| View previous topic :: View next topic |
| Author |
Message |
XaneXXXX
Expert Cheater
 Reputation: 0 Reputation: 0
Joined: 29 Nov 2012
Posts: 212
|
 Posted: Sun Sep 06, 2015 10:43 pm Post subject: Get address from opcodd aob? Posted: Sun Sep 06, 2015 10:43 pm Post subject: Get address from opcodd aob? |
 |
|
So i have this opcode that controls the time of day. It's in float and i don't have the pc on right now so let's say the code is
movss [rbx+7363666],xmm6
That opcode only controls ONE address. I want to make a script so that i can increase/decrease time of day by an hour. Can i somehow get the address out of the opcode?
I know how to do this with address aob only, and not the opcode itself.
Any tips?
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Sun Sep 06, 2015 11:33 pm Post subject: Posted: Sun Sep 06, 2015 11:33 pm Post subject: |
 |
|
Open Memory Viewer and just type that instruction in.
It'll produce the correct bytes for you.
From there, you can fill in the Writable checkbox (not checked, not unchecked).
Then search that array of bytes and hopefully not too many addresses pop up.
| Code: | | F3 0F11 B3 66363607 - movss [rbx+07363666],xmm6 |
|
|
| Back to top |
|
 |
XaneXXXX
Expert Cheater
 Reputation: 0 Reputation: 0
Joined: 29 Nov 2012
Posts: 212
|
 Posted: Mon Sep 07, 2015 4:13 pm Post subject: Posted: Mon Sep 07, 2015 4:13 pm Post subject: |
 |
|
| Zanzer wrote: | Open Memory Viewer and just type that instruction in.
It'll produce the correct bytes for you.
From there, you can fill in the Writable checkbox (not checked, not unchecked).
Then search that array of bytes and hopefully not too many addresses pop up.
| Code: | | F3 0F11 B3 66363607 - movss [rbx+07363666],xmm6 |
|
Could you explain this a little further? I din't think i understand hehe.
Thanks for your answer!
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Mon Sep 07, 2015 8:13 pm Post subject: Posted: Mon Sep 07, 2015 8:13 pm Post subject: |
 |
|
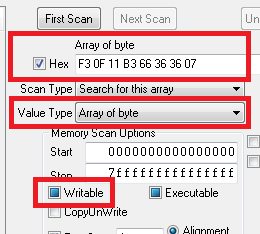
When you're in memory viewer, just select some random instruction and type:
movss [rbx+07363666],xmm6
Insert the single assembly instruction just to see what bytes it uses.
Then fill in the search criteria for those bytes as shown in the screenshot.
| Description: |
|
| Filesize: |
6.97 KB |
| Viewed: |
11111 Time(s) |
|
|
|
| Back to top |
|
 |
XaneXXXX
Expert Cheater
 Reputation: 0 Reputation: 0
Joined: 29 Nov 2012
Posts: 212
|
 Posted: Mon Sep 07, 2015 10:18 pm Post subject: Posted: Mon Sep 07, 2015 10:18 pm Post subject: |
 |
|
| Zanzer wrote: | When you're in memory viewer, just select some random instruction and type:
movss [rbx+07363666],xmm6
Insert the single assembly instruction just to see what bytes it uses.
Then fill in the search criteria for those bytes as shown in the screenshot. |
Thanks but that was not what i meant, If i do that i get the address (BASE ADDRESS) of the opcode, that's not what i want. i want the address that the opcode ACCESSES. not the opcode itself.
Thanks.
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Mon Sep 07, 2015 10:50 pm Post subject: Posted: Mon Sep 07, 2015 10:50 pm Post subject: |
 |
|
Can use injection to pull the address out when that instruction executes.
Can now use the pointer 'time_ptr' in your table.
| Code: | [ENABLE]
aobscan(time,F3 0F 11 B3 66 36 36 07)
alloc(newmem,$1000)
label(code)
label(return)
label(time_save)
label(time_ptr)
newmem:
code:
time_save:
readmem(time,8)
push rbx
db 48 81 C3
readmem(time+4,4)
mov [time_ptr],rbx
pop rbx
jmp return
time_ptr:
dq 0
time:
jmp code
nop
nop
nop
return:
registersymbol(time)
registersymbol(time_save)
registersymbol(time_ptr)
[DISABLE]
time:
readmem(time_save)
unregistersymbol(time)
unregistersymbol(time_save)
unregistersymbol(time_ptr)
dealloc(newmem) |
|
|
| Back to top |
|
 |
XaneXXXX
Expert Cheater
 Reputation: 0 Reputation: 0
Joined: 29 Nov 2012
Posts: 212
|
 Posted: Tue Sep 08, 2015 12:10 am Post subject: Posted: Tue Sep 08, 2015 12:10 am Post subject: |
 |
|
| Zanzer wrote: | Can use injection to pull the address out when that instruction executes.
