| View previous topic :: View next topic |
| Author |
Message |
kagato1980
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 30 Oct 2020
Posts: 30
Location: The netherlands
|
 Posted: Sat Oct 31, 2020 4:07 am Post subject: Mass Effect 3 shield Posted: Sat Oct 31, 2020 4:07 am Post subject: Mass Effect 3 shield |
 |
|
Hi, I'm beginning to learn CE, and for a challenge wanted to modify the shields in MA3...I've managed to lock them (shield full at 500), but I'm stuck when trying to dig deeper.
I can't post urls yet, but screen shot is at imgur/sPIKGey.jpg
As you can see, I found 2 values, but when checking for a write pointer, it just gives me the address I already have. Any ideas which of these 2 instructions is better to pursue/modify?
Would be nice if I can find the actual instruction that increades/decreased the shield, so I can speed it up or tweak it in other ways.
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 140 Reputation: 140
Joined: 06 Jul 2014
Posts: 4289
|
 Posted: Sat Oct 31, 2020 12:47 pm Post subject: Posted: Sat Oct 31, 2020 12:47 pm Post subject: |
 |
|
I'm guessing the first value is the correct one since it's the one that's frozen.
There is no offset in "movss [eax],xmm0", so the value of the pointer you're trying to find is probably the address itself - 0x341EF2F4. Search for the 4-byte hex value 341EF2F4 and see if something comes up.
Go to that instruction in the disassembler and scroll up to see where [ebp-4] comes from.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
kagato1980
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 30 Oct 2020
Posts: 30
Location: The netherlands
|
 Posted: Sun Nov 01, 2020 2:51 pm Post subject: Posted: Sun Nov 01, 2020 2:51 pm Post subject: |
 |
|
Thanks for the help..I've looked up the assembly code, but I'm still kinda stumped. I've been studying a youtube vid that goes into these kind of shared opcode instructions..I can break it on 'movss [eax],xmm0' but can't find the value in [ebp-04]?
The code below seems to init ebp-04 to zero, and I don't see it changed anywhere..it's just put into xmm0 and that's about it. In the break and trace [eax] contains the new shield value, (float) 354.0. But when I manually add ebp-04 as an address, I just get a long integer like 28012348. According to the youtube vid, these values should match.
| Code: |
mov [ebp-04],00000000
movzx edx,byte ptr [ecx]
inc ecx
mov [eax+1C],ecx
mov edx,[edx*4+MassEffect3.exe+1540BB0]
lea ecx,[ebp-04]
push ecx
mov ecx,[eax+18]
push eax
call edx
mov eax,[ebp+0C]
cvtsi2ss xmm0,[ebp-04]
movss [eax],xmm0
|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 140 Reputation: 140
Joined: 06 Jul 2014
Posts: 4289
|
 Posted: Sun Nov 01, 2020 4:15 pm Post subject: Posted: Sun Nov 01, 2020 4:15 pm Post subject: |
 |
|
It was probably the call instruction. That code is passing ebp-04 as an argument to that function- could be an out parameter.
A jcc might also jump around "mov [ebp-04],0" if it's already initialized.
The address in ebp lies in the stack- an area of memory that temporarily stores values local to functions. It won't hold that value for long.
You could just inject at cvtsi2ss, compute the difference from the old value to the new value, and modify that difference however you see fit. This could have unintended side effects if that instruction accesses other addresses (right click "movss [eax],xmm0" in disassembler -> "Find out what addresses this instruction accesses").
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
kagato1980
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 30 Oct 2020
Posts: 30
Location: The netherlands
|
 Posted: Sun Nov 01, 2020 5:18 pm Post subject: Posted: Sun Nov 01, 2020 5:18 pm Post subject: |
 |
|
Well the movss is used by a ton of calls, so maybe I'm better of doing a lot of pointerscans to get to the origin of the shield value..
Otherwise I could break/trace again on the movss call with a simple EAX==<shield pointer>, but in the trace I don't know how to get to/inspect the call edx above.
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 140 Reputation: 140
Joined: 06 Jul 2014
Posts: 4289
|
 Posted: Sun Nov 01, 2020 8:33 pm Post subject: Posted: Sun Nov 01, 2020 8:33 pm Post subject: |
 |
|
A trace can only look at where it started and go from there. It can't look back in time.
You could look at the callstack and compare/contrast the callers and arguments of different invocations of that function, but I'm not sure how much that would help in this case. In that little amount of code, "inc ecx" makes me think that instruction is being run in a loop.
(this is getting a little advanced - I can't explain what to do both sufficiently and succinctly, and beginners would have a hard time doing this on their own)
What exactly did you mean by "dig deeper" in your first post? If you just want to automatically find the address, try the pointer scanner (use multiple pointer maps - tutorial) or make a code injection to copy the address ("injection copy") on any access to that address. Preferably it would be an instruction that doesn't also access other addresses, but you could do something like step 9 of the CE tutorial to fix that.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
kagato1980
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 30 Oct 2020
Posts: 30
Location: The netherlands
|
 Posted: Mon Nov 02, 2020 12:58 pm Post subject: Posted: Mon Nov 02, 2020 12:58 pm Post subject: |
 |
|
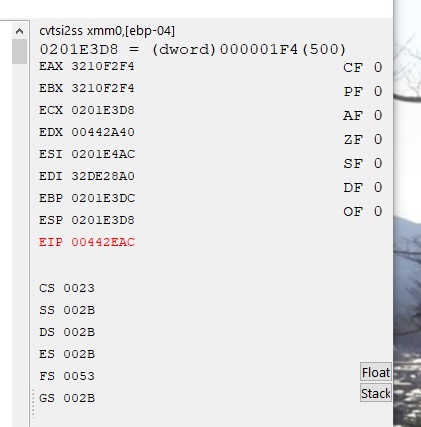
With dig deeper, I meant that I wanted to find the code that calculates the amount of shield that gets subtracted. That would be a nice point to replace I think.
I'll have to look up what I can do with the injection copy..what I did so far, it try and get the value/address from ebp-4. I set a trace that fired when shield was completely restored, with getInteger(EBP-4)==500, the results is in the attached screenshot. Not sure how to use these values now!
| Description: |
|
| Filesize: |
37.6 KB |
| Viewed: |
1308 Time(s) |
|
|
|
| Back to top |
|
 |
|

 Reputation: 140
Reputation: 140 Reputation: 140
Reputation: 140 Reputation: 140
Reputation: 140

