you can use, you can just google "C++ get module base address".
Then if you know how a pointer works you will have no problem adding offsets.
|
|
| Back to top |
|
 |
JohnathanSweeney
Newbie cheater
![]() Reputation: 1 Reputation: 1
Joined: 04 Apr 2016
Posts: 20
|
 Posted: Thu Aug 06, 2020 9:02 pm Post subject: Posted: Thu Aug 06, 2020 9:02 pm Post subject: |
 |
|
This is x64 compatible, as an example I made it read and write to a integer using the pointer you showed a screenshot of
| Code: |
#include <iostream>
#include <vector>
#include <Windows.h>
DWORD GetProcId(const wchar_t* procName)
{
DWORD procId = 0;
HANDLE hSnap = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, 0);
if (hSnap != INVALID_HANDLE_VALUE)
{
PROCESSENTRY32 procEntry;
procEntry.dwSize = sizeof(procEntry);
if (Process32First(hSnap, &procEntry))
{
do
{
if (!_wcsicmp(procEntry.szExeFile, procName))
{
procId = procEntry.th32ProcessID;
break;
}
} while (Process32Next(hSnap, &procEntry));
}
}
CloseHandle(hSnap);
return procId;
}
uintptr_t GetModuleBaseAddress(DWORD procId, const wchar_t* modName)
{
uintptr_t modBaseAddr = 0;
HANDLE hSnap = CreateToolhelp32Snapshot(TH32CS_SNAPMODULE | TH32CS_SNAPMODULE32, procId);
if (hSnap != INVALID_HANDLE_VALUE)
{
MODULEENTRY32 modEntry;
modEntry.dwSize = sizeof(modEntry);
if (Module32First(hSnap, &modEntry))
{
do
{
if (!_wcsicmp(modEntry.szModule, modName))
{
modBaseAddr = (uintptr_t)modEntry.modBaseAddr;
break;
}
} while (Module32Next(hSnap, &modEntry));
}
}
CloseHandle(hSnap);
return modBaseAddr;
}
|
This is pasted from a tutorial on www.guidedhacking.com
| Code: |
uintptr_t FindDMAAddy(HANDLE hProc, uintptr_t ptr, std::vector<unsigned int> offsets)
{
uintptr_t addr = ptr;
for (unsigned int i = 0; i < offsets.size(); ++i)
{
ReadProcessMemory(hProc, (BYTE*)addr, &addr, sizeof(addr), 0);
addr += offsets[i];
}
return addr;
}
int main()
{
//Get ProcId of the target process
DWORD procId = GetProcId(L"GAMER_PRO.exe");
//Getmodulebaseaddress
uintptr_t moduleBase = GetModuleBaseAddress(procId, L"GAMER_PRO.exe");
//Get Handle to Process
HANDLE hProcess = 0;
hProcess = OpenProcess(PROCESS_ALL_ACCESS, NULL, procId);
//Resolve base address of the pointer chain
uintptr_t dynamicPtrBaseAddr = moduleBase + 0x2CD74B0;
std::cout << "DynamicPtrBaseAddr = " << "0x" << std::hex << dynamicPtrBaseAddr << std::endl;
//Resolve our pointer chain
uintptr_t Addr = FindDMAAddy(hProcess, dynamicPtrBaseAddr, { 0x8D10 });
std::cout << "Addr = " << "0x" << std::hex << Addr << std::endl;
//Read value
int oldValue = 0;
ReadProcessMemory(hProcess, (BYTE*)Addr, &oldValue, sizeof(oldValue), nullptr);
std::cout << "Curent value = " << std::dec << oldValue << std::endl;
//Write to it
int newValue = 1337;
WriteProcessMemory(hProcess, (BYTE*)Addr, &newValue, sizeof(newValue), nullptr);
//Read out again
ReadProcessMemory(hProcess, (BYTE*)Addr, &oldValue, sizeof(oldValue), nullptr);
std::cout << "New value = " << std::dec << oldValue << std::endl;
getchar();
return 0;
}
|
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|



