 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
limau
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 18 Jun 2014
Posts: 21
|
 Posted: Wed Jun 18, 2014 11:06 pm Post subject: How to find the location of a global variable? Posted: Wed Jun 18, 2014 11:06 pm Post subject: How to find the location of a global variable? |
 |
|
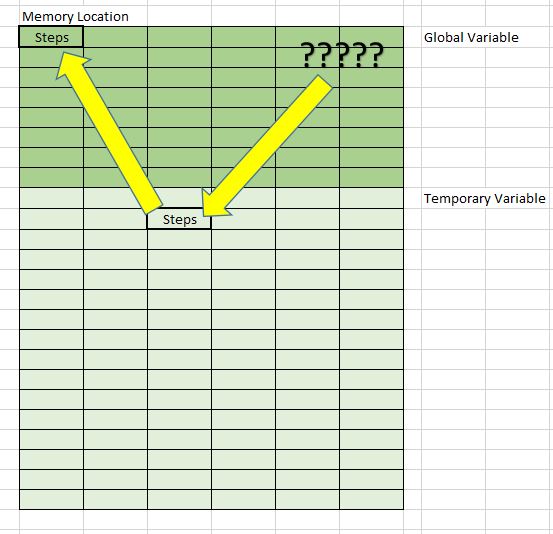
Is it possible to find global variable that is hidden as shown above (attachment)?
First I use normal 4 byte scan and I found the Steps Value inside the global variable, but this variable's purpose is just to display your Steps and not the actual value. Then I use what location writes to this location. Then from the assembly language, this value was copied from a location in the temporary variable (checked the ebp pointer pointing at). I tried to do the same with the temporary variable by putting what writes to this variable. But the problem is this is a temporary location and it gets updated periodic by other function as it's a temporary variable. From my trial and error, when ever the steps reduce, there is a few times the function will use back this temporary variable. Is there any way I can set a break point at this temporary variable, eg. break when 28 is written to this temporary location so that I can find out where the actual value is copied from?
| Description: |
|
| Filesize: |
56.13 KB |
| Viewed: |
28667 Time(s) |
|
|
|
| Back to top |
|
 |
Gniarf
Grandmaster Cheater Supreme
![]() Reputation: 43 Reputation: 43
Joined: 12 Mar 2012
Posts: 1285
|
 Posted: Fri Jun 20, 2014 2:02 pm Post subject: Re: How to find the location of a global variable? Posted: Fri Jun 20, 2014 2:02 pm Post subject: Re: How to find the location of a global variable? |
 |
|
| limauing wrote: | | Is it possible to find global variable that is hidden as shown above (attachment)? |
Let's say that we have SourceVar copied into TempVar copied into DisplayVar. If SourceVar and DisplayVar were always equal to each other you should have found both by scanning. Maybe SourceVar and DisplayVar use a different dayatype (one is float and one is a 4 byte int), or maybe DisplayVar=SourceVar1+SourceVar2+... in which case you should try to scan with unknown initial value+increased/decreased value. Or maybe SourceVar is encrypted, in which case you should try to scan with unknown initial value+changed/unchanged value.
| limauing wrote: | | From my trial and error, when ever the steps reduce, there is a few times the function will use back this temporary variable. |
Normally, the function that copies stuff into TempVar should be told where to copy from. Check the stack, locate the arguments passed on to your function and see if you find the address of TempVar in there, normally the address of SourceVar should be written near (often copy functions are declared like CopyFunction(destination, source, other parameters) ).
| limauing wrote: | | Is there any way I can set a break point at this temporary variable, eg. break when 28 is written to this temporary location so that I can find out where the actual value is copied from? |
What you're talking about is called a conditional breakpoint, more on this here: http://forum.cheatengine.org/viewtopic.php?p=5484054 (look at Dark Byte's answer to question 1). The lua engine understands EAX, EBX, ECX, EIP... in breakpoints conditions.
Aside that is your game made by softhouse charas?
_________________
DO NOT PM me if you want help on making/fixing/using a hack. |
|
| Back to top |
|
 |
limau
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 18 Jun 2014
Posts: 21
|
 Posted: Sat Jun 21, 2014 4:01 am Post subject: Posted: Sat Jun 21, 2014 4:01 am Post subject: |
 |
|
Thanks for the reply Gniarf.
| Quote: | | Let's say that we have SourceVar copied into TempVar copied into DisplayVar. If SourceVar and DisplayVar were always equal to each other you should have found both by scanning. Maybe SourceVar and DisplayVar use a different dayatype (one is float and one is a 4 byte int), or maybe DisplayVar=SourceVar1+SourceVar2+... in which case you should try to scan with unknown initial value+increased/decreased value. Or maybe SourceVar is encrypted, in which case you should try to scan with unknown initial value+changed/unchanged value. |
I tried using the "unknown initial value+increased/decreased" but doesn't seem to work here. Tried the "unknown initial value+changed/unchanged value" but ended up with more than 17,000+ results and can't seem to narrow it down further.
| Quote: |
Normally, the function that copies stuff into TempVar should be told where to copy from. Check the stack, locate the arguments passed on to your function and see if you find the address of TempVar in there, normally the address of SourceVar should be written near (often copy functions are declared like CopyFunction(destination, source, other parameters) ). |
I am still struggling on understanding the assembly meanings. Don't really know what''s what and what..
| Quote: | | What you're talking about is called a conditional breakpoint, more on this here:(look at Dark Byte's answer to question 1). The lua engine understands EAX, EBX, ECX, EIP... in breakpoints conditions. |
Thanks. I will try this conditional breakpoint.
| Quote: | | Aside that is your game made by softhouse charas? |
I am afraid not. This is a FB game called Anipop(apps_facebook_com_cuteanimal), very similar to CandyCrush. CandyCrush is pretty straight forward, you scan for the variable and change it. However Anipop did some extra precautions and like you suspected, probably encrypted the steps and score's actual location. They could even put a check sum to it too.
|
|
| Back to top |
|
 |
Gniarf
Grandmaster Cheater Supreme
![]() Reputation: 43 Reputation: 43
Joined: 12 Mar 2012
Posts: 1285
|
 Posted: Sat Jun 21, 2014 9:43 am Post subject: Posted: Sat Jun 21, 2014 9:43 am Post subject: |
 |
|
| limauing wrote: | | I am still struggling on understanding the assembly meanings. Don't really know what''s what and what.. |
Ah sorry, I thought you were familiar with asm when you mentioned checking ebp, anyway here's a for dummies version:
-When you use the find out what *** features, you have a button that reads "More information", click on it.
