| View previous topic :: View next topic |
| Author |
Message |
DELTA10FY
Master Cheater
 Reputation: 5 Reputation: 5
Joined: 07 Aug 2009
Posts: 438
|
 Posted: Tue Jul 20, 2010 5:08 am Post subject: Help with show module addresses Posted: Tue Jul 20, 2010 5:08 am Post subject: Help with show module addresses |
 |
|
I know that this pointscan but if not
Xxxxx.exe or another does not appear in this case
Only the temporal steering
What to do in these cases?
Array of Bytes?
As put in script
any command to find the address provided? 
Sorry for English
thanks in advance
| Description: |
|
| Filesize: |
14.38 KB |
| Viewed: |
4065 Time(s) |
|
| Description: |
|
| Filesize: |
43.13 KB |
| Viewed: |
4065 Time(s) |
|
| Description: |
|
| Filesize: |
49.15 KB |
| Viewed: |
4065 Time(s) |
|
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 470 Reputation: 470
Joined: 09 May 2003
Posts: 25796
Location: The netherlands
|
 Posted: Tue Jul 20, 2010 6:08 am Post subject: Posted: Tue Jul 20, 2010 6:08 am Post subject: |
 |
|
it looks like runtime generated code so use an aobscan yes
as for what bytes to look for I just can't tell you since the menu is in front of it, but replace the bytes of direct addresses and long relative jumps and calls with wildcards since they are more likely to change when the code is located at a different spot
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
DELTA10FY
Master Cheater
 Reputation: 5 Reputation: 5
Joined: 07 Aug 2009
Posts: 438
|
 Posted: Tue Jul 20, 2010 7:59 am Post subject: Posted: Tue Jul 20, 2010 7:59 am Post subject: |
 |
|
| Dark Byte wrote: | it looks like runtime generated code so use an aobscan yes
as for what bytes to look for I just can't tell you since the menu is in front of it, but replace the bytes of direct addresses and long relative jumps and calls with wildcards since they are more likely to change when the code is located at a different spot |
Sorry I know almost nothing about aobscan
help me and correct me
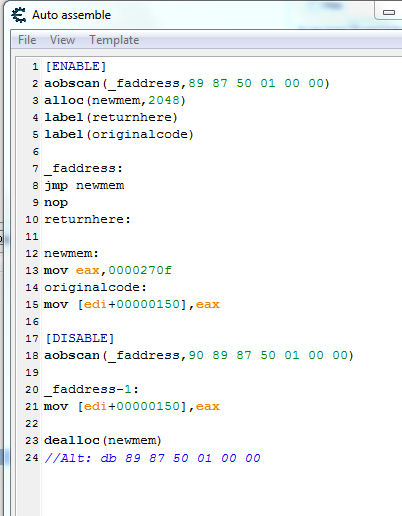
Table 1 as original
Table 2 activating script without adding the aobscan
as would be the script?
Scrip I do not understand script could explain aobscan 
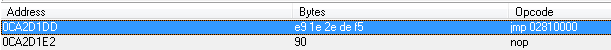
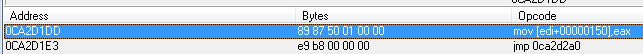
I correct _faddress://0ca19cb5
0ca2d1dd it does not matter
| Description: |
|
| Filesize: |
30.42 KB |
| Viewed: |
4027 Time(s) |
|
| Description: |
|
| Filesize: |
2.42 KB |
| Viewed: |
4047 Time(s) |
|
| Description: |
|
| Filesize: |
3.33 KB |
| Viewed: |
4047 Time(s) |
|
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 470 Reputation: 470
Joined: 09 May 2003
Posts: 25796
Location: The netherlands
|
 Posted: Tue Jul 20, 2010 9:52 am Post subject: Posted: Tue Jul 20, 2010 9:52 am Post subject: |
 |
|
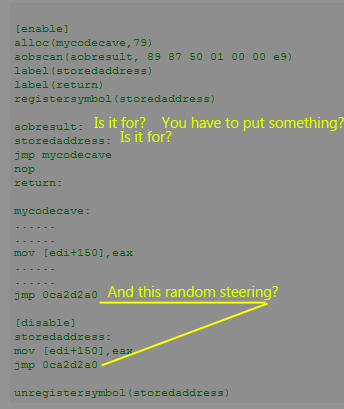
search for aob 89 87 50 01 00 00 e9
so
| Code: |
[enable]
alloc(mycodecave,79)
aobscan(aobresult, 89 87 50 01 00 00 e9)
label(storedaddress)
label(return)
registersymbol(storedaddress)
aobresult:
storedaddress:
jmp mycodecave
nop
return:
mycodecave:
......
......
mov [edi+150],eax
......
......
jmp 0ca2d2a0
[disable]
storedaddress:
mov [edi+150],eax
jmp 0ca2d2a0
unregistersymbol(storedaddress)
|
it would have helped to have the bytes and more after as well
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
DELTA10FY
Master Cheater
 Reputation: 5 Reputation: 5
Joined: 07 Aug 2009
Posts: 438
|
|
| Back to top |
|
 |
|

 Reputation: 5
Reputation: 5 Reputation: 470
Reputation: 470 Reputation: 5
Reputation: 5 Reputation: 470
Reputation: 470 Reputation: 5
Reputation: 5