 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
Punz1A4
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 10 Jun 2016
Posts: 25
|
 Posted: Thu Jul 28, 2016 4:37 pm Post subject: Comparing Unicode Strings Posted: Thu Jul 28, 2016 4:37 pm Post subject: Comparing Unicode Strings |
 |
|
So I did a little research and managed to write a script that is supposed to compare two Unicode strings but it doesn't seem to work.
| Code: | code:
fstp dword ptr [esi+5C] //original code
push eax
push [esi+4]
push string
call kernel32.lstrcmpW
test eax,eax
jnz original_code
pop eax
mov [esi+5C],(float)50 //modify original value
original_code:
pop eax
mov esi,[esi+44]
jmp return
string:
db 'M',0,'a',0,'n',0,'a',0,'_',0,'S',0,'t',0,0 |
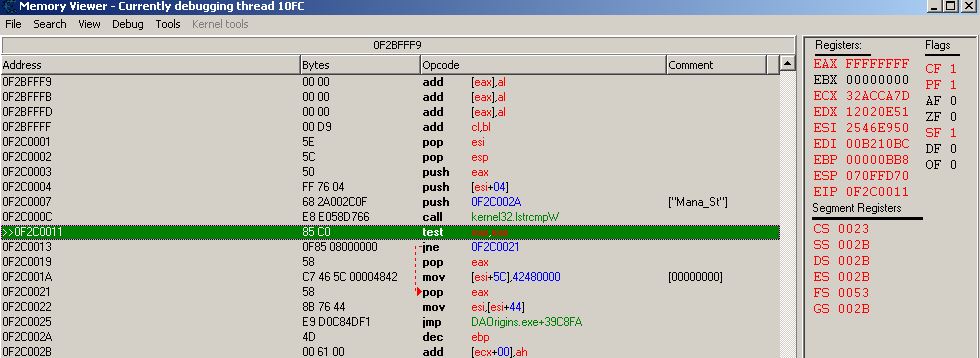
Breakpoint at test eax, eax show that ZF is 0 and value of eax is FFFFFFFF... so totally opposite to what it should be for it to work.
The thing I'm not sure about is if I declared the string properly... otherwise I dunno where's the problem.
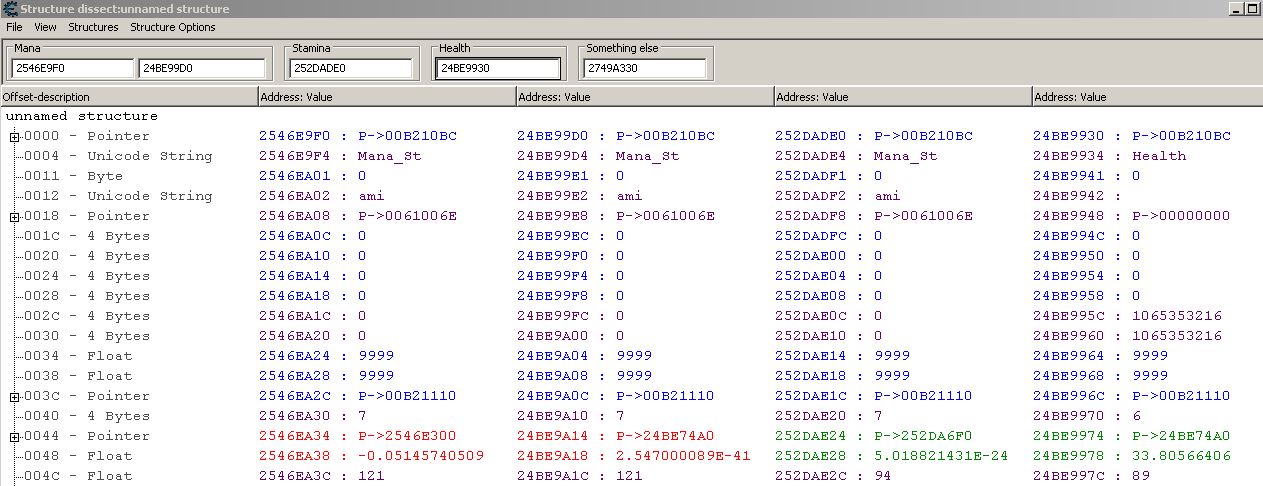
Attaching ss of breakpoint and structure dissect of addresses which should set the ZF. If anybody has an idea what may be wrong I would feel obliged.
| Description: |
|
| Filesize: |
77.79 KB |
| Viewed: |
10144 Time(s) |
|
| Description: |
|
| Filesize: |
144.87 KB |
| Viewed: |
10143 Time(s) |
|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 153 Reputation: 153
Joined: 06 Jul 2014
Posts: 4740
|
 Posted: Thu Jul 28, 2016 5:00 pm Post subject: Posted: Thu Jul 28, 2016 5:00 pm Post subject: |
 |
|
First of all, the breakpoint triggers before the instruction has been executed, but your problem lies in the fact that CE didn't correctly guess the elements in that structure. The string is actually "Mana_Stamina", which you would see if you browsed that memory region.
