| View previous topic :: View next topic |
| Author |
Message |
LongBeardedLion
Expert Cheater
![]() Reputation: 0 Reputation: 0
Joined: 10 Apr 2020
Posts: 174
|
 Posted: Thu Jun 25, 2020 4:42 am Post subject: .rdata address at the root of a sequence of functions Posted: Thu Jun 25, 2020 4:42 am Post subject: .rdata address at the root of a sequence of functions |
 |
|
Images below
Since my hacks are not working properly, i have been on a journey trying to get to the very root of the sequence of functions.
So i have a few questions for this.
1- The reason im doing this is because i dont know of any other possible solution to make my hacks work.
So my idea is to get to the first function in the sequence, where the values that i want to change are first used and passed to later functions.
So im sure that the values that im using will be passed into all the processes that are needed and written into every place in memory and passed into every function that is needed.
Is this the right way to do this? Pls tell me.
Because this that im doing is different than just changing a value.
Im reverse engineering many functions. A lot of trial and error.
Calling function after function and testing to see if it works.
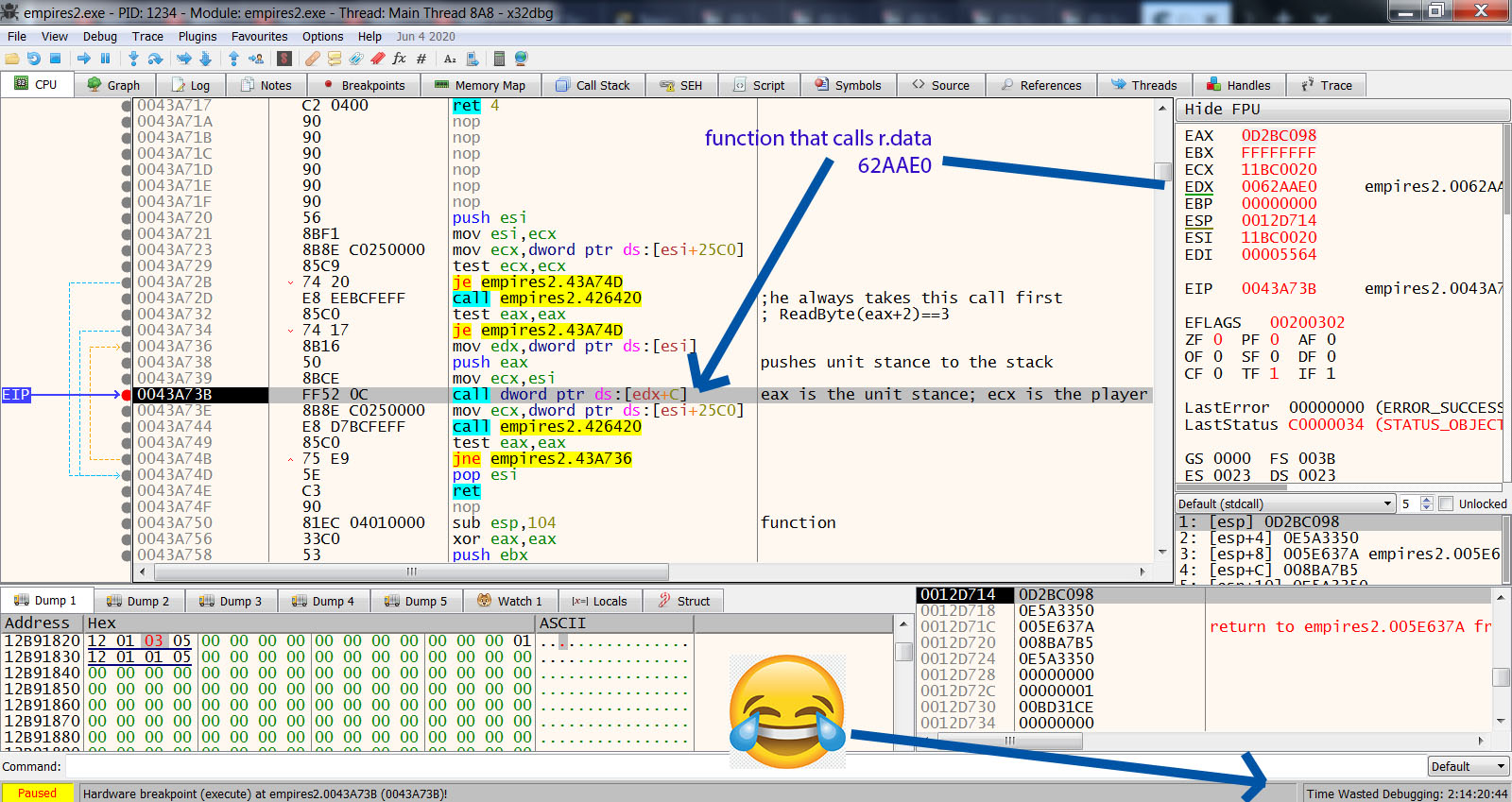
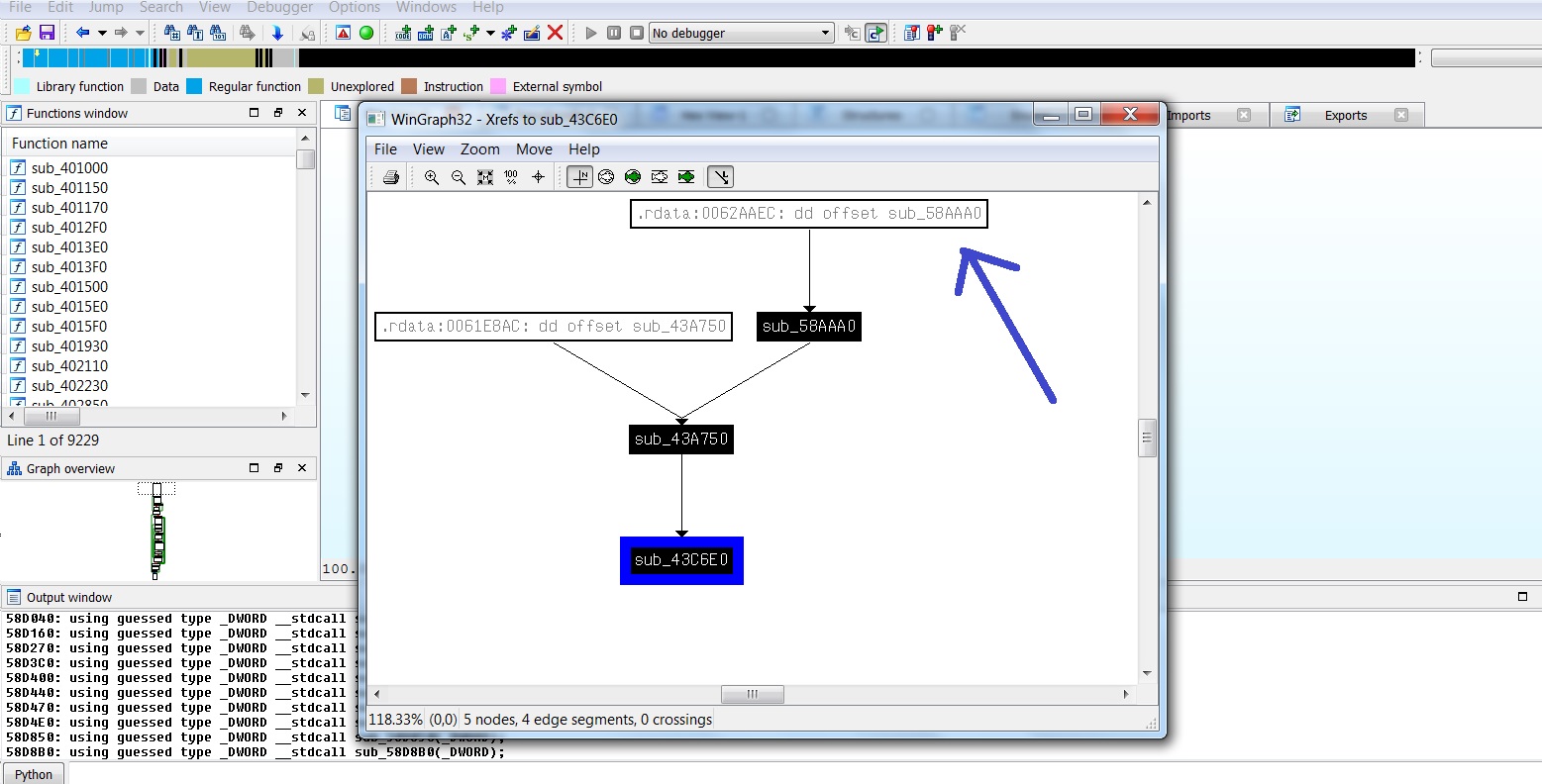
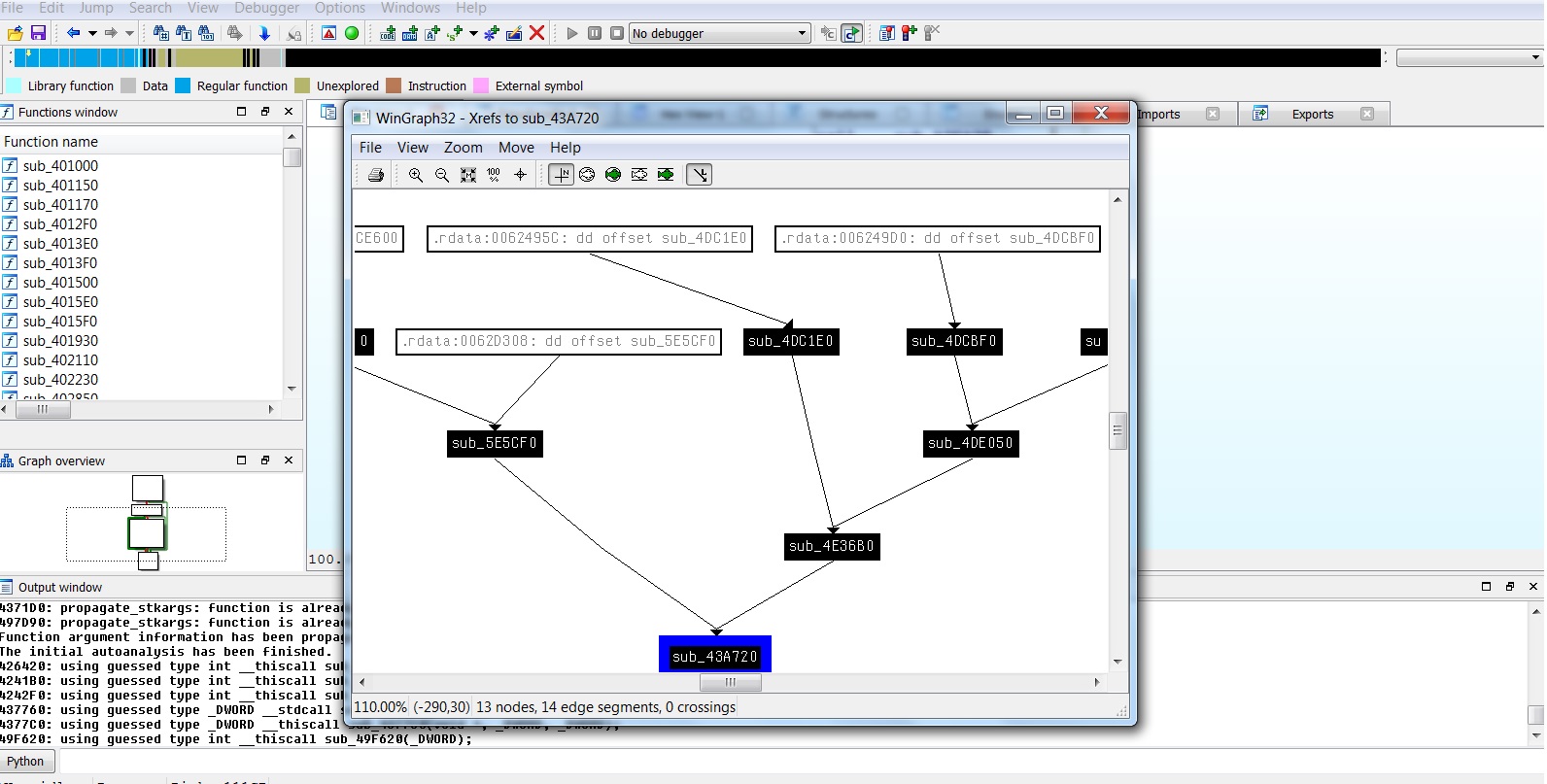
2- At the bottom of the sequence of functions there is always these .rdata addresses.
I was told in another post these are "Vtables". But that wasnt very clear. I made some research and found that Vtables can be hacked, and are basically addresses that call functions. So should i hack the Vtable? Or should i call the function that is called after the Vtable? Or the function before?
From the example below in the image xreftofunction.jpg, you can see that at the root of the sequence of functions right before sub 58AAA0, there is the .rdata 62AAEC.
Thats the Vtable that is called this way : Call dword [edx+c] Where edx is 62AAEC. Thats so cool.
3- Should i keep digging back? Because what im trying to do is basically change a stance of a unit. So its almost like mimicking the press of a button.