-There you have a button with a big S (for Stack), click on it to see the stack view.
When a (compiled) program calls a function that way: CopyFunction(destination, source, size) the corresponding assembly code is something like (the numbers to the left are example addresses):
| Code: | Test.exe+1000-push size //size could be a constant number, or contained in a register
Test.exe+1005-push source
Test.exe+100a-push destination
Test.exe+100f-call CopyFunction
Test.exe+1014-Another instruction |
The corresponding stack view if you put a breakpoint on the first instruction of CopyFunction would be:
| Code: | Test.exe+1014 //the address of the instruction immediately after the call
destination
source
size |
Of course since CopyFunction might use push/pop/call/sub esp,***/add esp,*** and your breakpoint isn't at the first instruction, you probably won't see the Test.exe+1014 at the top of the stack but it should be near the top, and destination's address should be just under or at least very close.
What I do is that I double click on every "(pointer)test.exe+***" starting from the top and if there is a call just above the highlighted line in the memory viewer, I check that this call is really the call to the function I had in the "find out what ***" window. Once I found the correct line, I just read the arguments just under.
Note: for now you don't care about the address column of the stack view, you're mostly interested in "secondary" which is an alternate way to display the content of the value column, the former making usually useful but possibly erroneous assumptions.
| limauing wrote: | | This is a FB game |
