| View previous topic :: View next topic |
| Author |
Message |
ChrisLearnsCE
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 13 Jun 2021
Posts: 9
|
 Posted: Fri Jun 25, 2021 9:21 pm Post subject: When changing a value, others change too? Posted: Fri Jun 25, 2021 9:21 pm Post subject: When changing a value, others change too? |
 |
|
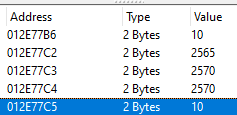
Basically, I have a list of static 2 byte variables. They are all in order in terms of offsets (12E77C4, 12E77C5, 12E77C6 etc.)
when I try to modify one of them, the other variables change for some reason. I can't seem to find any kind of pattern that I can decrypt.
I also don't think it's the app changing them, as I have the app paused while doing all this testing.
I have a screenshot where I can show what issue I'm having.
| Description: |
| I tried setting 12E77C3, C4 and C5 to the value of 10 in order. This is what I get. The values are all locked, and the app is paused, yet they still change. am I missing something here? |
|
| Filesize: |
3.89 KB |
| Viewed: |
1539 Time(s) |
|
|
|
| Back to top |
|
 |
TheyCallMeTim13
Wiki Contributor
 Reputation: 51 Reputation: 51
Joined: 24 Feb 2017
Posts: 976
Location: Pluto
|
 Posted: Fri Jun 25, 2021 9:40 pm Post subject: Posted: Fri Jun 25, 2021 9:40 pm Post subject: |
 |
|
Some of these are spaced by 1 byte but set with 2 byte value type, so changing one will change the other. Setting 0x...C2 will also set 0x...C3, and setting 0x...C3 will also set 0x...C4, and so on.
_________________
|
|
| Back to top |
|
 |
ChrisLearnsCE
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 13 Jun 2021
Posts: 9
|
 Posted: Fri Jun 25, 2021 9:44 pm Post subject: Posted: Fri Jun 25, 2021 9:44 pm Post subject: |
 |
|
| so what should I do? I'm not sure how these values work then
|
|
| Back to top |
|
 |
TheyCallMeTim13
Wiki Contributor
 Reputation: 51 Reputation: 51
Joined: 24 Feb 2017
Posts: 976
Location: Pluto
|
 Posted: Fri Jun 25, 2021 9:53 pm Post subject: Posted: Fri Jun 25, 2021 9:53 pm Post subject: |
 |
|
You can use "see what accesses" and see how the values are used, but you'll need to understand a bit of assembly.
_________________
|
|
| Back to top |
|
 |
ChrisLearnsCE
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 13 Jun 2021
Posts: 9
|
 Posted: Fri Jun 25, 2021 10:08 pm Post subject: Posted: Fri Jun 25, 2021 10:08 pm Post subject: |
 |
|
I only understand the basics and I'm not smart enough to be able to trace a long path of the variable to find it's source.
But it seems like changing the variable to a byte has helped so far, hopefully this might make tracking it easier. not sure if 2byte or byte has different assembly code or not.
|
|
| Back to top |
|
 |
TheyCallMeTim13
Wiki Contributor
 Reputation: 51 Reputation: 51
Joined: 24 Feb 2017
Posts: 976
Location: Pluto
|
 Posted: Fri Jun 25, 2021 10:41 pm Post subject: Posted: Fri Jun 25, 2021 10:41 pm Post subject: |
 |
|
It can be done a lot of different ways. If you're lucky you might find a "word ptr" or "byte ptr", with the instructions that access the address. "word" is 2 bytes so "dword" (double word) is 4 bytes and "qword" (quad word) is 8 bytes. But if you "see what assesses" the address and then in the instruction "see what addresses this instruction accesses" CE will select a value type for you, it's not 100% right but most times it is.
Also this might help: https://wiki.cheatengine.org/index.php?title=Tutorials:Value_types
_________________
|
|
| Back to top |
|
 |
|

 Reputation: 51
Reputation: 51 Reputation: 51
Reputation: 51 Reputation: 51
Reputation: 51

