 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
Midnightesc
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 12 Jun 2006
Posts: 13
|
 Posted: Fri Jul 12, 2013 7:45 am Post subject: simple AA script qn Posted: Fri Jul 12, 2013 7:45 am Post subject: simple AA script qn |
 |
|
hi,
how do i assign the value in a register (e.g. EDI) to a symbol?
given that for eg i did an aobscan and found the code i wanted:
add [edi+0000005C],eax // edi having value of 05B002FC at that point
now, the address of the actual item i wanted is stored @ the address of : edi+0000005C
how do i assign that to a label/symbol so that i can reference and add it directly to the cheat tables?
i've tried:
| Code: |
registersymbol(aob2_pointer)
alloc(aob2_pointer,4)
aobscan(aob_result, 00 11 22 33 44 55) //eg byte string, this points to add [edi+0000005C],eax
aob_result:
mov [aob2_pointer], edi // so aob2_pointer should hold value of [u]05B002FC[/u]
add [aob2_pointer], 0000005C // so aob2_pointer should hold 05B002FC + 5c = 5B00358 <-- this is the address i want aob2_pointer to be when i add it in the cheat table
|
but it doesn't work. any suggestions?
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 471 Reputation: 471
Joined: 09 May 2003
Posts: 25839
Location: The netherlands
|
 Posted: Fri Jul 12, 2013 8:09 am Post subject: Posted: Fri Jul 12, 2013 8:09 am Post subject: |
 |
|
make sure that instruction is only accessed by the thing you need (e.g health tends to be used by both player and enemies)
Also, allocate memory for your code injection since I doubt there is enough space in the code for those instructions AND the original code. (Tip: use the code injection template)
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
Midnightesc
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 12 Jun 2006
Posts: 13
|
 Posted: Fri Jul 12, 2013 8:25 am Post subject: Posted: Fri Jul 12, 2013 8:25 am Post subject: |
 |
|
| Dark Byte wrote: | make sure that instruction is only accessed by the thing you need (e.g health tends to be used by both player and enemies)
Also, allocate memory for your code injection since I doubt there is enough space in the code for those instructions AND the original code. (Tip: use the code injection template) |
thanks for the reply. well, first of all that instruction is only accessed by 1 function (it's a counter),
and even if i tried it with only the | Code: | | mov [aob2_pointer], edi |
(this and the ori instructions are both 6 bytes) it still didnt work. i couldn't get the value of edi in the symbol aob2_pointer
*edit* scratch that.. i figured that out.
thanks!
|
|
| Back to top |
|
 |
jgoemat
Master Cheater
![]() Reputation: 23 Reputation: 23
Joined: 25 Sep 2011
Posts: 264
|
 Posted: Sat Jul 13, 2013 8:48 pm Post subject: Re: simple AA script qn Posted: Sat Jul 13, 2013 8:48 pm Post subject: Re: simple AA script qn |
 |
|
| Midnightesc wrote: | hi,
| Code: |
registersymbol(aob2_pointer)
alloc(aob2_pointer,4)
aobscan(aob_result, 00 11 22 33 44 55) //eg byte string, this points to add [edi+0000005C],eax
aob_result:
mov [aob2_pointer], edi // so aob2_pointer should hold value of [u]05B002FC[/u]
add [aob2_pointer], 0000005C // so aob2_pointer should hold 05B002FC + 5c = 5B00358 <-- this is the address i want aob2_pointer to be when i add it in the cheat table
|
|
I'm really surprised your code doesn't crash your game. Check out my videos http://www.youtube.com/watch?v=_gTflwQr5ew and http://www.youtube.com/watch?v=V-aa21OlSQE
First, doing the aobscan will get you the first result, there could be more than one. Scan for your bytes using CE to make sure you only get one, if not then you could be over-writing the wrong instruction.
Second, you are writing your instructions over that instruction, but that instruction is not long enough. You want to use the code injection template. Find the exact instruction you want to use. mov [edi+00005c],eax is only 3 bytes, your two instructions are 13 bytes so you are overwriting 10 extra bytes of gamem code. Find the location of the code in memory viewer and it CTRL+A to open auto-assembler, then use the template menu 'Cheat table framework code' and then 'Code injection'. This allocates memory at 'newmem' and replaes the instruction (and probably one after) with a jmp to your new memory. Your code still needs to perform the original add if you don't want to skip it.
Third, is aob2_pointer pointing to your new memory? I'm not sure, but I put the registersymbol AFTER it gets set, you could be registering the default of 0 for the value of the symbol...
Fourth, add alters flags so you probably want to pushfd before and popfd after to restore their state (Modifies Flags: AF CF OF PF SF ZF) in case that state is used by the game.
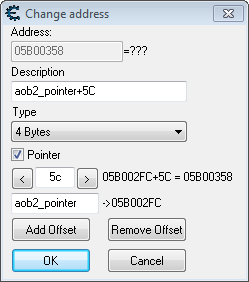
Lastly you don't really need the add, you can use a pointer. When editing the table entry, check 'pointer' at the bottom and put the address that contains a pointer in the space and you can enter offsets (see attached image)
| Code: |
alloc(newmem,$1000)
alloc(aob2_pointer,4)
registersymbol(aob2_pointer)
aobscan(aob_result,00 11 22 33 44 55) // really 6 bytes?
label(return)
newmem:
mov [aob2_pointer],edi
add [edi+0000005C],eax // original code
jmp return
aob_result:
jmp newmem // 5 bytes
nop // 1 byte
return:
|
| Description: |
|
| Filesize: |
8.13 KB |
| Viewed: |
2649 Time(s) |
|
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 471
Reputation: 471