I don't have an FB account, but last time I heard about them, FB games were flash games, (since the are JIT-Just In Time compiled) you might not see any "(pointer)test.exe+***" equivalent, I guess you'll have to try every line and look for a call (give up if you don't find it on the first stack view page).
EDIT: one thing with flash games and integers: try scanning using the binary datatype in decimal mode (sometimes flash uses things like memory value=display value*2+1 or with other constants). Just don't scan for 0 when doing a first scan in binary mode.
_________________
DO NOT PM me if you want help on making/fixing/using a hack. |
|
| Back to top |
|
 |
limau
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 18 Jun 2014
Posts: 21
|
 Posted: Mon Jun 23, 2014 9:25 am Post subject: Posted: Mon Jun 23, 2014 9:25 am Post subject: |
 |
|
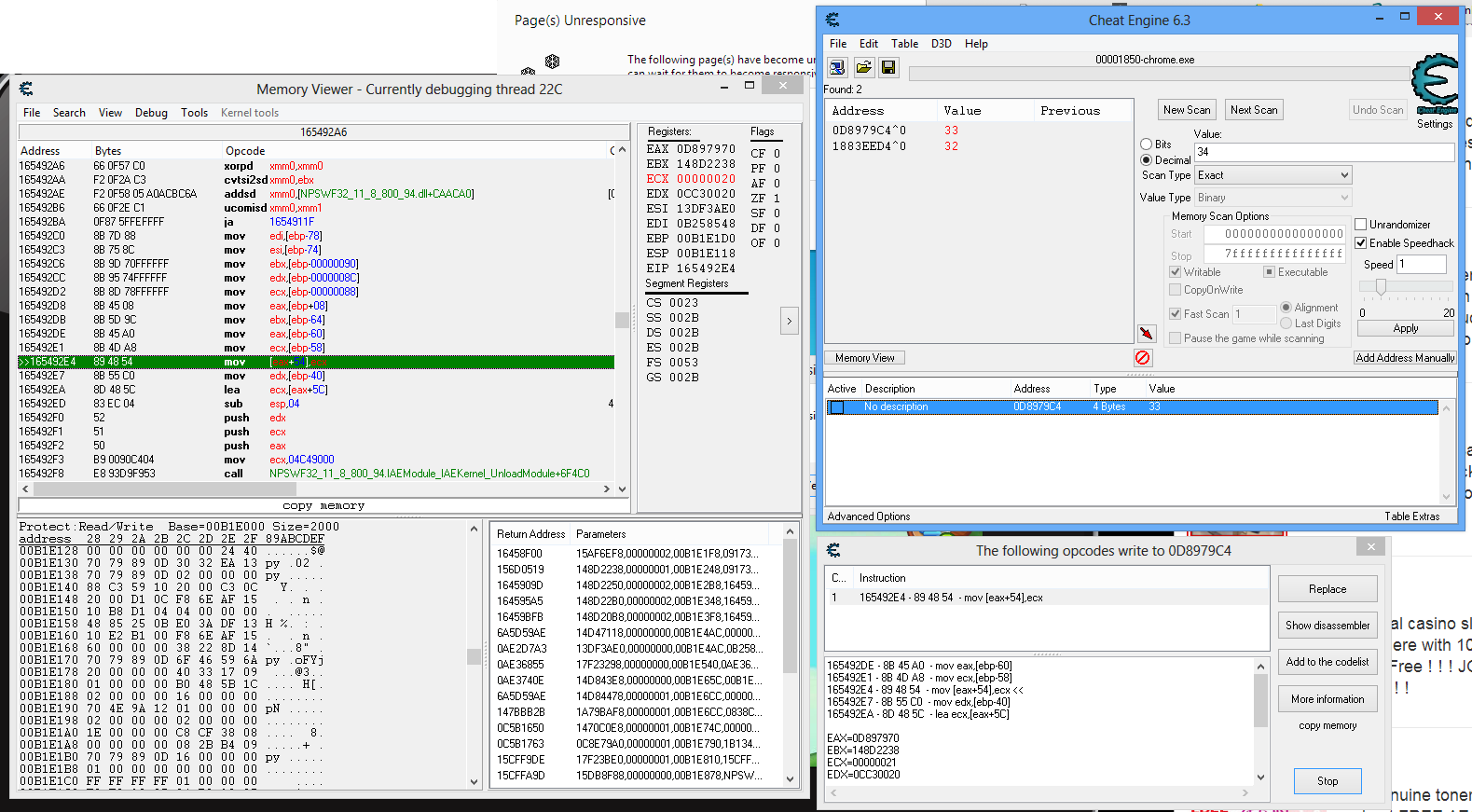
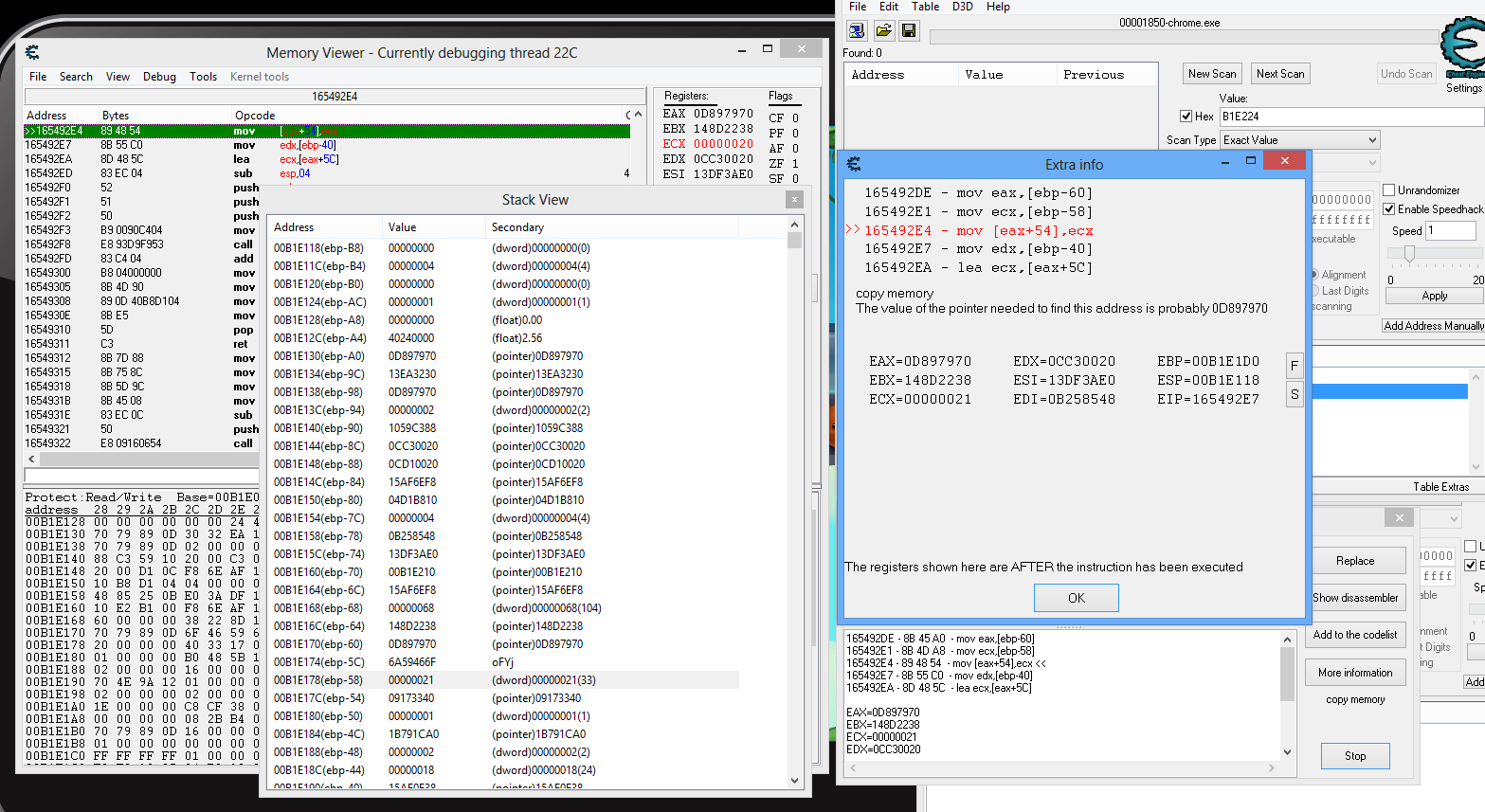
Ok, Here's what I got so far.
I've scan the display variable and use "find out what writes to this address".
I attached the screen shot, showing the assembly code and stack value.
What should I do next?
| Description: |
|
| Filesize: |
112.98 KB |
| Viewed: |
28501 Time(s) |
|
| Description: |
|
| Filesize: |
123.38 KB |
| Viewed: |
28501 Time(s) |
|
|
|
| Back to top |
|
 |
Gniarf
Grandmaster Cheater Supreme
![]() Reputation: 43 Reputation: 43
Joined: 12 Mar 2012
Posts: 1285
|
 Posted: Mon Jun 23, 2014 10:15 am Post subject: Posted: Mon Jun 23, 2014 10:15 am Post subject: |
 |
|
Scroll up, look for a "mov [ebp-58],***".
If you can't find any, look for a "mov [e**-58],***".
If you can't find any either, post the whole function. Function are usually separated by a bunch of nop or int 3.
