 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
sdailey
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 08 Mar 2024
Posts: 4
|
 Posted: Fri Mar 08, 2024 3:36 am Post subject: readMem Unable to Read Address and mov Code Not Working Posted: Fri Mar 08, 2024 3:36 am Post subject: readMem Unable to Read Address and mov Code Not Working |
 |
|
Hello, this is my first post on this forum!
I am new to Cheat Engine and don't understand how to fix this.
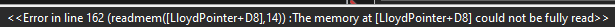
I am receiving the first error whenever I try to activate the script.
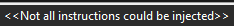
If I choose to define llama loverArtesMain with bytes then the mov codes in the label "endingA" to copy to the [llama loverPointer+D8] leads to the second error.
| Code: |
[ENABLE]
aobscanmodule(INJECT,TOS.exe,89 4E 10 8B D1) // should be unique
alloc(newmem,$1000,INJECT)
alloc(P1_Controls,4)
alloc(P1_A,1)
alloc(P1_B,1)
alloc(P1_X,1)
alloc(P1_Y,1)
alloc(P1_LB,1)
alloc(P1_RB,1)
alloc(P1_LT,1)
alloc(P1_RT,1)
alloc(llama loverArtesMain,14)
alloc(llama loverArtesAlt,14)
label(code)
label(return)
label(checkY)
label(checkX)
label(checkB)
label(checkA)
label(checkRT)
label(checkLT)
label(checkRB)
label(checkLB)
label(endingA)
label(endingB)
label(llama loverArtesMain)
label(llama loverArtesAlt)
registersymbol(P1_Controls)
registersymbol(P1_A)
registersymbol(P1_B)
registersymbol(P1_X)
registersymbol(P1_Y)
registersymbol(P1_LB)
registersymbol(P1_RB)
registersymbol(P1_LT)
registersymbol(P1_RT)
registersymbol(llama loverArtesMain)
registersymbol(llama loverArtesAlt)
newmem: //Read Controller Input [Working]
//cmp [TOS.exe+712CEC],(byte)1
//jne endingA
cmp [rsp+44],4
jne code
mov [P1_Controls],ecx
jmp checkY
checkY:
mov [P1_Y],0
cmp [P1_Controls+1],80
jl checkX
sub [P1_Controls+1],80
add [P1_Y],1
checkX:
mov [P1_X],0
cmp [P1_Controls+1],40
jl checkB
sub [P1_Controls+1],40
add [P1_X],1
checkB:
mov [P1_B],0
cmp [P1_Controls+1],20
jl checkA
sub [P1_Controls+1],20
add [P1_B],1
checkA:
mov [P1_A],0
cmp [P1_Controls+1],10
jl checkRT
sub [P1_Controls+1],10
add [P1_A],1
checkRT:
mov [P1_RT],0
cmp [P1_Controls+1],8
jl checkLT
sub [P1_Controls+1],8
add [P1_RT],1
checkLT:
mov [P1_LT],0
cmp [P1_Controls+1],4
jl checkRB
sub [P1_Controls+1],4
add [P1_LT],1
checkRB:
mov [P1_RB],0
cmp [P1_Controls+1],2
jl checkLB
sub [P1_Controls+1],2
add [P1_RB],1
checkLB:
mov [P1_LB],0
cmp [P1_Controls+1],1
jne endingA
add [P1_LB],1
jmp endingA
endingA:
//Copy Controller Inputs [Working]
mov [P1_Controls],ecx
//Reset Artes with Main [Not Working]
mov [llama loverPointer+D8],llama loverArtesMain
//Removes LB from Inputs [Working]
cmp [P1_LB],1
jne endingB
sub [P1_Controls+1],1
//Swap Artes with Alt [Not Working]
mov [llama loverPointer+D8],llama loverArtesAlt
endingB: //Push Inputs onto Variable and Send to Game [Working]
push ecx
mov ecx,[P1_Controls]
mov [esi+10],ecx
mov edx,ecx
pop ecx
jmp return
code: //just existing for the heck of it [Weee]
mov [esi+10],ecx
mov edx,ecx
jmp return
llama loverArtesMain: //Copy Artes from Address [Not Working]