Can now use the pointer 'time_ptr' in your table.
| Code: | [ENABLE]
aobscan(time,F3 0F 11 B3 66 36 36 07)
alloc(newmem,$1000)
label(code)
label(return)
label(time_save)
label(time_ptr)
newmem:
code:
time_save:
readmem(time,8)
push rbx
db 48 81 C3
readmem(time+4,4)
mov [time_ptr],rbx
pop rbx
jmp return
time_ptr:
dq 0
time:
jmp code
nop
nop
nop
return:
registersymbol(time)
registersymbol(time_save)
registersymbol(time_ptr)
[DISABLE]
time:
readmem(time_save)
unregistersymbol(time)
unregistersymbol(time_save)
unregistersymbol(time_ptr)
dealloc(newmem) |
|
Thanks! This is what i wanted. The script works but it shows the wrong address. i don't understand what: readmem(time+4,4) does.
Here is a pick of my script + the opcode i wanna access:
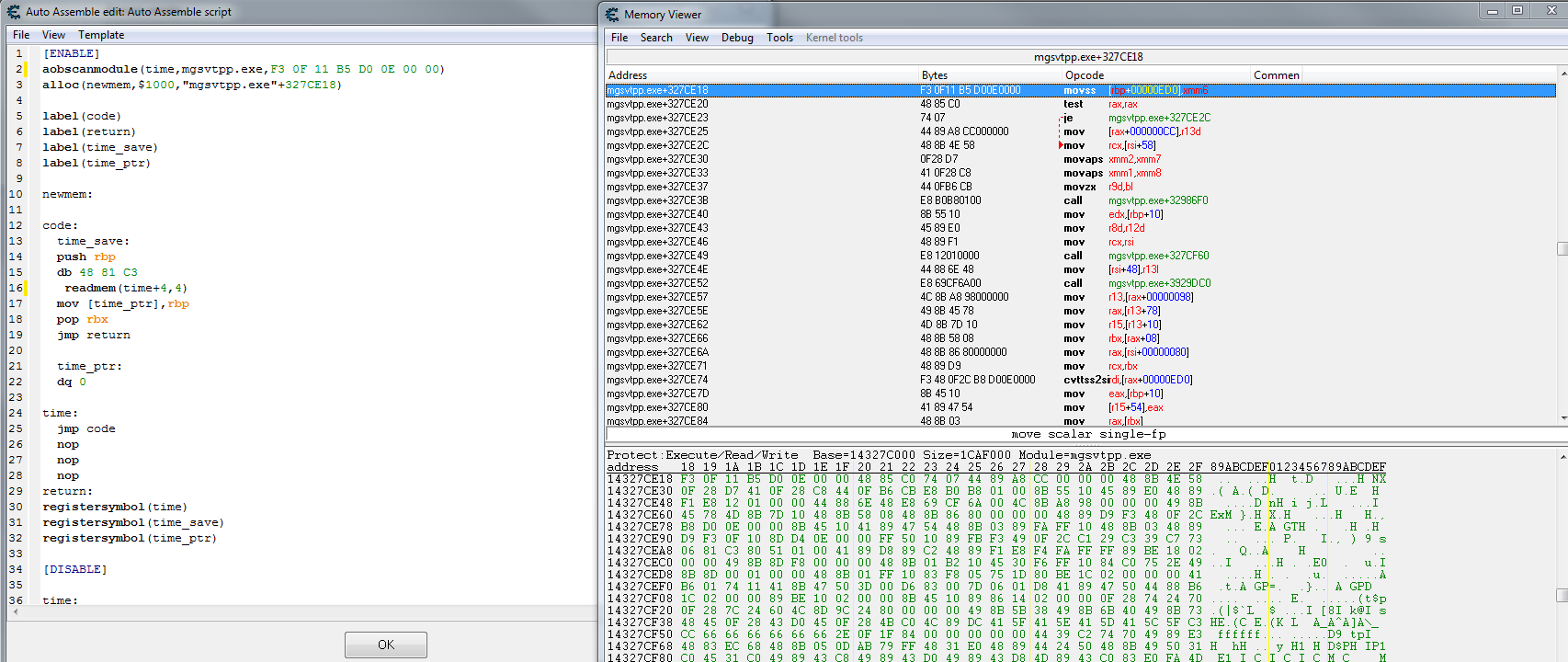
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Tue Sep 08, 2015 10:37 am Post subject: Posted: Tue Sep 08, 2015 10:37 am Post subject: |
 |
|
I'm surprised it didn't cause you to immediately crash. 
