darknight1601
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 05 Oct 2009
Posts: 6
|
 Posted: Mon Oct 05, 2009 7:12 am Post subject: Help with making a Trainer(Mod) Posted: Mon Oct 05, 2009 7:12 am Post subject: Help with making a Trainer(Mod) |
 |
|
1st thing i m new here so if i m posting it in wrong section pls move it to proper place thx
Ok i m creating a trainer to just see a value of a address
I not need edit it
Neither i need to freeze it
I just have to see it
I used cheat engine and found the address and its a pointer value like
| Code: |
game.exe+003E207C
F4 (offset)
194(offset)
Address to read.
|
*Offset are in HEX
The final address in a Integer 4 bytes
now mostly i used inbuilt trainer maker in cheat engine which was quite easy. but i didn't found anyway to see the value of this address through that inbuilt trainer maker.
so i looked around and found TMK(trainer maker kit)
nice tool so easy nope things after u use Tsearch but i don't know how to read this address in TMK too
I also found Game trainer studio
good tool with this i can see the value of address but i have no idea how to put this game.exe+003E207C there.
i tried to simply put game.exe with the pointer which didn't worked lol
So i ended up with designing my own trainer with VB6
I tried solving my problem with this tutorial
tut-making-trainer-vb which i found on mpgh(I can't post url to that link)
*In that post module maker is UMM by phenix
I used my portable version of VB6
I downloaded VB.net Undetected module maker by phenix
after this i followed there steps and as soon as i added that module it shows so many errors lol
here is the code what i got from UMM for my 1st module if u find problem understanding it look at the bottom of the post thank you
| Code: |
Private Declare Function XLIPYKQLGY Lib "kernel32" Alias "OpenProcess" (ByVal dwDesiredAccess As Integer, ByVal bInheritHandle As Integer, ByVal dwProcessId As Integer) As Integer
Private Declare Function MAHALTSYZG Lib "kernel32" Alias "WriteProcessMemory" (ByVal hProcess As Integer, ByVal lpBaseAddress As Integer, ByRef lpBuffer As Integer, ByVal nSize As Integer, ByRef lpNumberOfBytesWritten As Integer) As Integer
Private Declare Function ZEKRRGDBGQ Lib "kernel32" Alias "WriteProcessMemory" (ByVal hProcess As Integer, ByVal lpBaseAddress As Integer, ByRef lpBuffer As Single, ByVal nSize As Integer, ByRef lpNumberOfBytesWritten As Integer) As Integer
Private Declare Function GROIDZGUIZ Lib "kernel32" Alias "ReadProcessMemory" (ByVal hProcess As IntPtr, ByVal lpBaseAddress As IntPtr, ByRef buffer As Single, ByVal size As Int32, ByRef lpNumberOfBytesRead As Int32) As Boolean
