| View previous topic :: View next topic |
| Author |
Message |
rog9001
Expert Cheater
 Reputation: 2 Reputation: 2
Joined: 22 Dec 2015
Posts: 214
Location: Jupiter
|
 Posted: Sat Jul 02, 2016 8:31 am Post subject: Never dealt with this. what do i do? Posted: Sat Jul 02, 2016 8:31 am Post subject: Never dealt with this. what do i do? |
 |
|
I downloaded Need for Speed Undercover and tried to make a cheat for money and after finding money (encrypted) I had a look at what accesses the address but what I got in the window was:
| Code: |
movzx eax,byte ptr [eax]
movsx eax,byte ptr [eax]
movzx edx,byte ptr [ecx+01]
movdqa xmm6,[esi+60]
|
after noping all the instruction I found out that the instruction "movsx eax,byte ptr [eax]" is the money because when noped money is showen as 0 and you cant buy anything but after putting the instruction back the money reappears and everything is back to normal. Problem is... I have never dealt with that type of instruction before so could someone help me make a script or something...    
| Code: |
[ENABLE]
alloc(newmem,2048)
label(returnhere)
label(originalcode)
label(exit)
newmem:
originalcode:
movsx eax,byte ptr [ecx]
movzx edx,byte ptr [ecx+01]
exit:
jmp returnhere
"nfs.exe"+3E6B0B:
jmp newmem
nop
nop
returnhere:
[DISABLE]
dealloc(newmem)
"nfs.exe"+3E6B0B:
movsx eax,byte ptr [ecx]
movzx edx,byte ptr [ecx+01]
|
I did some research but nothing really helped sadly.
|
|
| Back to top |
|
 |
hhhuut
Grandmaster Cheater
 Reputation: 6 Reputation: 6
Joined: 08 Feb 2015
Posts: 607
|
 Posted: Sat Jul 02, 2016 8:36 am Post subject: Posted: Sat Jul 02, 2016 8:36 am Post subject: |
 |
|
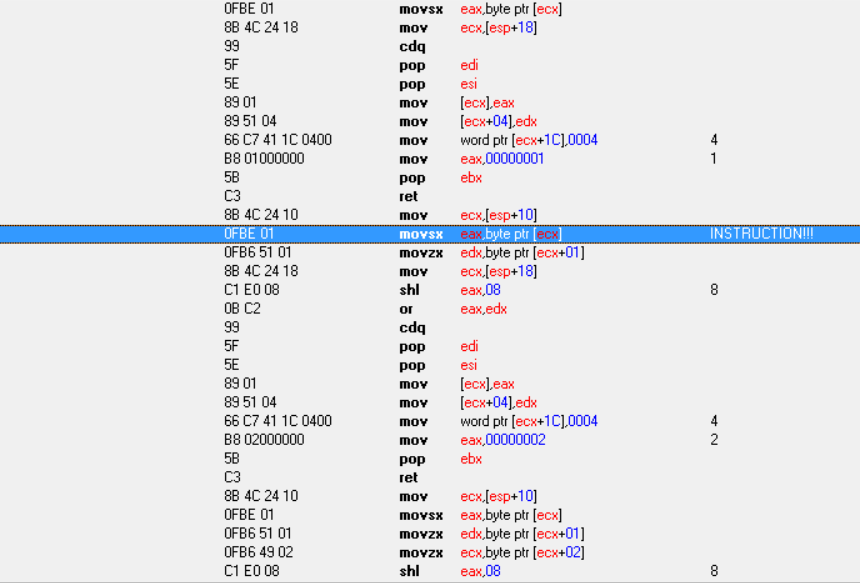
| Could you post a screenshot of the disassembler with about 10 lines before and after that instruction?
|
|
| Back to top |
|
 |
rog9001
Expert Cheater
 Reputation: 2 Reputation: 2
Joined: 22 Dec 2015
Posts: 214
Location: Jupiter
|
 Posted: Sat Jul 02, 2016 8:44 am Post subject: Posted: Sat Jul 02, 2016 8:44 am Post subject: |
 |
|
| Quote: | | Could you post a screenshot of the disassembler with about 10 lines before and after that instruction? |
Here ye go.
| Description: |
|
| Filesize: |
63.99 KB |
| Viewed: |
4810 Time(s) |
|
|
|
| Back to top |
|
 |
hhhuut
Grandmaster Cheater
 Reputation: 6 Reputation: 6
Joined: 08 Feb 2015
Posts: 607
|
 Posted: Sat Jul 02, 2016 8:51 am Post subject: Posted: Sat Jul 02, 2016 8:51 am Post subject: |
 |
|
It seems like the "encryption" just reverses the regular byte order ...
| Code: | [ENABLE]
alloc(newmem,2048)
label(returnhere)
label(originalcode)
label(exit)
newmem:
mov dx,#50000 //50k money
mov [ecx],dh
mov [ecx+01],dl
originalcode:
movsx eax,byte ptr [ecx]
movzx edx,byte ptr [ecx+01]
exit:
jmp returnhere
"nfs.exe"+3E6B0B:
jmp newmem
nop
nop
returnhere:
[DISABLE]
dealloc(newmem)
"nfs.exe"+3E6B0B:
movsx eax,byte ptr [ecx]
movzx edx,byte ptr [ecx+01] |
You can try this code, but first make sure that really only your money is accessed by this function, otherwise you may get some weird results 
|
|
| Back to top |
|
 |
|

 Reputation: 2
Reputation: 2 Reputation: 6
Reputation: 6 Reputation: 2
Reputation: 2 Reputation: 6
Reputation: 6