Or the commands that are triggered by it. So perhaps i need to go back enough in "time" until im close to the moment where the button is pressed and things start happening.
The more i go back the more things get harder. With complex loops that tick every second. And that call other functions that also loop.
| Description: |
|
| Filesize: |
425.27 KB |
| Viewed: |
2594 Time(s) |
|
| Description: |
|
| Filesize: |
261.87 KB |
| Viewed: |
2594 Time(s) |
|
| Description: |
|
| Filesize: |
286.1 KB |
| Viewed: |
2594 Time(s) |
|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4722
|
 Posted: Thu Jun 25, 2020 10:36 am Post subject: Posted: Thu Jun 25, 2020 10:36 am Post subject: |
 |
|
You should also look out for accesses to static data. Like arguments sent to functions, static data may need to be set correctly in order for the function to work correctly.
An object's vtable (if it has one) is a pointer typically stored as the first member of the object that points to an array of function pointers. This array is pointed to by the vtable of every object of that particular class. Look up "virtual function" in C++ for a high level overview.
How exactly are you calling the function? More specifically have you determined why is it crashing when you call it?
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
LongBeardedLion
Expert Cheater
![]() Reputation: 0 Reputation: 0
Joined: 10 Apr 2020
Posts: 174
|
 Posted: Thu Jun 25, 2020 2:18 pm Post subject: Posted: Thu Jun 25, 2020 2:18 pm Post subject: |
 |
|
Thank you parkour penguin i hope you are having a good day.
>static data
You mean static data as values that are passed into a function in other registers other than the ecx and the stack (in case its a __thiscall)?
I look for the value that is being passed. Get the pointer. And then use readprocessmemory to get that value into the argument before calling the function. Works most cases. Is that what you mean? Or something more complex?
I went to the point of calling the function and making sure every value in the stack and all the registers were the mimicking the same values taken by the right addresses at that point. I dont know if this is overdoing it or if for some reason is wrong. But it works in many cases.
As for why it crashes? I think it crashes because as it was suggested here in the past, there might be one value being passed somewhere that is off, and that causes the whole thing to fall a part. Because its my units stance (defence position, attack position), its not a value like gold. So the original sequence of the functions should start with a key, (a for attack stance) (d for defense stance), and then it goes through many functions and loops that all do something on the memory.
At some point i got to where the getAsyncKeyState is. But it seems its a loop that check for the keys that are being pressed and it only triggers an action if it detects after some ammount of time. (It had a call to a function named timeGetTime). But it was very obscure. And very hard to understand what is going to be called and after what.
So i stopped studying that part after 3 days working on it without much results. Perhaps in the future i will go back to that.
Instead im in 58AAA0 that is a function that is almost at the root, and its the stance, not just a key detection bunch of loops and function calls.
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4722
|
 Posted: Thu Jun 25, 2020 3:47 pm Post subject: Posted: Thu Jun 25, 2020 3:47 pm Post subject: |
 |
|
| LongBeardedLion wrote: | | You mean static data as values that are passed into a function in other registers other than the ecx and the stack (in case its a __thiscall)? |
No, I mean stuff that's stored in the exe. e.g. mov eax,[game.exe+1234].
| LongBeardedLion wrote: | | I dont know if this is overdoing it or if for some reason is wrong. |
It's a good approach if you want to try to get lucky and finish it quickly, but it would be better if you actually knew what the function was doing.
| LongBeardedLion wrote: | | As for why it crashes? I think... |
Don't make assumptions when debugging. Actually figure out where and why it's crashing.
If you want my guess, at least one problem is that the code you wrote to call it is wrong. e.g. not cleaning up the stack correctly, modifying a nonvolatile register without restoring it, deallocating memory in use, etc.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
Banjo Patterson
Cheater
![]() Reputation: 1 Reputation: 1
Joined: 15 May 2018
Posts: 36
|
 Posted: Thu Jun 25, 2020 9:01 pm Post subject: Posted: Thu Jun 25, 2020 9:01 pm Post subject: |
 |
|
In AoE2 most commands are dispatched with a command buffer which contains the contents of the command (starting with command ID then data related to the command).
A pointer to the command buffer is usually in the stack for any function which deals with the command, and if you use CE to scan the stack memory for the earliest record of that pointer, you can begin to locate the earliest function in the function path.
If you want to talk more, PM me your discord.
|
|
| Back to top |
|
 |
|

 Reputation: 152
Reputation: 152 Reputation: 152
Reputation: 152