Private Declare Function KXMXYVMZUJ Lib "kernel32" Alias "ReadProcessMemory" (ByVal hProcess As Integer, ByVal lpBaseAddress As Integer, ByRef lpBuffer As Integer, ByVal nSize As Integer, ByRef lpNumberOfBytesWritten As Integer) As Integer
Private Declare Function BBGDKEZBMT Lib "kernel32" Alias "CloseHandle" (ByVal hObject As Integer) As Integer
Public Declare Function WJXRUJZJDC Lib "user32" Alias "GetAsyncKeyState" (ByVal vKey As Long) As Integer
Public FOLUUBHNAM As Long
Public RWXFTODXXW As Single
Public QDFHJPGEZF As Integer
'WriteMemory
Public Function HLHGNYENGP(ByVal MCGIITKYLQ As Integer, ByVal DKIHMCIHSA As Long, ByVal XVIOPITWZJ As Integer)
Dim IRJCTXVTAM As Process() = Process.GetProcessesByName("game")
If IRJCTXVTAM.Length = 0 Then
End
End If
Dim EUTWKBKUCW As IntPtr = XLIPYKQLGY(&H1F0FFF, 0, IRJCTXVTAM(0).Id)
MAHALTSYZG(EUTWKBKUCW, MCGIITKYLQ, DKIHMCIHSA, XVIOPITWZJ, Nothing)
BBGDKEZBMT (EUTWKBKUCW)
End Function
'ReadFloat
Public Function HOGOKYWNSZ(ByVal MCGIITKYLQ As Single)
Dim IRJCTXVTAM As Process() = Process.GetProcessesByName("game")
If IRJCTXVTAM.Length = 0 Then
End
End If
Dim EUTWKBKUCW As IntPtr = XLIPYKQLGY(&H1F0FFF, 0, IRJCTXVTAM(0).Id)
KXMXYVMZUJ(EUTWKBKUCW, MCGIITKYLQ, FOLUUBHNAM, 4, Nothing)
BBGDKEZBMT (EUTWKBKUCW)
Return FOLUUBHNAM
End Function
'WriteFloat
Public Function LTEEFUBSEJ(ByVal MCGIITKYLQ As Integer, ByVal DKIHMCIHSA As Single)
Dim IRJCTXVTAM As Process() = Process.GetProcessesByName("game")
If IRJCTXVTAM.Length = 0 Then
End
End If
Dim EUTWKBKUCW As IntPtr = XLIPYKQLGY(&H1F0FFF, 0, IRJCTXVTAM(0).Id)
ZEKRRGDBGQ(EUTWKBKUCW, MCGIITKYLQ, DKIHMCIHSA, 4, Nothing)
BBGDKEZBMT (EUTWKBKUCW)
End Function
'ReadLong
Public Function CXXKRDOUWT(ByVal MCGIITKYLQ As Integer)
Dim IRJCTXVTAM As Process() = Process.GetProcessesByName("game")
If IRJCTXVTAM.Length = 0 Then
End
End If
Dim EUTWKBKUCW As IntPtr = XLIPYKQLGY(&H1F0FFF, 0, IRJCTXVTAM(0).Id)
KXMXYVMZUJ(EUTWKBKUCW, MCGIITKYLQ, FOLUUBHNAM, 4, Nothing)
BBGDKEZBMT (EUTWKBKUCW)
Return FOLUUBHNAM
End Function
'ReadFloatPointer
Public Function XFPXBIOCOD(ByVal FFELIAMHMS As Integer, ByVal KHTHKWHFID As Short)
Dim NWYGSSHRJH As Long
Dim IRJCTXVTAM As Process() = Process.GetProcessesByName("game")
If IRJCTXVTAM.Length = 0 Then
End
End If
Dim EUTWKBKUCW As IntPtr = XLIPYKQLGY(&H1F0FFF, 0, IRJCTXVTAM(0).Id)
KXMXYVMZUJ(EUTWKBKUCW, FFELIAMHMS, FOLUUBHNAM, 4, Nothing)
NWYGSSHRJH = FOLUUBHNAM + KHTHKWHFID
GROIDZGUIZ(EUTWKBKUCW, NWYGSSHRJH, RWXFTODXXW, 4, Nothing)
Return RWXFTODXXW
BBGDKEZBMT (EUTWKBKUCW)
End Function
'ReadLongPointer
Public Function FKDBCAWGKN(ByVal FFELIAMHMS As Integer, ByVal KHTHKWHFID As Short, ByVal XVIOPITWZJ As Integer)
Dim NWYGSSHRJH As Long
