| View previous topic :: View next topic |
| Author |
Message |
renomous
Advanced Cheater
![]() Reputation: 0 Reputation: 0
Joined: 15 Jul 2012
Posts: 86
|
 Posted: Sun Feb 26, 2017 9:30 am Post subject: can anyone tell me whats is that dwodr here ? Posted: Sun Feb 26, 2017 9:30 am Post subject: can anyone tell me whats is that dwodr here ? |
 |
|
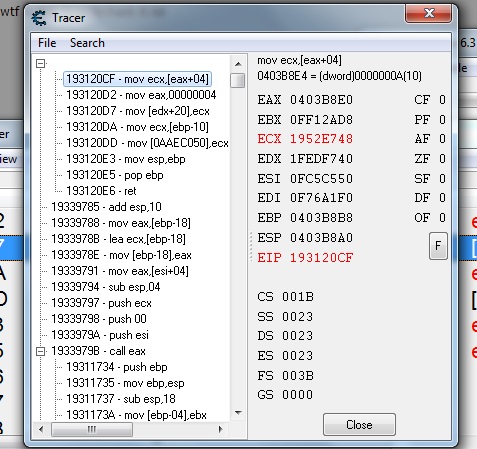
193120CF - mov ecx,[eax+04]
0403B8E4 = (dword)0000000A(10) << -----wtf is this how to hack it lol
---------------
EAX=0403B8E0
EBX=0FF12AD8
ECX=1952E748
EDX=1FEDF740
ESI=0FC5C550
EDI=0F76A1F0
EBP=0403B8B8
ESP=0403B8A0
EIP=193120CF
EFLAGS=00200202
-
193120D2 - mov eax,00000004
EAX=0403B8E0
EBX=0FF12AD8
ECX=0000000A << -------------------- my value that want to hack
EDX=1FEDF740
ESI=0FC5C550
EDI=0F76A1F0
EBP=0403B8B8
ESP=0403B8A0
EIP=193120D2
EFLAGS=00200302
-
193120D7 - mov [edx+20],ecx
1FEDF760 = (dword)00000009(9)
EAX=00000004
EBX=0FF12AD8
ECX=0000000A << --------------------
EDX=1FEDF740
ESI=0FC5C550
EDI=0F76A1F0
EBP=0403B8B8
ESP=0403B8A0
EIP=193120D7
EFLAGS=00200302
| Description: |
|
| Filesize: |
99.86 KB |
| Viewed: |
6277 Time(s) |
|
|
|
| Back to top |
|
 |
Filipe_Br
Master Cheater
![]() Reputation: 3 Reputation: 3
Joined: 07 Jan 2016
Posts: 272
Location: My house
|
 Posted: Tue Feb 28, 2017 7:48 am Post subject: Re: can anyone tell me whats is that dwodr here ? Posted: Tue Feb 28, 2017 7:48 am Post subject: Re: can anyone tell me whats is that dwodr here ? |
 |
|
DWORD = 4 Bytes
_________________
... |
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Tue Feb 28, 2017 7:15 pm Post subject: Posted: Tue Feb 28, 2017 7:15 pm Post subject: |
 |
|
193120CF - mov ecx,[eax+04]
Instruction is located at address 193120CF
The instruction pulls a value from [eax+04]
Register EAX equals 0403B8E0
0403B8E4 = (dword)0000000A(10)
EAX + 04 equals the address 0403B8E4
dword is the variable size (4-bytes)
0000000A is the value at that address in hex notation
(10) is the value at that address in decimal notation
|
|
| Back to top |
|
 |
didadadida93
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 27 Feb 2017
Posts: 1
Location: Front of my monitor
|
 Posted: Sun Mar 05, 2017 9:03 pm Post subject: Posted: Sun Mar 05, 2017 9:03 pm Post subject: |
 |
|
| Zanzer wrote: | 193120CF - mov ecx,[eax+04]
Instruction is located at address 193120CF
The instruction pulls a value from [eax+04]
Register EAX equals 0403B8E0
0403B8E4 = (dword)0000000A(10)
EAX + 04 equals the address 0403B8E4
dword is the variable size (4-bytes)
0000000A is the value at that address in hex notation
(10) is the value at that address in decimal notation |
how if the value at that address change frequently?
what should I do next?
|
|
| Back to top |
|
 |
Filipe_Br
Master Cheater
![]() Reputation: 3 Reputation: 3
Joined: 07 Jan 2016
Posts: 272
Location: My house
|
 Posted: Wed Mar 08, 2017 10:40 am Post subject: Posted: Wed Mar 08, 2017 10:40 am Post subject: |
 |
|
Although I think I'm talking bullshit.
You said the following:
ECX=0000000A << -------------------- my value that want to hack
So I suppose the statement you want is:
mov [edx+20],ecx
So just do a coding injection, which changes:
mov [edx+20],ecx
for:
mov [edx+20],#1000 -- new value
Or simply change the value of ecx, before it writes to any statement:
mov ecx,#1000 --new value
mov [edx+20],ecx
_________________
... |
|
| Back to top |
|
 |
|



