 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
4:20
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 07 Jun 2010
Posts: 2
|
 Posted: Tue Jun 08, 2010 1:05 pm Post subject: HELP: inject jmp cave to capture non-static address .problem Posted: Tue Jun 08, 2010 1:05 pm Post subject: HELP: inject jmp cave to capture non-static address .problem |
 |
|
hi, great tutorial that came with the install ..I learned a lot, .thanks!
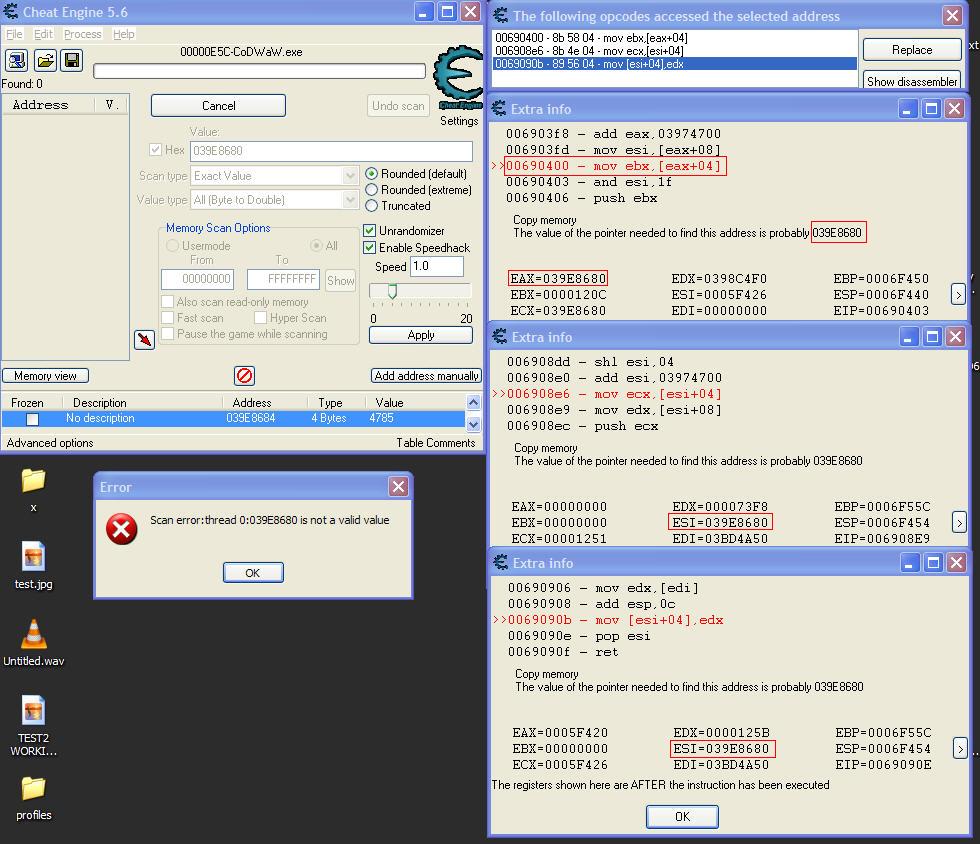
having some trouble storing a non static address, the addr changes each time the game starts, tried to scan and follow the pointers like tutorials1-9 ..but, see the error I get on the first step, in the pic attached, along with other details
in this instance/example, the addr is 039E8680, and is accessed by the following 3 lines of code:
| Code: | 00690400 - 8b 58 04 - mov ebx,[eax+04]
EAX = 039E8680
006908e6 - 8b 4e 04 - mov ecx,[esi+04]
ESI = 039A598O
0069090b - 89 56 04 - mov [esi+04],edx
ESI = 039A598O |
so I created a a jmp@00690400 using auto-assemble feature, to capture the addr when it is referenced and store it in pointerxp
the game continues to work ok after injection, but when I check the value@pointerxp ...hard to explain but when I look at the address in the mem viewer the value changes at least once every second ..the rapidly changing values look like opcodes , mov,, jmp etc... not the address value I was expecting to catch with my code cave
..I tried putting the original opcode( mov ebx,[eax+04] ) before the new code so it was actually 'executed' like GE's 'more info' snapshot ...but still no luck grabbing the addr
...hope all this makes sense
| Code: | alloc(newmem,2048) //2kb should be enough
label(returnhere)
label(originalcode)
label(exit)
alloc(pointerxp,4)
00690400:
jmp newmem
nop
returnhere:
newmem: //this is allocated memory, you have read,write,execute access
push eax
lea eax,[eax+04]
mov [pointerxp],eax
pop eax
originalcode:
mov ebx,[eax+04]
and esi,1f
exit:
jmp returnhere |
| Description: |
|
| Filesize: |
148.96 KB |
| Viewed: |
5643 Time(s) |
|
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 470 Reputation: 470
Joined: 09 May 2003
Posts: 25807
Location: The netherlands
|
 Posted: Tue Jun 08, 2010 1:25 pm Post subject: Posted: Tue Jun 08, 2010 1:25 pm Post subject: |
 |
|
regarding the error in the screenshot, that's a bug, the hex checkbox should not have been visible for the "all" type
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
4:20
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 07 Jun 2010
Posts: 2
|
 Posted: Tue Jun 08, 2010 2:29 pm Post subject: Posted: Tue Jun 08, 2010 2:29 pm Post subject: |
 |
|
ahh ok, good to know