_________________
DO NOT PM me if you want help on making/fixing/using a hack. |
|
| Back to top |
|
 |
limau
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 18 Jun 2014
Posts: 21
|
 Posted: Mon Jun 23, 2014 1:59 pm Post subject: Posted: Mon Jun 23, 2014 1:59 pm Post subject: |
 |
|
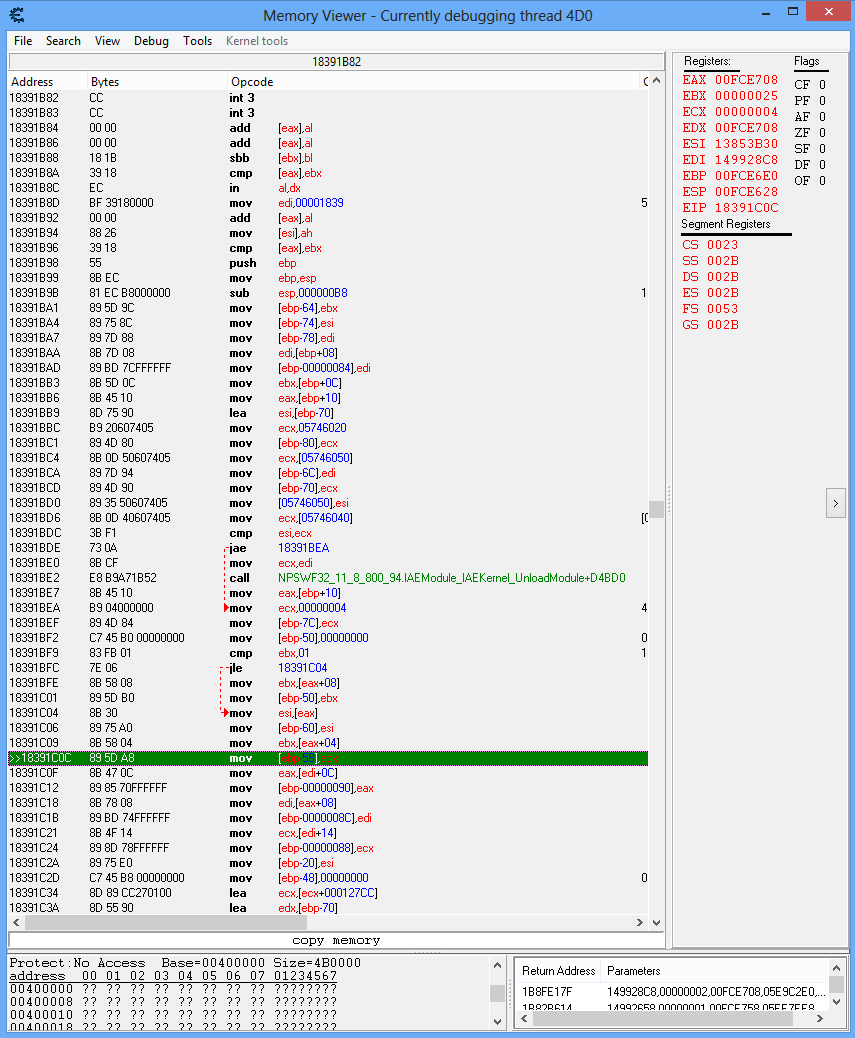
Ok, I scrolled up and up, and found this quite top of the function as you mentioned. What should I do next?
| Description: |
|
| Filesize: |
52.24 KB |
| Viewed: |
28478 Time(s) |
|
|
|
| Back to top |
|
 |
Gniarf
Grandmaster Cheater Supreme
![]() Reputation: 43 Reputation: 43
Joined: 12 Mar 2012
Posts: 1285
|
 Posted: Mon Jun 23, 2014 3:02 pm Post subject: Posted: Mon Jun 23, 2014 3:02 pm Post subject: |
 |
|
Read upward.
mov [ebp-58],ebx means the game stores ebx at ebp-58 (and you saw that ebp-58 was later on copied into ecx then ecx into DisplayVar).
Q:What is the last instruction that wrote ebx?
A:The line just above: mov ebx,[eax+4] . Now look at the order of magnitude: eax and esp are awfully close, so that means eax is also a temporary variable, or an argument passed on to your function.
Anyway, continue looking up, where does that eax come from? [ebp+10].
push ebp+mov ebp,esp is a common way to start a function, and whatever is above looks like bullshit so it's probably some data but no code thus I assume your function starts at this push ebp. In this case ebp+0x10 would mean the 3rd argument* passed on to your function.
In C your code looks like that:
| Code: | typedef struct _ThirdArgument
{
DWORD Unknown; //sizeof(DWORD)=4
int ValueToDisplay;
} ThirdArgument;
typedef struct _FirstArgument
{
BYTE Unknown[0x54]; //0x54 bytes before our payload
int DisplayVar;
} FirstArgument;
void(?) CopyFunction(FirstArgument Arg1, DWORD, ThirdArgument Arg3)
{
int ebx=Arg3.ValueToDisplay; //mov ebx,[eax+0] would be ebx=Arg3.Unknown, but we have a mov ebx,[eax+4]
int TempAkaEbpMinus58=ebx;
int ecx=TempAkaEbpMinus58;
Arg1.DisplayVar=ecx; //we know it's Arg1 because of the mov eax,[ebp+8] on 1.png
} |
What you have to do now is to look at the stack, find and double click on the line that contains "(ebp+4)"*, this line should show you where CopyFunction was called from. Go there and scroll up, you should see at least 3 push instructions. The 3rd one from the bottom is the equivalent of "push Arg3", trace where Arg3 comes from and more importantly find what writes (no, not the CE feature) on Arg3+4.
*:In functions that start with push ebp+mov ebp,esp:
[ebp+0] is a backup of what was ebp when you entered the function
[ebp+4] is the address of the instruction immediately after the call ThisFunction
[ebp+8] is the first argument
[ebp+C] is the second argument
[ebp+10] is the third argument
...