Dim IRJCTXVTAM As Process() = Process.GetProcessesByName("game")
If IRJCTXVTAM.Length = 0 Then
End
End If
Dim EUTWKBKUCW As IntPtr = XLIPYKQLGY(&H1F0FFF, 0, IRJCTXVTAM(0).Id)
KXMXYVMZUJ(EUTWKBKUCW, FFELIAMHMS, FOLUUBHNAM, 4, Nothing)
NWYGSSHRJH = FOLUUBHNAM + KHTHKWHFID
KXMXYVMZUJ(EUTWKBKUCW, NWYGSSHRJH, QDFHJPGEZF, XVIOPITWZJ, Nothing)
Return QDFHJPGEZF
BBGDKEZBMT (EUTWKBKUCW)
End Function
'WriteFloatPointer
Public Function RSPMBOSQHW(ByVal FFELIAMHMS As Integer, ByVal KHTHKWHFID As Short, ByVal DKIHMCIHSA As Single)
Dim NWYGSSHRJH As Long
Dim IRJCTXVTAM As Process() = Process.GetProcessesByName("game")
If IRJCTXVTAM.Length = 0 Then
End
End If
Dim EUTWKBKUCW As IntPtr = XLIPYKQLGY(&H1F0FFF, 0, IRJCTXVTAM(0).Id)
KXMXYVMZUJ(EUTWKBKUCW, FFELIAMHMS, FOLUUBHNAM, 4, Nothing)
NWYGSSHRJH = FOLUUBHNAM + KHTHKWHFID
ZEKRRGDBGQ(EUTWKBKUCW, NWYGSSHRJH, DKIHMCIHSA, 4, Nothing)
BBGDKEZBMT (EUTWKBKUCW)
End Function
'WriteLongPointer
Public Function RZXOQOVXJG(ByVal FFELIAMHMS As Integer, ByVal KHTHKWHFID As Short, ByVal DKIHMCIHSA As Long, ByVal XVIOPITWZJ As Integer)
Dim NWYGSSHRJH As Long
Dim IRJCTXVTAM As Process() = Process.GetProcessesByName("game")
If IRJCTXVTAM.Length = 0 Then
End
End If
Dim EUTWKBKUCW As IntPtr = XLIPYKQLGY(&H1F0FFF, 0, IRJCTXVTAM(0).Id)
KXMXYVMZUJ(EUTWKBKUCW, FFELIAMHMS, FOLUUBHNAM, 4, Nothing)
NWYGSSHRJH = FOLUUBHNAM + KHTHKWHFID
MAHALTSYZG(EUTWKBKUCW, NWYGSSHRJH, DKIHMCIHSA, XVIOPITWZJ, Nothing)
BBGDKEZBMT (EUTWKBKUCW)
End Function
'NOP
Public Function UJCXELLJLP(ByVal MCGIITKYLQ As Integer, ByVal DKIHMCIHSA As Integer)
Dim IRJCTXVTAM As Process() = Process.GetProcessesByName("game")
If IRJCTXVTAM.Length = 0 Then
End
End If
Dim EUTWKBKUCW As IntPtr = XLIPYKQLGY(&H1F0FFF, 0, IRJCTXVTAM(0).Id)
MAHALTSYZG(EUTWKBKUCW, MCGIITKYLQ, DKIHMCIHSA, 1, Nothing)
BBGDKEZBMT (EUTWKBKUCW)
End Function
|
It have so many red lines lol
anyway i left it as it was and i made my 2nd module
In 2nd module the gaved me code which was
| Code: |
'readdll
Public Function readdll(ByVal modulename As String)
Dim procmodule As ProcessModule
Dim constant1 As Integer
Dim constant2 As Long
Dim constant3 As Process() = Process.GetProcessesByName("WarRock")
If constant3.Length = 0 Then
Return 0
End If
For Each procmodule In constant3(0).Modules
If modulename = procmodule.ModuleName Then
constant1 = procmodule.BaseAddress
End If
Next
constant2 = constant1
Return constant2
End Function |
but problem was it was for dll not exe
so changed dll to exe i don't know i did write or wrong
and code became
| Code: |
'readexe
Public Function readexe(ByVal modulename As String)
Dim procmodule As ProcessModule
Dim constant1 As Integer
