 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
illones1985
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 17 Oct 2015
Posts: 20
|
 Posted: Sat Feb 27, 2016 11:30 pm Post subject: i found the right pointer, but returns ?? @ levelstart Posted: Sat Feb 27, 2016 11:30 pm Post subject: i found the right pointer, but returns ?? @ levelstart |
 |
|
| as the title subject says, i found a pointer for the value i want to manipulate, but when i first load the game and start playing, the pointer says ?? in the value section. i did an aob scan and dissassembled the bytes and then i found out what this instruction accesses. it results in one address which is good, and when i go back to look at the pointer, suddenly it realizes what it's supposed to be doing, and gives me a valid number that i can freeze. my question is how do i avoid all the extra scanning and imediately be able to change the pointer's value? if anyone needs more clarification, please let me know. thanks
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Sat Feb 27, 2016 11:38 pm Post subject: Posted: Sat Feb 27, 2016 11:38 pm Post subject: |
 |
|
Go to the instruction again and select Tools > Auto Assemble.
In the popup, select Template > AOB Injection.
Paste the generated code here.
|
|
| Back to top |
|
 |
illones1985
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 17 Oct 2015
Posts: 20
|
 Posted: Sat Feb 27, 2016 11:43 pm Post subject: Posted: Sat Feb 27, 2016 11:43 pm Post subject: |
 |
|
| Zanzer wrote: | Go to the instruction again and select Tools > Auto Assemble.
In the popup, select Template > AOB Injection.
Paste the generated code here. |
{ Game : NFS13.exe
Version:
Date : 2016-02-28
Author : Willy
This script does blah blah blah
}
[ENABLE]
aobscanmodule(INJECT,NFS13.exe,F3 0F 10 44 35 20) // should be unique
alloc(newmem,$1000)
label(code)
label(return)
newmem:
code:
movss xmm0,[ebp+esi+20]
jmp return
INJECT:
jmp code
nop
return:
registersymbol(INJECT)
[DISABLE]
INJECT:
db F3 0F 10 44 35 20
unregistersymbol(INJECT)
dealloc(newmem)
{
// ORIGINAL CODE - INJECTION POINT: "NFS13.exe"+262AB0
"NFS13.exe"+262A88: 8D 4C 24 10 - lea ecx,[esp+10]
"NFS13.exe"+262A8C: 51 - push ecx
"NFS13.exe"+262A8D: 8B CE - mov ecx,esi
"NFS13.exe"+262A8F: E8 BC B3 FF FF - call NFS13.exe+25DE50
"NFS13.exe"+262A94: 8B 06 - mov eax,[esi]
"NFS13.exe"+262A96: 8B 90 DC F3 02 00 - mov edx,[eax+0002F3DC]
"NFS13.exe"+262A9C: 8B 8C BA D0 A5 00 00 - mov ecx,[edx+edi*4+0000A5D0]
"NFS13.exe"+262AA3: 83 B9 9C 00 00 00 00 - cmp dword ptr [ecx+0000009C],00
"NFS13.exe"+262AAA: 75 59 - jne NFS13.exe+262B05
"NFS13.exe"+262AAC: 8B 54 24 0C - mov edx,[esp+0C]
// ---------- INJECTING HERE ----------
"NFS13.exe"+262AB0: F3 0F 10 44 35 20 - movss xmm0,[ebp+esi+20]
// ---------- DONE INJECTING ----------
"NFS13.exe"+262AB6: 8B 52 28 - mov edx,[edx+28]
"NFS13.exe"+262AB9: 8B 6C 24 10 - mov ebp,[esp+10]
"NFS13.exe"+262ABD: 0F 2F 84 2A 54 02 00 00 - comiss xmm0,[edx+ebp+00000254]
"NFS13.exe"+262AC5: 72 49 - jb NFS13.exe+262B10
"NFS13.exe"+262AC7: 8B 89 A0 00 00 00 - mov ecx,[ecx+000000A0]
"NFS13.exe"+262ACD: 51 - push ecx
"NFS13.exe"+262ACE: 8D 88 70 ED 02 00 - lea ecx,[eax+0002ED70]
"NFS13.exe"+262AD4: E8 97 93 1D 00 - call NFS13.exe+43BE70
"NFS13.exe"+262AD9: 8B C8 - mov ecx,eax
"NFS13.exe"+262ADB: E8 B0 46 F1 FF - call NFS13.exe+177190
}
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Sat Feb 27, 2016 11:57 pm Post subject: Posted: Sat Feb 27, 2016 11:57 pm Post subject: |
 |
|
May need to adjust the offset depending on the value you wanted.