You're pushing RBP but then popping it into RBX, corrupting the registers.
The "db 48 81 C3" prepares the code "add rbx,____"
The "readmem(time+4,4)" copies the last 4 bytes (the offset), completing the above as "add rbx,ED0"
I had RBX because your original example stated RBX. However, you need RBP.
So change it to "db 48 81 C5" instead.
And fix that last POP to read "pop rbp".
|
|
| Back to top |
|
 |
XaneXXXX
Expert Cheater
 Reputation: 0 Reputation: 0
Joined: 29 Nov 2012
Posts: 212
|
 Posted: Tue Sep 08, 2015 11:01 am Post subject: Posted: Tue Sep 08, 2015 11:01 am Post subject: |
 |
|
My bad hehe, I corrected all the mistakes but it still shows the wrong value when I'm adding the address.
Do you have any idea what it could be?
I'm guessing that it has something to do that the offset is wrong
Thanks!
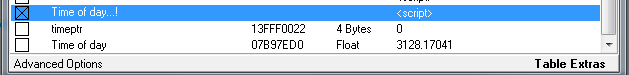
When i follow the code in memory:
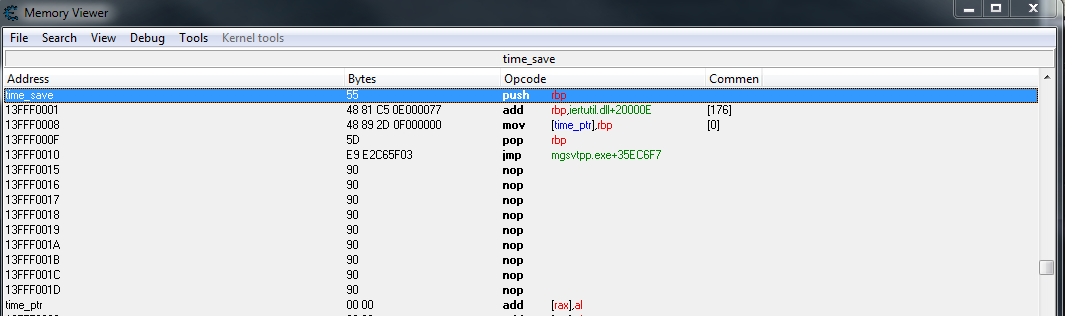
Looks like time_ptr is in the wrong place? 
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Tue Sep 08, 2015 11:13 am Post subject: Posted: Tue Sep 08, 2015 11:13 am Post subject: |
 |
|
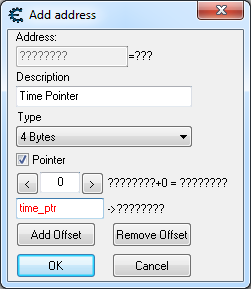
Did you declare the table pointer as shown?
Did you go back in game to let it execute the instruction as it normally would?
Just saw that ADD RBP line... looks like the offset to the READMEM was off?
| Description: |
|
| Filesize: |
11.49 KB |
| Viewed: |
11011 Time(s) |
|
Last edited by Zanzer on Tue Sep 08, 2015 11:18 am; edited 1 time in total |
|
| Back to top |
|
 |
XaneXXXX
Expert Cheater
 Reputation: 0 Reputation: 0
Joined: 29 Nov 2012
Posts: 212
|
 Posted: Tue Sep 08, 2015 11:15 am Post subject: Posted: Tue Sep 08, 2015 11:15 am Post subject: |
 |
|
Yep.
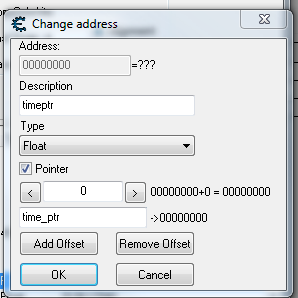
That's with the script on!
UPDATE: It works!! But the game crashes as soon as the right address shows up
I made a mistake in the script. Everything works now! Thank you very much.