_________________
DO NOT PM me if you want help on making/fixing/using a hack. |
|
| Back to top |
|
 |
limau
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 18 Jun 2014
Posts: 21
|
 Posted: Tue Jun 24, 2014 1:39 am Post subject: Posted: Tue Jun 24, 2014 1:39 am Post subject: |
 |
|
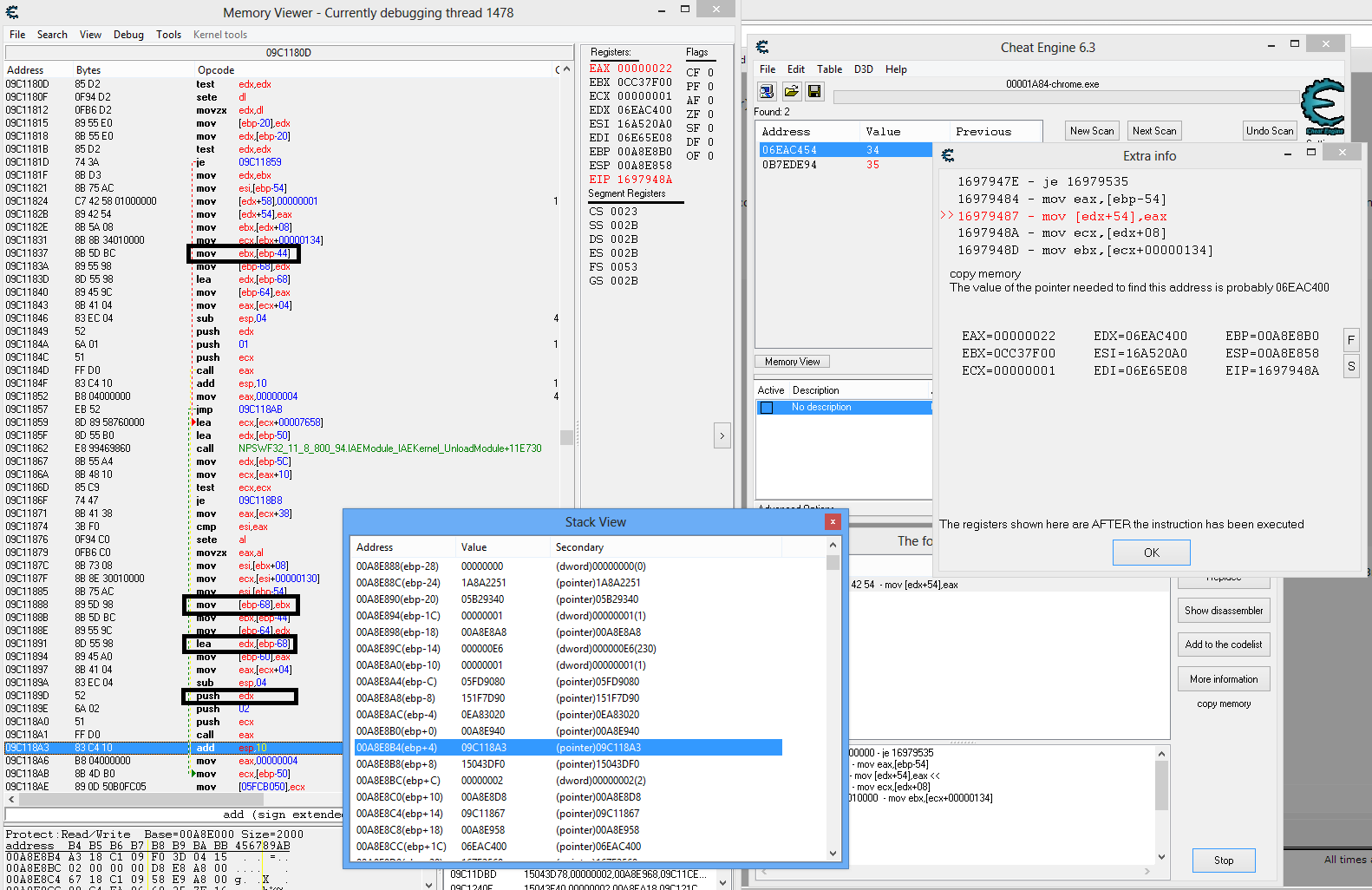
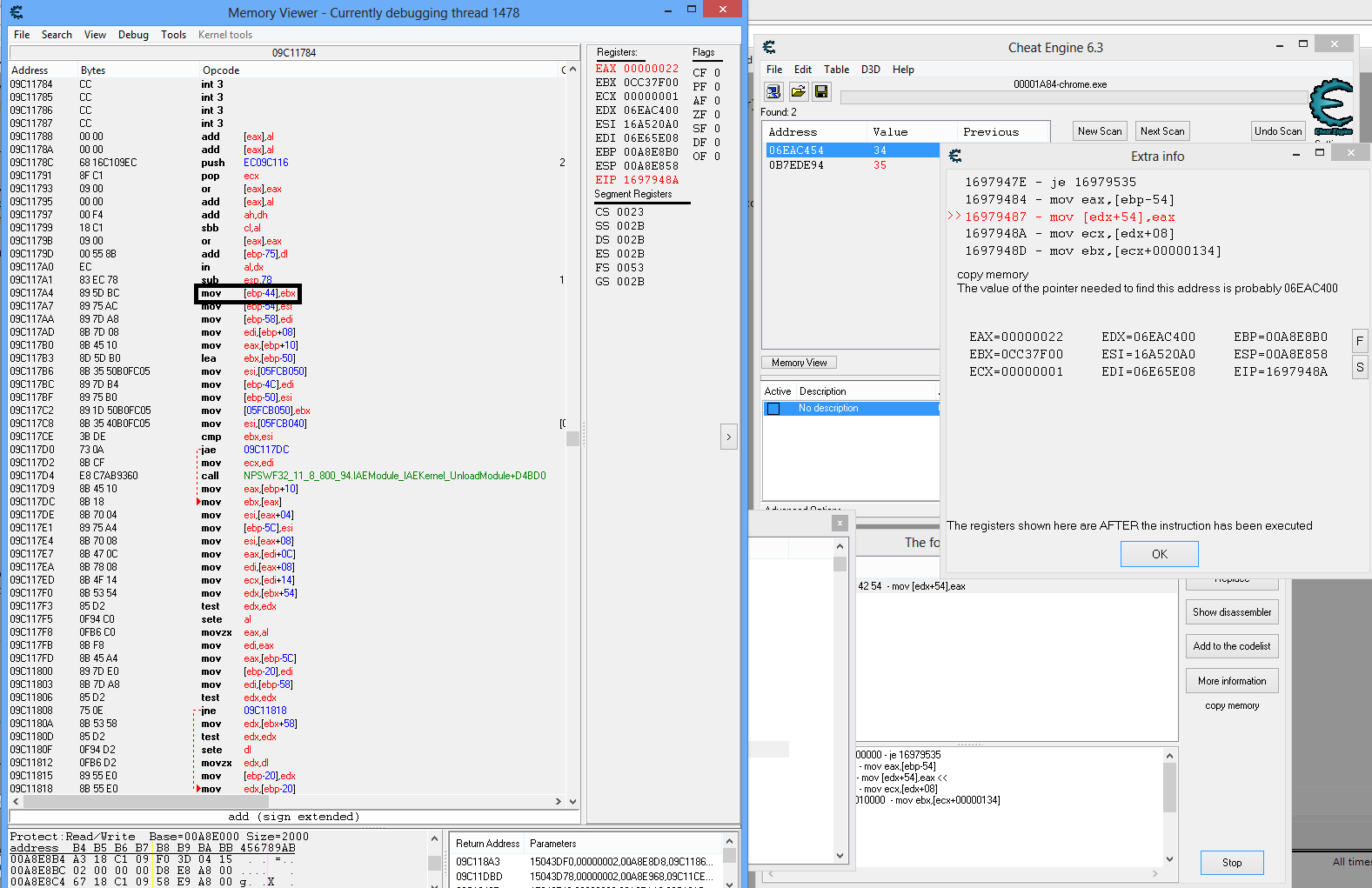
Ok, from the stack window, I found the ebp+4 as you mention. I jump to the address, and above it there is 3 push instructions. I find out what Arg3 till the top of the function. Where do I go to now?