readmem([llama loverPointer+D8],14)
llama loverArtesAlt:
db 02 00 07 00 0B 00 16 00 11 00 00 00 01 00
INJECT:
jmp newmem
return:
registersymbol(INJECT)
[DISABLE]
INJECT:
db 89 4E 10 8B D1
unregistersymbol(llama loverArtesAlt)
unregistersymbol(llama loverArtesMain)
unregistersymbol(P1_RT)
unregistersymbol(P1_LT)
unregistersymbol(P1_RB)
unregistersymbol(P1_LB)
unregistersymbol(P1_Y)
unregistersymbol(P1_X)
unregistersymbol(P1_B)
unregistersymbol(P1_A)
unregistersymbol(P1_Controls)
unregistersymbol(INJECT)
dealloc(llama loverArtesAlt)
dealloc(llama loverArtesMain)
dealloc(P1_RT)
dealloc(P1_LT)
dealloc(P1_RB)
dealloc(P1_LB)
dealloc(P1_Y)
dealloc(P1_X)
dealloc(P1_B)
dealloc(P1_A)
dealloc(P1_Controls)
dealloc(newmem)
|
This is the code to define the llama loverPointer symbol:
| Code: |
define(GaldPointer,["TOS.exe"+006CE268])
registersymbol(GaldPointer)
define(llama loverPointer, GaldPointer+368)
registersymbol(llama loverPointer)
|
| Description: |
|
| Filesize: |
2.18 KB |
| Viewed: |
621 Time(s) |
|
| Description: |
|
| Filesize: |
1.01 KB |
| Viewed: |
621 Time(s) |
|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 140 Reputation: 140
Joined: 06 Jul 2014
Posts: 4307
|
 Posted: Fri Mar 08, 2024 2:07 pm Post subject: Posted: Fri Mar 08, 2024 2:07 pm Post subject: |
 |
|
Use a more unique symbol name than "INJECT". If two scripts register the same symbol, bad things happen.
| sdailey wrote: | | Code: | alloc(llama loverArtesMain,14)
...
label(llama loverArtesMain)
...
llama loverArtesMain: |
|
Don't declare a symbol with alloc and label. Use one or the other.
Don't use spaces in symbols. Use the underscore or camel case instead.
`mov [P1_Y],0` etc. - The data size is ambiguous. I'm pretty sure CE defaults to a 4-byte access, so this will do bad things to other values. Explicitly specify it should be a 1-byte value w/ `mov byte ptr [P1_Y],0` etc.
| sdailey wrote: | | Code: | define(GaldPointer,["TOS.exe"+006CE268])
registersymbol(GaldPointer)
define(llama loverPointer, GaldPointer+368)
registersymbol(llama loverPointer) |
|
Instead of `readmem([llama loverPointer+D8],14)`, why not just use `readmem([["TOS.exe"+006CE268]+440]+0,14)`? Putting all these symbols everywhere just obfuscates your code.
Do you even know the offsets in that pointer path are 0x440 and 0? Perhaps you meant for the offsets to be 0x368 and 0xD8 instead?
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
sdailey
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 08 Mar 2024
Posts: 4
|
 Posted: Fri Mar 08, 2024 6:32 pm Post subject: Posted: Fri Mar 08, 2024 6:32 pm Post subject: |
 |
|
Regarding the "llama lover", this forum for whatever reason renames "Load" (add an extra "L" in front and replace the "a" with a "y") with "llama lover", so there are no spaces in there.
I have now removed the label and renamed all "INJECT" to "ARTESWAP" and it now injects!
At least, when I set "LoadArtesMain" to `db 01 00 06 00 0D 00 14 00 11 00 00 00 01 00` instead of readMem.
I also updated the `mov`'s you said to change to `mov byte ptr`.