Dim constant2 As Long
Dim constant3 As Process() = Process.GetProcessesByName("game")
If constant3.Length = 0 Then
Return 0
End If
For Each procmodule In constant3(0).Modules
If modulename = procmodule.modulename Then
constant1 = procmodule.BaseAddress
End If
Next
constant2 = constant1
Return constant2
End Function
|
It shown me error too in these lines
Dim constant3 As Process() = Process.GetProcessesByName("game")
Return 0
Return constant2
after this all
i made a text box and puted this code in it hoping it all work
| Code: |
Dim string1 As Long
Dim string2 As Integer
Dim string3 As Integer
string1 = readexe("ozld.exe")
string2 = "&H" + Hex(string1 + &H3E207C)
string3 = ReadLongPointer(string2, &HF4, 4, Nothing)
TextBox1.Text = ReadLongPointer(string3, &H194, 4, Nothing)
|
after this when i tried to compile of course 1st error was in 4th line 4m top in module 1st which i got 4m UMM
| Code: |
Private Declare Function GROIDZGUIZ Lib "kernel32" Alias "ReadProcessMemory" (ByVal hProcess As IntPtr, ByVal lpBaseAddress As IntPtr, ByRef buffer As Single, ByVal size As Int32, ByRef lpNumberOfBytesRead As Int32) As Boolean
|
and error was user-defined type not defined
So this was all
I don't know much about VB so can't tell wat wrong i m doing
game.exe+003E207C
also i wasn't able to find any tutorial to find how to put this
in Game trainer studio or TMK too.
All i want to see the value of that address in a little window on my desktop while i play my game. also if possible i want this trainer to be undetectable too.
Coz its not freezing or changing the value of address i don't think game sud have problem with this but still if possible i want to keep it undetectable.
Can any one help me with this?
*MODDED
sorry i show u the original code which UMM filles with obsulute value
i also attaching a pic of UMM coz i can't post pic too:(
anyway in pic u can see UMM in left hand got blank boxes which gets filled with random values when i press genrate fast module.
and this is original code which i think it filles with crap values
| Code: |
Private Declare Function OpenProcess Lib "kernel32" Alias "OpenProcess" (ByVal dwDesiredAccess As Integer, ByVal bInheritHandle As Integer, ByVal dwProcessId As Integer) As Integer
Private Declare Function WriteProcessMemory Lib "kernel32" Alias "WriteProcessMemory" (ByVal hProcess As Integer, ByVal lpBaseAddress As Integer, ByRef lpBuffer As Integer, ByVal nSize As Integer, ByRef lpNumberOfBytesWritten As Integer) As Integer
Private Declare Function WriteFloatMemory Lib "kernel32" Alias "WriteProcessMemory" (ByVal hProcess As Integer, ByVal lpBaseAddress As Integer, ByRef lpBuffer As Single, ByVal nSize As Integer, ByRef lpNumberOfBytesWritten As Integer) As Integer