| Description: |
|
| Filesize: |
126.2 KB |
| Viewed: |
28435 Time(s) |
|
| Description: |
|
| Filesize: |
94.54 KB |
| Viewed: |
28435 Time(s) |
|
|
|
| Back to top |
|
 |
Gniarf
Grandmaster Cheater Supreme
![]() Reputation: 43 Reputation: 43
Joined: 12 Mar 2012
Posts: 1285
|
 Posted: Tue Jun 24, 2014 9:31 am Post subject: Posted: Tue Jun 24, 2014 9:31 am Post subject: |
  |
|
Looks like you're getting the hang of backtracing, congratulation.
You have found CopyFunction ages ago, now you've found the function that calls CopyFunction, let's call the latter CopyFunction_1. CopyFunction_2 would be the function that calls CopyFunction_1, etc...
My naming convention might not be very good, if you've got a better suggestion, I'm all ears/eyes.
The boxed ebx on 5.png is probably set by the parent function (CopyFunction_2). Also you see the 55 8b ec bytes just above the sub esp,78, that's the bytecode for push ebp+mov ebp,esp.
Anyway beware of the lea edx,[ebp-68] (boxed on 4.png), which means that edx=ebp-68, and NOT edx=the 4 bytes at address ebp-68. So basically CopyFunction_1 is building a ThirdArgument struct on the stack, beginning at ebp-68. ThirdArgument.Unknown comes from the ebx on 5.png, but we're tracking ThirdArgument.ValueToDisplay which is at ebp-68+4=ebp-64.
Looking up at your screenshots, I see:
mov [ebp-64],eax at 9c11840
mov eax,[ebp-5c] at 9c117fd
mov [ebp-5c], esi at 9c117e1
mov esi,[eax+4] at 9c117de
mov eax,[ebp+10] at 9C117d9 and 9c117b0
Lol, ebp+10 means 3rd argument to CopyFunction_1, eax+4 means there is a 4 byte offset, exactly like when you traced CopyFunction.
You have 2 options to continue tracing:
A-right click on DisplayVar in your cheat table->browse this memory region->right click->data breakpoint->break on write, then debug->"execute till return" when cheat engine breaks execution. That will lead you to CopyFunction_1, execute till return again to go to CopyFunction_2. There you continue backtracing manually.
Note: if cheat engine stops on an instruction that starts with "ret", do debug->step over.
B-You use the ebp backup (at ebp+0)) in the stack view to see what was ebp for CopyFunction_1. Check that [CopyFunction_1's ebp+10]+4 is equal to DisplayVar to make sure you didn't lose track of what you are tracing. Then go to [CopyFunction_1's ebp+4] to locate CopyFunction_2.
In both cases the third argument is the address of Something (probably a ThirdArgument struct) and you want to know who wrote on Something+4 (the ValueToDisplay member).
Also check if Something is allocated on the stack or somewhere else (which would mean you hit the jackpot)
Thinking again about it, if you could locate the .swf of your game you could try to decompile it to at least get some clues on how SourceVar is handled, and maybe find it by scanning.