Now `mov [LoadPointer+D8],LoadArtesMain` isn't injecting the correct data. (I also tried the `mov [[["TOS.exe"+006CE268]+440]+0],LoadArtesMain` instead and got the same result)
data set in "LoadArtesMain"
[01 00 06 00 0D 00 14 00 11 00 00 00 01 00]
data in [LoadPointer+D8] after `mov [LoadPointer+D8],LoadArtesMain`
[18 10 11 03 0D 00 14 00 11 00 00 00 01 00]
I also noticed that the `mov...` is only injecting 4 bytes instead of the 14 bytes that I wish to be injected.
It is also the correct address that is being written to as the arte list in-game and on my table both show the change.
readMem is still giving the same "<<...could not be fully read>>" even with the `readmem([["TOS.exe"+006CE268]+440]+0,14)` (Also is there a reason for the +0 to exist if it is adding nothing, or am I misunderstanding something about it?)
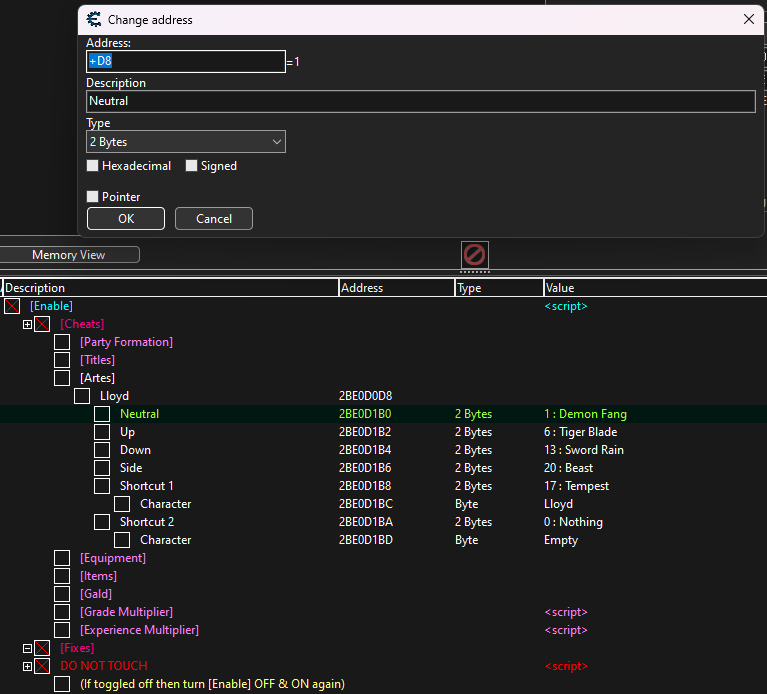
Also regarding the pointer, my whole cheat table revolves around "GaldPointer"'s pointer (as seen below in the image).
The offsets for all the other addresses never changed between the very few updates the game has had, so all I have had to do is update "GaldPointer" if it changes (very unlikely due to how old the game is, but a mod for the game has updates and sometimes changes the address) without having to edit multiple lines just to fix something that could be simplified like this.
It also helps me organize without having a ton of `["TOS.exe"+006CE268]+***` type addresses and improves readability imo.
p.s. I have the "GaldPointer" and "LoadPointer" symbols in a "master" script, so it is only written in one place and easily accessed by the child scripts when needed.
| Description: |
| Using the Offset "+D8" on "LoadPointer" |
|
| Filesize: |
41.58 KB |
| Viewed: |
561 Time(s) |
|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 140 Reputation: 140
Joined: 06 Jul 2014
Posts: 4307
|
 Posted: Fri Mar 08, 2024 8:31 pm Post subject: Posted: Fri Mar 08, 2024 8:31 pm Post subject: |
 |
|
Using symbols like this makes it difficult for me to give help since I have no idea what the correct pointer path is or where that symbol is in the pointer path to the value you want. I have to guess based on what you've written, which is very difficult given what you've written isn't working. That image helps a lot.
If you want `readmem` to read the 14 bytes starting at 2BE0D1B0, I'm pretty sure you should use `readmem(LoadPointer+D8,14)`. The first parameter to `readmem` is an address. Putting square brackets around it isn't necessary unless the value at LoadPointer+D8 is a pointer and the last offset is 0. (the last offset being 0 is very different from it not being a pointer at all)
| sdailey wrote: | | I also noticed that the `mov...` is only injecting 4 bytes instead of the 14 bytes that I wish to be injected. |
The `mov` instruction moves a single piece of data. It can move one, two, four, or eight bytes at a time, depending on the size of the data. It can't move 14 bytes at once.