| Description: |
|
Download |
| Filename: |
sample.ct |
| Filesize: |
1.13 KB |
| Downloaded: |
611 Time(s) |
|
|
| Back to top |
|
 |
illones1985
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 17 Oct 2015
Posts: 20
|
 Posted: Sun Feb 28, 2016 12:15 am Post subject: Posted: Sun Feb 28, 2016 12:15 am Post subject: |
 |
|
| Zanzer wrote: | | May need to adjust the offset depending on the value you wanted. |
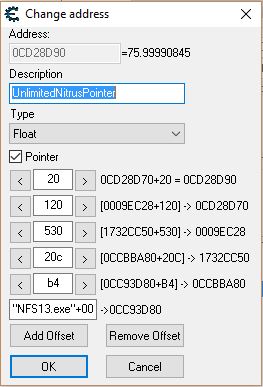
sorry, i'm not sure how to use your .ct. it gives me an error saying line 11 can't be compiled, and i'm not sure what you mean by change the offset. i found the pointer and offset. i screen captured the pointer. thanks for the quick response

| Description: |
|
| Filesize: |
33.79 KB |
| Viewed: |
5096 Time(s) |
|
| Description: |
|
| Filesize: |
33.27 KB |
| Viewed: |
5096 Time(s) |

|
|
|
| Back to top |
|
 |
rog9001
Expert Cheater
 Reputation: 2 Reputation: 2
Joined: 22 Dec 2015
Posts: 214
Location: Jupiter
|
 Posted: Thu Mar 10, 2016 4:04 pm Post subject: Posted: Thu Mar 10, 2016 4:04 pm Post subject: |
 |
|
| Code: |
movss xmm0,[ebp+esi+20]
|
If this is the instruction for Nitro then how about you find out what write or accesses the address then press the instruction above > more information > F. Have a look at the values in the other xmm's and if you find something like xmm4 with the value 100 or something then you can do:
Or if you want it more simple then just do this
| Code: |
//movss xmm0,[ebp+esi+20]
|
|
|
| Back to top |
|
 |
++METHOS
I post too much
![]() Reputation: 92 Reputation: 92
Joined: 29 Oct 2010
Posts: 4197
|
 Posted: Thu Mar 10, 2016 4:20 pm Post subject: Posted: Thu Mar 10, 2016 4:20 pm Post subject: |
 |
|
Change the script that Zanzer posted to match what is shown below, then update the address in your cheat table by removing the +20 offset. Report back.
| Code: | [ENABLE]
aobscanmodule(value,NFS13.exe,F3 0F 10 44 35 20)
alloc(newmem,$1000)
label(code)
label(return)
label(value_ptr)
registersymbol(value)
registersymbol(value_ptr)
newmem:
code:
push eax
lea eax,[ebp+esi+20]
mov [value_ptr],eax
pop eax
movss xmm0,[ebp+esi+20]
jmp return
value_ptr:
dd 0
value:
jmp code
nop
return:
[DISABLE]
value:
db F3 0F 10 44 35 20
unregistersymbol(value)
unregistersymbol(value_ptr)
dealloc(newmem) |
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 2
Reputation: 2


