 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
fraxe
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 06 May 2020
Posts: 2
|
 Posted: Wed May 06, 2020 5:14 am Post subject: issues with finding function in memory Posted: Wed May 06, 2020 5:14 am Post subject: issues with finding function in memory |
 |
|
Hi there, i am not very experienced in reverse engineering and unfortunately i encountered blocking problem with finding function in memory.
For now i can't post links, so i mentioned attachment name where it should be placed.
Maybe i will reproduce my steps below, i will appreciate some kind of code review if the steps are correct.
The goal is find a function that performs attacking player.
1. i found address with currently attacked player id
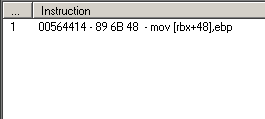
2. next using "find out what writes to this address" i found one instruction (attachment 2)
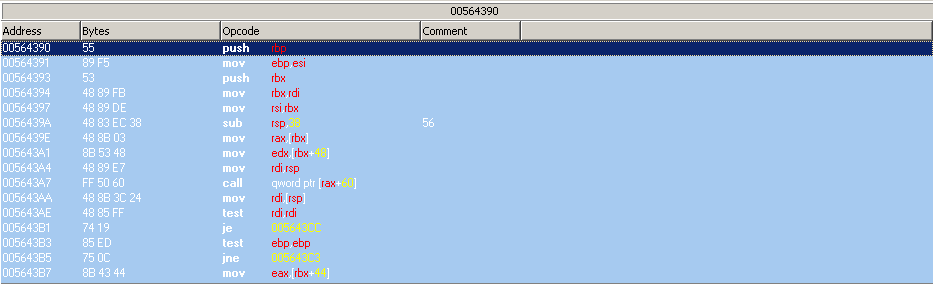
3. after that, using "select current function" in disassembler i got function starting like that (attachment 3)
Now, i assume that 00564390 is address of my function, am i correct?
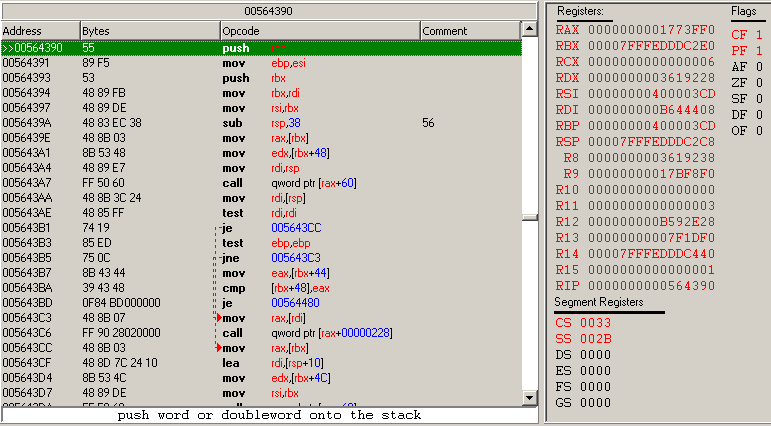
Next, basing on Dark Byte answer below i tried to set breakpoint on function start and find out what are the arguments of this functions, but in RSP i have kinda unclear values, i don't know where is the limit where arguments stop. (attachment arguments)
| Dark Byte wrote: | at the entrypoint [ESP+4] contains the parameter
If you're inside the function body (after the header) then the parameter will be in [EBP+8]
Easiest method is just checking the stackview and optional stackview->stacktrace to see the parameters, and the functions that called that function and their parameters |
Stacktrace shows value only in "full stack" mode, otherwise is empty, here is RSP on breakpoint in predicted function start. (attachment rsp)
Could anyone check if my steps are correct? I will appreciate any advice.
Best regards!
| Description: |
|
| Filesize: |
1.05 KB |
| Viewed: |
1152 Time(s) |
|
| Description: |
|
| Filesize: |
7.82 KB |
| Viewed: |
1152 Time(s) |
|
| Description: |
|
| Filesize: |
17.32 KB |
| Viewed: |
1152 Time(s) |
|
| Description: |
|
| Filesize: |
6.51 KB |
| Viewed: |
1152 Time(s) |

|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4722
|
 Posted: Wed May 06, 2020 10:56 am Post subject: Posted: Wed May 06, 2020 10:56 am Post subject: |
 |
|
In 32-bit code, arguments are passed through the stack.
In 64-bit code, the first 4 arguments are passed through rcx, rdx, r8, and r9 respectively, and then any extras are passed through the stack.
But all that seems pointless since that function isn't conforming to standard calling conventions (or that's not actually the start of the function).
I'd go to the current return address of the stack (7F1E5C) and see what's going on there. i.e. check if it even is code (if not -> probably not actual start of the function), and if so, see what it's doing around the call.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
fraxe
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 06 May 2020
Posts: 2
|
 Posted: Sat May 09, 2020 8:36 am Post subject: Posted: Sat May 09, 2020 8:36 am Post subject: |
 |
|
| @ParkourPenguin, thank you very much for reply, I'll try to investigate correct address to this function.
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 152
Reputation: 152