_________________
DO NOT PM me if you want help on making/fixing/using a hack. |
|
| Back to top |
|
 |
limau
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 18 Jun 2014
Posts: 21
|
 Posted: Wed Jun 25, 2014 10:54 am Post subject: Posted: Wed Jun 25, 2014 10:54 am Post subject: |
 |
|
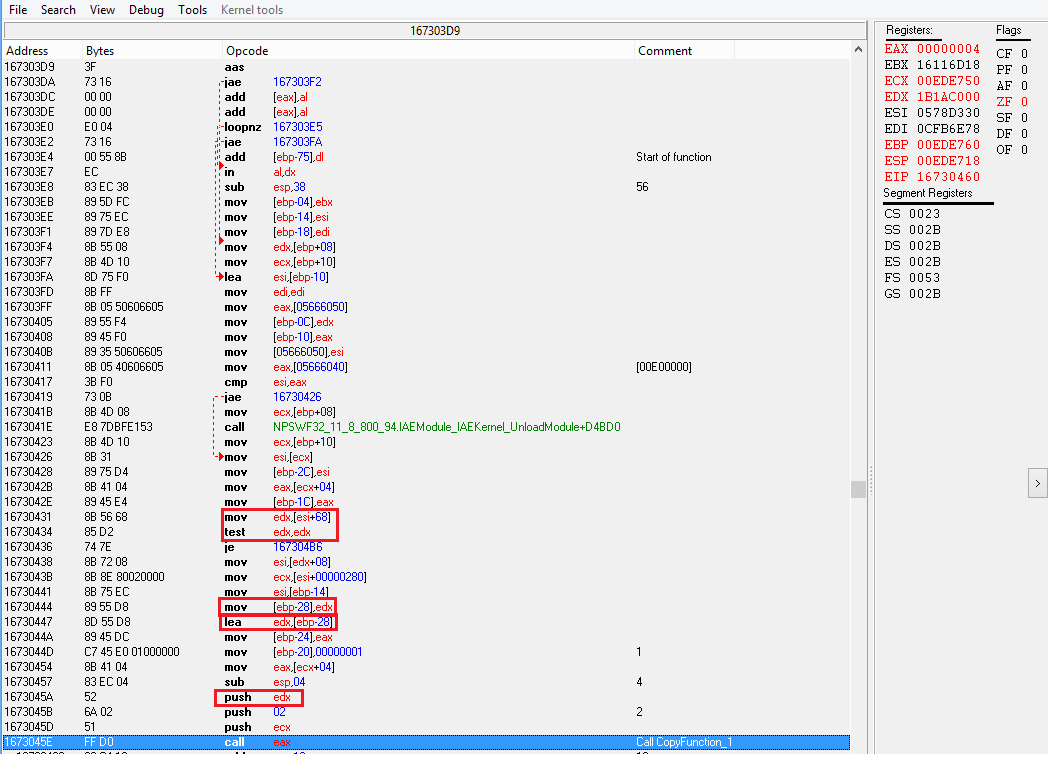
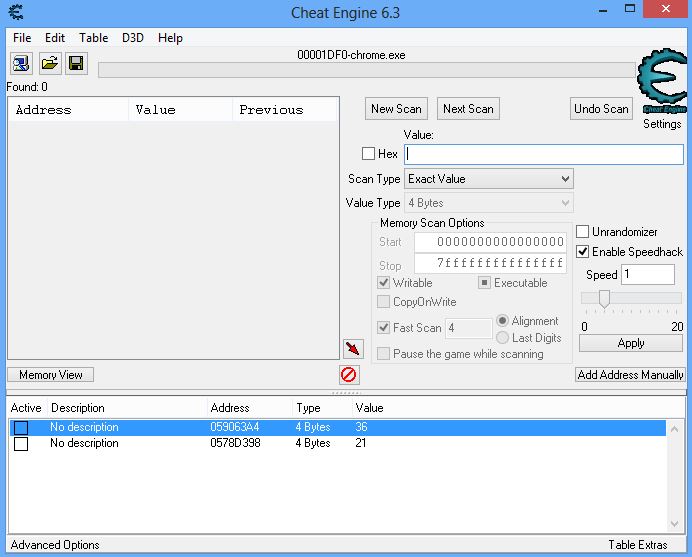
I tried finding the swf file, but seems like this game has many components of swf inside the temporary internet files. Was planning to use Sothink SWF Decompiler but that's out of the point since I can't get the whole SWF.
I tried Option A and that's a faster way to find the CopyFunction_2. Here's what I got, Please refer to 6.png.
From the box I highlighted, starting from the Arg3 which is the 3rd push from the bottom,
mov edx,[esi+68]
test edx,edx
mov [ebp-28],edx
lea edx,[ebp-28]
push edx
Then from the register esi which is 0578D330, I add hex68 to get 578D398. When I see the value in this address, it's 21. Is there something I missed?
*Also, after setting the break point, I want to try to change the value 21 to see if it's has something to do with the Steps. But when I delete the break point, CE hangs, I close it and the flash game crashes.
| Description: |
|
| Filesize: |
38.4 KB |
| Viewed: |
28370 Time(s) |
|
| Description: |
|
| Filesize: |
65.75 KB |
| Viewed: |
28370 Time(s) |
|
|
|
| Back to top |
|
 |
Gniarf
Grandmaster Cheater Supreme
![]() Reputation: 43 Reputation: 43
Joined: 12 Mar 2012
Posts: 1285
|
 Posted: Wed Jun 25, 2014 11:22 am Post subject: Posted: Wed Jun 25, 2014 11:22 am Post subject: |
 |
|
| limauing wrote: | mov [ebp-28],edx
lea edx,[ebp-28]
push edx
Then from the register esi which is 0578D330, I add hex68 to get 578D398. When I see the value in this address, it's 21. Is there something I missed? |
Same mistake as when you traced CopyFunction_1: the function is building a ThirdArgument structure at ebp-28, loading its address in edx, and passing edx as argument. That means you have ThirdArgument.Unknown at ebp-28 and ThirdArgument.ValueToDisplay is at ebp-28+4=ebp-24.
I'll let you find where what is written on ebp-24 comes from, but basically the conclusion is "Oh. No. Not. Again!".
| limauing wrote: | | *Also, after setting the break point, I want to try to change the value 21 to see if it's has something to do with the Steps. But when I delete the break point, CE hangs, I close it and the flash game crashes. |
CE hanging looks like a bug in CE, if you can reproduce it, you may go to the cheat engine section of this forum and report it.
BTW: CE 6.4 just came out.
However when a debugger is attached to a process and you close the debugger it is normal that the debugged program closes as well.