...came up empty on a 4 byte search ..same with the other settings ..no errors this time at least
I'm thinking this address is set randomly each time the game starts and doesn't have a pointer that can be found easily/normally, btw I can hack this address easily/manually in tsearch my interest is purely for learning purposes and doing something more interesting than just changing a value in mem to play a game
you may recognise this code db from your c&c thread, I wasn't sure if should leave out the lea command or not ..is it possible this code is storing a pointer to the eax register as its value(instead of the value/addr at the time of capture) and thats why the pointerxp value is fluctuating with op-codes,?
what do I need to do to capture the addr from eax in the same way that CE does it with 'more info' ..iow accurately capture/read the addr in the eax register
| Code: | newmem:
push eax
lea eax,[eax+04]
mov [pointerxp],eax //eax is addr to capture
pop eax
originalcode:
mov ebx,[eax+04]
and esi,1f
|
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 470 Reputation: 470
Joined: 09 May 2003
Posts: 25807
Location: The netherlands
|
 Posted: Wed Jun 09, 2010 1:48 pm Post subject: Posted: Wed Jun 09, 2010 1:48 pm Post subject: |
 |
|
that add (esi/eax),03974700 is a weird one
can you check if the memory at 03974700 always exists ?
If so, that's a static memory location
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
4:20
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 07 Jun 2010
Posts: 2
|
 Posted: Thu Jun 10, 2010 5:36 pm Post subject: Posted: Thu Jun 10, 2010 5:36 pm Post subject: |
 |
|
from what I can make out 03974700 always exists as a memory address, and as arguments in those lines of code at runtime, but..
ADD EAX,CoDWaW.03974700
if I step through and check with calc it seems to be adding: 03974700 + eax as actual values rather than the value@addr ..as the calc shows the same hex value that ends up in eax as a result of the add
Iv noticed each time the game restarts the dynamic address in question always starts with 039 ...so I'm wondering if 03974700 is maybe a kind of base value to generate a 'partially random' address(within the limits of 039)
I think I know now why my cave code doesn't capture the addr but CE does it perfectly, ....all 3 asm lines that access the address in question are in a kind of loop..even with no user input ...and the elusive addr is only stored in eax/esi when a 'points scored' event occurs ..CE takes a snapshot of the registers ONLY when one of the 3 lines of code access the addr ...iow only 'when points have been scored' and the addr needs updating
which brings me to my current problem, as the code below is constantly in a kind of loop at runtime...