Private Declare Function ReadFloat Lib "kernel32" Alias "ReadProcessMemory" (ByVal hProcess As IntPtr, ByVal lpBaseAddress As IntPtr, ByRef buffer As Single, ByVal size As Int32, ByRef lpNumberOfBytesRead As Int32) As Boolean
Private Declare Function ReadProcessMemory Lib "kernel32" Alias "ReadProcessMemory" (ByVal hProcess As Integer, ByVal lpBaseAddress As Integer, ByRef lpBuffer As Integer, ByVal nSize As Integer, ByRef lpNumberOfBytesWritten As Integer) As Integer
Private Declare Function CloseHandle Lib "kernel32" Alias "CloseHandle" (ByVal hObject As Integer) As Integer
Public Declare Function GetAsyncKeyState Lib "user32" Alias "GetAsyncKeyState" (ByVal vKey As Long) As Integer
Public RBuff1 As Long
Public RBuff2 As Single
Public RBuff3 As Integer
'WriteMemory
Public Function WriteMemory(ByVal Address As Integer, ByVal Value As Long, ByVal Bytes As Integer)
Dim warrockLookUp As Process() = Process.GetProcessesByName("WarRock")
If warrockLookUp.Length = 0 Then
End
End If
Dim processHandle As IntPtr = OpenProcess(&H1F0FFF, 0, warrockLookUp(0).Id)
WriteProcessMemory(processHandle, Address, Value, Bytes, Nothing)
CloseHandle(processHandle)
End Function
'ReadFloat
Public Function ReadFloat(ByVal Address As Single)
Dim warrockLookUp As Process() = Process.GetProcessesByName("WarRock")
If warrockLookUp.Length = 0 Then
End
End If
Dim processHandle As IntPtr = OpenProcess(&H1F0FFF, 0, warrockLookUp(0).Id)
ReadProcessMemory(processHandle, Address, RBuff1, 4, Nothing)
CloseHandle(processHandle)
Return RBuff1
End Function
'WriteFloat
Public Function WriteFloat(ByVal Address As Integer, ByVal Value As Single)
Dim warrockLookUp As Process() = Process.GetProcessesByName("WarRock")
If warrockLookUp.Length = 0 Then
End
End If
Dim processHandle As IntPtr = OpenProcess(&H1F0FFF, 0, warrockLookUp(0).Id)
WriteFloatMemory(processHandle, Address, Value, 4, Nothing)
CloseHandle(processHandle)
End Function
'ReadLong
Public Function ReadLong(ByVal Address As Integer)
Dim warrockLookUp As Process() = Process.GetProcessesByName("WarRock")
If warrockLookUp.Length = 0 Then
End
End If
Dim processHandle As IntPtr = OpenProcess(&H1F0FFF, 0, warrockLookUp(0).Id)
ReadProcessMemory(processHandle, Address, RBuff1, 4, Nothing)
CloseHandle(processHandle)
Return RBuff1
End Function
'ReadFloatPointer
Public Function ReadFloatPointer(ByVal Base As Integer, ByVal Offset As Short)
Dim fullAddress As Long
Dim warrockLookUp As Process() = Process.GetProcessesByName("WarRock")
If warrockLookUp.Length = 0 Then
End
End If
Dim processHandle As IntPtr = OpenProcess(&H1F0FFF, 0, warrockLookUp(0).Id)