Try fixing that and see if it works.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
Punz1A4
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 10 Jun 2016
Posts: 25
|
 Posted: Thu Jul 28, 2016 6:02 pm Post subject: Posted: Thu Jul 28, 2016 6:02 pm Post subject: |
 |
|
| Quote: | | First of all, the breakpoint triggers before the instruction has been executed |
Thanks, didn't know that 
As for the Mana_Stamina thing - yeah, my bad it's like that in memory region though declaring
| Code: | string:
db 'M',0,'a',0,'n',0,'a',0,'_',0,'S',0,'t',0,'a',0,'m',0,'i',0,'n',0,'a',0,0 |
didn't change anything. Tried doing it with bytes instead of 'letters' aswell. It still doesn't work :/
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Thu Jul 28, 2016 6:25 pm Post subject: Posted: Thu Jul 28, 2016 6:25 pm Post subject: |
 |
|
| May need 1 more ",0" at the end, just to be safe.
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 153 Reputation: 153
Joined: 06 Jul 2014
Posts: 4740
|
 Posted: Thu Jul 28, 2016 6:32 pm Post subject: Posted: Thu Jul 28, 2016 6:32 pm Post subject: |
 |
|
The second argument (the first one you push) is also incorrect. Putting square brackets around a register (usually) gets the value at the address that register stores. In other words, you're pushing the first two characters of that string and not the address of the string.
One way to fix it:
| Code: | ...
lea eax,[esi+4]
push eax
push whereverMyStringIs
call kernel32.lstrcmpW
... |
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
Punz1A4
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 10 Jun 2016
Posts: 25
|
 Posted: Thu Jul 28, 2016 7:18 pm Post subject: Posted: Thu Jul 28, 2016 7:18 pm Post subject: |
 |
|
Huge thanks dude - loading address instead of value helped 
If anybody would ever be interested I also had to add one more jump (jumpafter), cause otherwise popping eax too many times caused the game to crash.
Again huge thanks Penguin.
| Code: | code:
fstp dword ptr [esi+5C] //original code
push eax
lea eax,[esi+4]
push eax
push string
call kernel32.lstrcmpW
test eax,eax
jz jumpafter
pop eax
original_code:
mov esi,[esi+44]
jmp return
jumpafter:
pop eax
mov [esi+5C],(float)50 //modify original value
jmp original_code
string:
db 'M',0,'a',0,'n',0,'a',0,'_',0,'S',0,'t',0,'a',0,'m',0,'i',0,'n',0,'a',0,0 |
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Thu Jul 28, 2016 7:49 pm Post subject: Posted: Thu Jul 28, 2016 7:49 pm Post subject: |
 |
|
Could've just removed your first pop all together. 
|
|
| Back to top |
|
 |
Punz1A4
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 10 Jun 2016
Posts: 25
|
 Posted: Fri Jul 29, 2016 12:26 pm Post subject: Posted: Fri Jul 29, 2016 12:26 pm Post subject: |
 |
|
Yeah, my brain really started to shut down though after the time I've spend looking in memory viewer 
Also I had to add one more 0 to the string for some reason when I wanted to declare 2nd one. Otherwise script was crashing the game.
| Code: | string_mana_stamina:
db 'M',0,'a',0,'n',0,'a',0,'_',0,'S',0,'t',0,'a',0,'m',0,'i',0,'n',0,'a',0,0,0
string_health:
db 'H',0,'e',0,'a',0,'l',0,'t',0,'h',0,0 |
dunno why
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Fri Jul 29, 2016 3:52 pm Post subject: Posted: Fri Jul 29, 2016 3:52 pm Post subject: |
 |
|
| Because unicode strings are two bytes, meaning they are null terminated by two zeroes.
|
|
| Back to top |
|
 |
Xblade Of Heaven
Master Cheater
 Reputation: 0 Reputation: 0
Joined: 16 Oct 2005
Posts: 395
Location: DEAD
|
 Posted: Fri Jul 29, 2016 4:18 pm Post subject: Posted: Fri Jul 29, 2016 4:18 pm Post subject: |
 |
|
2 bytes cmp unicode string, 2+2+2+2,etc....
| Code: | cmp dword ptr[eax+4],'M'
je ...
cmp dword ptr[eax+6],'a'
je ...
cmp dword ptr[eax+8],'n'
je ...
cmp dword ptr[eax+a],'a'
je ...
|
etc...
_________________
Welcome to the Hell.
 |
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 153
Reputation: 153 Reputation: 153
Reputation: 153 Reputation: 0
Reputation: 0



