 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
Gorki
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 17 Nov 2012
Posts: 2
|
 Posted: Sat Nov 17, 2012 5:39 pm Post subject: Finding the right address. Posted: Sat Nov 17, 2012 5:39 pm Post subject: Finding the right address. |
 |
|
Hello, and so I wanted a little fun poitnerami. I found a static address corresponding to the value of the game but looking for who is responsible for the address shown on the screen pops up thousands of addresses and do not know how to go about it. I put a screen.
| Description: |
|
| Filesize: |
25.51 KB |
| Viewed: |
7468 Time(s) |

|
|
|
| Back to top |
|
 |
Fresco
Grandmaster Cheater
![]() Reputation: 4 Reputation: 4
Joined: 07 Nov 2010
Posts: 600
|
 Posted: Sun Nov 18, 2012 5:02 am Post subject: Posted: Sun Nov 18, 2012 5:02 am Post subject: |
 |
|
are you sure it's the right address ?
perhaps you can look a the "count" (how many times the code wrote to the address). for example if it's ammo, you shoot once, and the count should be 1.
also try to add them all to the codelist and see if they write to other addresses too.
if you really can't find a solution, just nop them all for the static address you found.
go auto assemble and:
| Code: |
//original code = mov [eax+4],ecx
//bla bla
label(nopme)
pushfd //save all flags
push ebx // you should use a register that is not used by the code, in fact the code uses only eax and ecx, and i used ebx.
lea ebx,[eax+4] // load effective address of value [eax+4] into ebx
cmp ebx,(here goes the static address) //ex: game.exe+hexoffset
je nopme // if the code want's to write to your address nop it
mov [eax+4],ecx // original code (get's executed if eax+4 is not equal to game.exe+hexoffset)
nopme: //label defined
pop ebx // restore original ebx
popfd // restore flags
|
PS: call / push / pop / etc ... all of the codes that do not modify a value of some address ex: [eax+4] don't write to any code, therefore don't even bother nopping them because they don't change anything nor the value of your address.
_________________
... Fresco |
|
| Back to top |
|
 |
Gorki
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 17 Nov 2012
Posts: 2
|
 Posted: Sun Nov 18, 2012 7:30 am Post subject: Posted: Sun Nov 18, 2012 7:30 am Post subject: |
 |
|
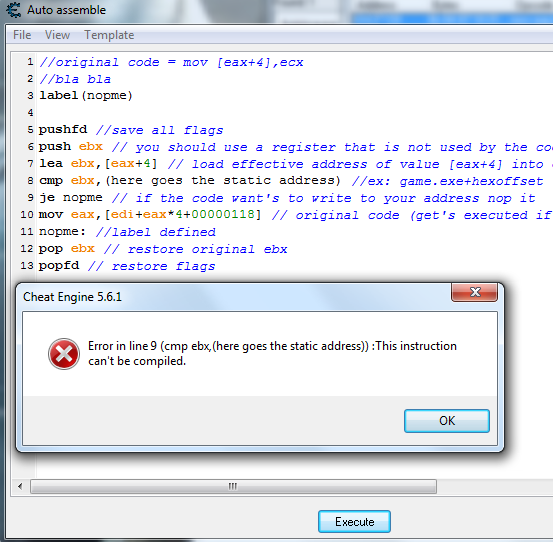
I added your code and changed the line in the original code and pops up an error
#Edit 1
Something changed, and it worked. Now, how to add a script to the list of addresses to have something like in the Annex.
| Description: |
|
| Filesize: |
2.21 KB |
| Viewed: |
7411 Time(s) |

|
| Description: |
|
| Filesize: |
75 KB |
| Viewed: |
7425 Time(s) |
|
|
|
| Back to top |
|
 |
Fresco
Grandmaster Cheater
![]() Reputation: 4 Reputation: 4
Joined: 07 Nov 2010
Posts: 600
|
 Posted: Tue Nov 20, 2012 11:12 am Post subject: Posted: Tue Nov 20, 2012 11:12 am Post subject: |
 |
|
Sorry, I assumed you knew some basic assembly and how to use AA in CE.
The code I wrote in the previous post does not work unless you modify it to suit your needs.
| Fresco wrote: | [...] | Code: | [...]
cmp ebx,(here goes the static address) //ex: game.exe+hexoffset
[...] |
[...] |
here you should replace "(here goes the static address)" with the static address, I even gave you an example on how should it look like: 'game.exe+hexoffset' a concrete example would be:
cheatengine-x86_64.exe+16FC0
and if that's the case, you should write in your code:
| Code: | | cmp ebx, game.exe+hexoffset |
_____________________________________
anyways, form what i understood. you have found an hypothetical static address which is shown by CE in green color, meaning that it never changes.
a static address should look like: game.exe+offset (being game.exe a module or the game itself and offset a hex number).
i got that you want to freeze it's value.
well, search for a code that writes to that address.
the instruction above writes the value of ebx register into memory location eax+4 simple no? now look at eax's value and use a hex calculator to add 4 to that value you'll get an address (memory location) on which the instruction mov will perform it's action to move ebx.
got it ?
auto assemble all the codes that have between square brackets your static address.
use cmp to check if the codes writes to your address or not.
if yes, just nop and return if not, do original code and return.
also, you'll have an | Code: | [ENABLE]
//code to be executed when you activate the script
[DISABLE]
//code to be executed when you deactivate the script |
enable - disable section.
just read some tutorials about that, I'm sure you'll find your way.
a complete working script is this:
| Code: | [ENABLE]
alloc(newmem,2048,"cheatengine-x86_64.exe"+16CF0) //2kb should be enough
label(returnhere)
label(originalcode)
label(exit)
newmem: //this is allocated memory, you have read,write,execute access
//place your code here
sub rsp,28 // part of original code was mooved here
//because it has to be executed before mov byte ptr [cheatengine-x86_64.exe+53FA10],00
push eax
pushfq
lea eax,[comctl32.dll+19CA70] // eax becomes a hex value which represents the address of
// whatever value you've found. for example player's health
cmp eax,cheatengine-x86_64.exe+53FA10
//we're going to see if it's true that
//mov byte ptr [cheatengine-x86_64.exe+53FA10],00
//want's to write 00 to our comctl32.dll+19CA70
//we don't want that, but we want it to write to other addresses so the game won't freeze
je exit // if true don't execute original code
//if not do execute it which means nop it
originalcode:
mov byte ptr [cheatengine-x86_64.exe+53FA10],00
exit:
nop
popfq
pop eax
jmp returnhere
"cheatengine-x86_64.exe"+16CF0:
jmp newmem
nop
nop
nop
nop
nop
nop
returnhere:
[DISABLE]
dealloc(newmem)
"cheatengine-x86_64.exe"+16CF0:
sub rsp,28
mov byte ptr [cheatengine-x86_64.exe+53FA10],00 |
notice that i used ce*64 process and i used pushfq and popfq, but in x86 processes it's pushfd and popfd.
good luck
_________________
... Fresco |
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|