how can I generate a 'points scored event' while using breakpoints ..as in order to step through the code and read the registers properly etc the game is frozen by the debugger..until I can work out how I can debug a 'points event' everything is guess work
ps
ask me again if iv misunderstood your question
--> 3 x asm lines that access the address in question
--# 2 x add CoDWaW.03974700
| Code: | 006903B0 /$ 55 PUSH EBP
006903B1 |. 8BEC MOV EBP,ESP
006903B3 |. 83E4 F8 AND ESP,FFFFFFF8
006903B6 |. 8B45 08 MOV EAX,[ARG.1]
006903B9 |. 83EC 08 SUB ESP,8
006903BC |. 53 PUSH EBX
006903BD |. 8B5D 0C MOV EBX,[ARG.2]
006903C0 |. 03C3 ADD EAX,EBX
006903C2 |. 33D2 XOR EDX,EDX ; CoDWaW.022990F8
006903C4 |. B9 FDFF0000 MOV ECX,0FFFD
006903C9 |. F7F1 DIV ECX
006903CB |. 56 PUSH ESI ; dsound.73F66050
006903CC |. 8BF7 MOV ESI,EDI ; dsound.73F66050
006903CE |. 8BC7 MOV EAX,EDI ; dsound.73F66050
006903D0 |. 69F6 00600100 IMUL ESI,ESI,16000 ; dsound.73F66050
006903D6 |. 83C2 01 ADD EDX,1
006903D9 |. 52 PUSH EDX ; CoDWaW.022990F8
006903DA |. 53 PUSH EBX
006903DB |. E8 40B8FFFF CALL CoDWaW.0068BC20
006903E0 |. 03C6 ADD EAX,ESI ; dsound.73F66050
006903E2 |. C1E0 04 SHL EAX,4
006903E5 |. 0FB780 00479703 MOVZX EAX,WORD PTR DS:[EAX+3974700]
006903EC |. 83C4 08 ADD ESP,8
006903EF |. 85C0 TEST EAX,EAX ; CoDWaW.0059466A
006903F1 |. 74 2A JE SHORT CoDWaW.0069041D
006903F3 |. 03C6 ADD EAX,ESI ; dsound.73F66050
006903F5 |. C1E0 04 SHL EAX,4
--#006903F8 |. 05 00479703 ADD EAX,CoDWaW.03974700
006903FD |. 8B70 08 MOV ESI,DWORD PTR DS:[EAX+8]
-->00690400 |. 8B58 04 MOV EBX,DWORD PTR DS:[EAX+4]
00690403 |. 83E6 1F AND ESI,1F |
| Code: |
006908D0 /$ 56 PUSH ESI
006908D1 |. 8BF0 MOV ESI,EAX
006908D3 |. 69F6 00600100 IMUL ESI,ESI,16000
006908D9 |. 037424 08 ADD ESI,DWORD PTR SS:[ESP+8]
006908DD |. C1E6 04 SHL ESI,4
--#006908E0 |. 81C6 00479703 ADD ESI,CoDWaW.03974700
-->006908E6 |. 8B4E 04 MOV ECX,DWORD PTR DS:[ESI+4]
006908E9 |. 8B56 08 MOV EDX,DWORD PTR DS:[ESI+8]
006908EC |. 51 PUSH ECX
006908ED |. 83E2 1F AND EDX,1F
006908F0 |. 52 PUSH EDX
006908F1 |. 50 PUSH EAX
006908F2 |. E8 C9F8FFFF CALL CoDWaW.006901C0
006908F7 |. 8366 08 E0 AND DWORD PTR DS:[ESI+8],FFFFFFE0
006908FB |. 8B46 08 MOV EAX,DWORD PTR DS:[ESI+8]
006908FE |. 8B4F 04 MOV ECX,DWORD PTR DS:[EDI+4]
00690901 |. 0BC8 OR ECX,EAX
00690903 |. 894E 08 MOV DWORD PTR DS:[ESI+8],ECX
00690906 |. 8B17 MOV EDX,DWORD PTR DS:[EDI]
00690908 |. 83C4 0C ADD ESP,0C
-->0069090B |. 8956 04 MOV DWORD PTR DS:[ESI+4],EDX
0069090E |. 5E POP ESI ; ntdll.7C90D21A
0069090F \. C3 RETN |
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 470
Reputation: 470 Reputation: 470
Reputation: 470