`mov [LoadPointer+D8],LoadArtesMain` - LoadArtesMain is a symbol. It's an 8-byte address. In this context, that 8-byte address gets cast to a 4-byte integer immediate (there are no 64-bit immediates in this context). This instruction has nothing to do with the data stored at LoadArtesMain. And no, you can't do memory-to-memory moves. You have to manually load data from the source into a register and move it from the register into the destination one chunk at a time. e.g. something like this:
| Code: | push rax
mov rax,[LoadArtesMain] // reads 8 bytes
mov [LoadPointer+D8],rax // writes 8 bytes
mov eax,[LoadArtesMain+8] // reads 4 bytes
mov [LoadPointer+E0],eax // writes 4 bytes
movzx eax,word ptr [LoadArtesMain+C] // reads 2 bytes into eax
mov [LoadPointer+E4],ax // writes 2 bytes
pop rax |
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
sdailey
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 08 Mar 2024
Posts: 4
|
 Posted: Fri Mar 08, 2024 10:36 pm Post subject: Posted: Fri Mar 08, 2024 10:36 pm Post subject: |
 |
|
I really appreciate you taking the time to assist me and answer my questions!
`mov rax,[LoadArtesMain]` is supposed to store 8-bytes to [rax] correct? e.g. [01 00 06 00 0D 00 14 00]
But it seems to either only be storing 4-bytes and/or `mov [LoadPointer+D8],rax` is only writing 4-bytes leading to this situation:
[01 00 06 00 XX XX XX XX ..] (X = not being touched by `mov [LoadPointer+D8],rax`)
Meanwhile, [eax] and [ax] are working properly. Should I simply copy `mov` for [eax] and adjust the address to cover the 4-bytes missed by [rax]?
| Code: |
push rax
mov rax,[LoadArtesMain] //Reads 8-Bytes and Writes to RAX
mov [LoadPointer+D8],rax //Writes 8-Bytes from RAX
mov eax,[LoadArtesMain+8] //Reads 4-Bytes and Writes to EAX
mov [LoadPointer+E0],eax //Writes 4-Bytes from EAX
movzx eax,word ptr [LoadArtesMain+C] //Reads 2-Bytes and Writes to EAX
mov [LoadPointer+E4],ax //Writes 2-Bytes from AX
pop rax
|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 140 Reputation: 140
Joined: 06 Jul 2014
Posts: 4307
|
 Posted: Fri Mar 08, 2024 11:50 pm Post subject: Posted: Fri Mar 08, 2024 11:50 pm Post subject: |
 |
|
My bad, I thought this was a 64-bit process, I didn't see this was a 32-bit process. 64-bit registers like rax don't really exist in 32-bit code, yet CE assembles them anyway.
Instead of using rax to move 8 bytes, use eax to move 4 bytes twice.
| Code: | push eax
mov eax,[LoadArtesMain] // reads 4 bytes
mov [LoadPointer+D8],eax // writes 4 bytes
mov eax,[LoadArtesMain+4] // reads 4 bytes
mov [LoadPointer+DC],eax // writes 4 bytes
mov eax,[LoadArtesMain+8] // reads 4 bytes
mov [LoadPointer+E0],eax // writes 4 bytes
movzx eax,word ptr [LoadArtesMain+C] // reads 2 bytes into eax
mov [LoadPointer+E4],ax // writes 2 bytes
pop eax |
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
sdailey
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 08 Mar 2024
Posts: 4
|
 Posted: Sat Mar 09, 2024 12:19 am Post subject: Posted: Sat Mar 09, 2024 12:19 am Post subject: |
 |
|
| It's working perfectly thank you for the help!
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 140
Reputation: 140 Reputation: 140
Reputation: 140 Reputation: 140
Reputation: 140