One more question, what does the "dq 0" do? I'm guessing it stands for define qword?
Update again: It kind of works, The problem is that the script also FREEZES the time, the address won't update 
Last edited by XaneXXXX on Tue Sep 08, 2015 11:22 am; edited 1 time in total |
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Tue Sep 08, 2015 11:21 am Post subject: Posted: Tue Sep 08, 2015 11:21 am Post subject: |
 |
|
I only promised to get you the address. You're on your own with the crashing! 
Did you try again after a fresh game load? Maybe all of those enables/disables corrupted something?
edit: Oh, you got it working. Great!
Yes, DQ reserves 8-bytes below your code to be used as though it was an 8-byte variable named time_ptr.
edit2: Woops, you forgot to include the original code! 
| Code: | time_save:
readmem(time,8) |
This also explains why you crashed earlier.
Last edited by Zanzer on Tue Sep 08, 2015 11:26 am; edited 1 time in total |
|
| Back to top |
|
 |
XaneXXXX
Expert Cheater
 Reputation: 0 Reputation: 0
Joined: 29 Nov 2012
Posts: 212
|
 Posted: Tue Sep 08, 2015 11:25 am Post subject: Posted: Tue Sep 08, 2015 11:25 am Post subject: |
 |
|
| Zanzer wrote: | I only promised to get you the address. You're on your own with the crashing! 
Did you try again after a fresh game load? Maybe all of those enables/disables corrupted something?
edit: Oh, you got it working. Great!
Yes, DQ reserves 8-bytes below your code to be used as though it was an 8-byte variable named time_ptr.
edit2: Woops, you forgot to include the original code! 
| Code: | time_save:
readmem(time,8) |
|
I added the originalcode and everything works fine! Thank you very much for your help! 
|
|
| Back to top |
|
 |
XaneXXXX
Expert Cheater
 Reputation: 0 Reputation: 0
Joined: 29 Nov 2012
Posts: 212
|
 Posted: Tue Sep 08, 2015 10:08 pm Post subject: Posted: Tue Sep 08, 2015 10:08 pm Post subject: |
 |
|
Hello again! I was just wondering real fast, Why did you write
"readmem(time+4,4)" in the script? I mean,
Where did you get the numbers from? From what i can see, +4 = offset, and then you move the value of 4 into it or something haha.
These are commands I've never used before myself so I'm a little bit confused.
Then you said that i forget to add the originalcode:
movss [rbp+00000ED0],xmm6
But you told me to write: which worked fine, i just don't get how the originalcode can be .
I also want to understand this so that i can use it for other things in the future 
Thanks!! :roll
|
|
| Back to top |
|
 |
Zanzer
I post too much
![]() Reputation: 126 Reputation: 126
Joined: 09 Jun 2013
Posts: 3278
|
 Posted: Wed Sep 09, 2015 4:34 pm Post subject: Posted: Wed Sep 09, 2015 4:34 pm Post subject: |
 |
|
READMEM takes an address as the first parameter and a length as the second.
It will read those bytes into the CE script at the location it appears.
First, we defined the address "time" using:
aobscanmodule(time,mgsvtpp.exe,F3 0F 11 B5 D0 0E 00 00)
This positions the label right over the instruction:
F3 0F 11 B5 D0 0E 00 00 - movss [rbp+ED0],xmm6
So time+4 positions us over the above bytes used to define the offset (D0 0E 00 00).
The length of 4 tells CE to copy those 4 bytes directly into the code at the time.
Since we had the DB statement prior, that makes CE insert the following:
48 81 C3 D0 0E 00 00 - add rbx,ED0
The first READMEM points us directly on the "time" address and simply reads the 8 bytes (original code):
F3 0F 11 B5 D0 0E 00 00 - movss [rbp+ED0],xmm6
So those 8 bytes are copied into the script at that location.
Now none of your code really cares what the offset is because it is copied on activation.
I would normally take this one step further and make the AOB scan ignore the offset as well.
aobscanmodule(time,mgsvtpp.exe,F3 0F 11 B5 * * * * {more to make it unique})
|
|
| Back to top |
|
 |
|

 Reputation: 0
Reputation: 0 Reputation: 0
Reputation: 0 Reputation: 0
Reputation: 0 Reputation: 0
Reputation: 0 Reputation: 0
Reputation: 0 Reputation: 0
Reputation: 0 Reputation: 0
Reputation: 0 Reputation: 0
Reputation: 0