ReadProcessMemory(processHandle, Base, RBuff1, 4, Nothing)
fullAddress = RBuff1 + Offset
ReadFloat(processHandle, fullAddress, RBuff2, 4, Nothing)
Return RBuff2
CloseHandle(processHandle)
End Function
'ReadLongPointer
Public Function ReadLongPointer(ByVal Base As Integer, ByVal Offset As Short, ByVal Bytes As Integer) 'ReadLongPointer
Dim fullAddress As Long
Dim warrockLookUp As Process() = Process.GetProcessesByName("WarRock")
If warrockLookUp.Length = 0 Then
End
End If
Dim processHandle As IntPtr = OpenProcess(&H1F0FFF, 0, warrockLookUp(0).Id)
ReadProcessMemory(processHandle, Base, RBuff1, 4, Nothing)
fullAddress = RBuff1 + Offset
ReadProcessMemory(processHandle, fullAddress, RBuff3, Bytes, Nothing)
Return RBuff3
CloseHandle(processHandle)
End Function
'WriteFloatPointer
Public Function WriteFloatPointer(ByVal Base As Integer, ByVal Offset As Short, ByVal Value As Single)
Dim fullAddress As Long
Dim warrockLookUp As Process() = Process.GetProcessesByName("WarRock")
If warrockLookUp.Length = 0 Then
End
End If
Dim processHandle As IntPtr = OpenProcess(&H1F0FFF, 0, warrockLookUp(0).Id)
ReadProcessMemory(processHandle, Base, RBuff1, 4, Nothing)
fullAddress = RBuff1 + Offset
WriteFloatMemory(processHandle, fullAddress, Value, 4, Nothing)
CloseHandle(processHandle)
End Function
'WriteLongPointer
Public Function WriteLongPointer(ByVal Base As Integer, ByVal Offset As Short, ByVal Value As Long, ByVal Bytes As Integer)
Dim fullAddress As Long
Dim warrockLookUp As Process() = Process.GetProcessesByName("WarRock")
If warrockLookUp.Length = 0 Then
End
End If
Dim processHandle As IntPtr = OpenProcess(&H1F0FFF, 0, warrockLookUp(0).Id)
ReadProcessMemory(processHandle, Base, RBuff1, 4, Nothing)
fullAddress = RBuff1 + Offset
WriteProcessMemory(processHandle, fullAddress, Value, Bytes, Nothing)
CloseHandle(processHandle)
End Function
'NOP
Public Function NOP(ByVal Address As Integer, ByVal value As Integer)
Dim warrockLookUp As Process() = Process.GetProcessesByName("WarRock")
If warrockLookUp.Length = 0 Then
End
End If
Dim processHandle As IntPtr = OpenProcess(&H1F0FFF, 0, warrockLookUp(0).Id)
WriteProcessMemory(processHandle, Address, value, 1, Nothing)
CloseHandle(processHandle)
End Function
|
i still don't understand any but i hope u can understand it better i also including UMM in a zip file if u don't understand still use it and see wat it do.
| Description: |
| VB.net Udetected Module maker by phenix |
|
| Filesize: |
118.07 KB |
| Viewed: |
3387 Time(s) |
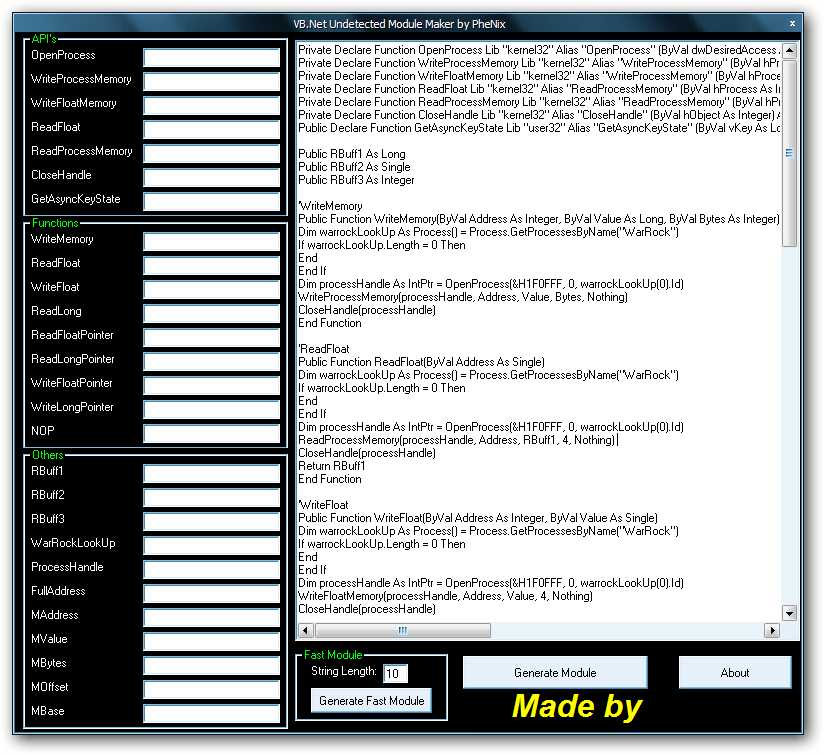
|
Last edited by darknight1601 on Mon Oct 05, 2009 9:48 am; edited 1 time in total |
|

 Reputation: 5
Reputation: 5