_________________
DO NOT PM me if you want help on making/fixing/using a hack. |
|
| Back to top |
|
 |
daspamer
Grandmaster Cheater Supreme
 Reputation: 54 Reputation: 54
Joined: 13 Sep 2011
Posts: 1588
|
 Posted: Wed Jun 25, 2014 3:06 pm Post subject: Posted: Wed Jun 25, 2014 3:06 pm Post subject: |
 |
|
Game encoding functions..
| Code: | package com.he.animal.utils
{
public class SecretInteger extends Object
{
private var _a:int;
private var _b:int;
private var _c:C;
private var _encryptedValue:int;
private var _password:int;
public function SecretInteger(param1:int = 0)
{
this.value = param1;
return;
}// end function
public function get value() : int
{
return (this._a + this._c.v) / this._b;
}// end function
public function get isValidate() : Boolean
{
var _loc_1:* = this._encryptedValue ^ this._password;
return this.value == _loc_1;
}// end function
public function set value(param1:int) : void
{
this._password = Math.random() * param1;
this._encryptedValue = param1 ^ this._password;
this._b = Math.floor(Math.random() * SecretScale.INT_SCALE_NUMBER) + 1;
param1 = param1 * this._b;
this._a = Math.floor(Math.random() * param1);
this._c = new C(param1 - this._a);
return;
}// end function
}
} |
This was suppose to work
| Code: | EncryptValue // I'm gonna store it plain... so I could also override return function and make it return plain
d0 30 d0 60 ?? ?? ?? 46 ?? ?? ?? d1 a2 68 ?? ?? d0 d1 d0 66 ?? ?? aa 68 ?? ?? d0 60 ?? ?? ?? 60 ?? ?? ?? 46 ?? ?? ?? 60 ?? ?? 66 ?? ?? a2 46 ?? ?? ?? ?? 24 01 a0 68 ?? ?? d1 d0 66 ?? ?? a2 73 d5 d0 60 ?? ?? ?? 60 ?? ?? ?? 46 ?? ?? ?? d1 a2 46 ?? ?? ?? ?? 68 ?? ?? d0 5d ?? ?? d1 d0 66 ?? ?? ?? 4a ?? ?? ?? 68 ?? ?? 47
d0 30 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 d0 d1 68 ?? ?? 47 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02 02
GetValue
d0 30 d0 66 ?? ?? d0 66 ?? ?? 66 ?? ?? a0 d0 66 ?? ?? a3 48
d0 30 d0 66 ?? ?? 48 02 02 02 02 02 02 02 02 02 02 02 02 02 |
(Storing value in _a variable and returning _a value);
_________________
I'm rusty and getting older, help me re-learn lua. |
|
| Back to top |
|
 |
Gniarf
Grandmaster Cheater Supreme
![]() Reputation: 43 Reputation: 43
Joined: 12 Mar 2012
Posts: 1285
|
|
| Back to top |
|
 |
daspamer
Grandmaster Cheater Supreme
 Reputation: 54 Reputation: 54
Joined: 13 Sep 2011
Posts: 1588
|
 Posted: Wed Jun 25, 2014 4:33 pm Post subject: Posted: Wed Jun 25, 2014 4:33 pm Post subject: |
 |
|
| Gniarf wrote: | And there comes the flash game expert... 
@DaSpamer
Given the number of 02 in your patches I assume it means nop in ActionScript, heh?
Still since AS(3?) is compiled into asm at runtime, is it ok to apply your patches at the main menu, or is it too late and the OP should patch the .swf?
(I can't check because I don't have/want a FB account)
Thanks for showing us the encryption function. By the looks of it, forcing Math.random() to return 0 would surely have lovely results, hehehe... Aside from gameplay side effects... |
Yes 02 means no operation.
I will check effects if forcing 0 instead of math.random(), it'll be much easier to set up a formula.
This should be activated on screen loading (around the 70-100%, pause process..).
If you could tell me what exactly you seek to accomplish, I could help  . .
Edit:
Trying with forcing 1, because forcing 0 would pretty much break it (all values gonna be 0).
Here the force 1 instead math.random (replace 24 XX with any other number)
| Code: | d0 30 d0 60 ?? ?? ?? 46 ?? ?? ?? d1 a2 68 ?? ?? d0 d1 d0 66 ?? ?? aa 68 ?? ?? d0 60 ?? ?? ?? 60 ?? ?? ?? 46 ?? ?? ?? 60 ?? ?? 66 ?? ?? a2 46 ?? ?? ?? ?? 24 01 a0 68 ?? ?? d1 d0 66 ?? ?? a2 73 d5 d0 60 ?? ?? ?? 60 ?? ?? ?? 46 ?? ?? ?? d1 a2 46 ?? ?? ?? ?? 68 ?? ?? d0 5d ?? ?? d1 d0 66 ?? ?? ?? 4a ?? ?? ?? 68 ?? ?? 47
d0 30 d0 24 01 02 02 02 02 02 02 d1 a2 68 ?? ?? d0 d1 d0 66 ?? ?? aa 68 ?? ?? d0 60 ?? ?? ?? 24 01 02 02 02 02 02 02 60 ?? ?? 66 ?? ?? a2 46 ?? ?? ?? ?? 24 01 a0 68 ?? ?? d1 d0 66 ?? ?? a2 73 d5 d0 60 ?? ?? ?? 24 01 02 02 02 02 02 02 d1 a2 46 ?? ?? ?? ?? 68 ?? ?? d0 5d ?? ?? d1 d0 66 ?? ?? ?? 4a ?? ?? ?? 68 ?? ?? 47
|
| Code: | param1 = 17 // first level
// Let's see what we can do..
this._password = 1 * param1 // 17 //this._password = Math.random() * param1;
this._encryptedValue = param1 ^ this._password// Big value (8.2724026188634e+020) //this._encryptedValue = param1 ^ this._password;
this._b = math.floor(1 * SecretScale.INT_SCALE_NUMBER (=5)) + 1// 6 //this._b = Math.floor(Math.random() * SecretScale.INT_SCALE_NUMBER) + 1; //SecretScale.INT_SCALE_NUMBER is defined as 5 in other A.S.
param1 = param1 * this._b// 102 //param1 = param1 * this._b;
this._a = Math.floor(1 * param1);// 102 //this._a = Math.floor(Math.random() * param1);
this._c = new C(param1 - this._a);// 0 //this._c = new C(param1 - this._a); //C is a class, it stores the value inside the class. (this._c.v)
return // end of function.. //return; |
_________________
I'm rusty and getting older, help me re-learn lua.
Last edited by daspamer on Wed Jun 25, 2014 5:12 pm; edited 2 times in total |
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 54
Reputation: 54 Reputation: 54
Reputation: 54








