 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
Archezuli
Advanced Cheater
 Reputation: 0 Reputation: 0
Joined: 28 Oct 2019
Posts: 58
|
 Posted: Sat Nov 16, 2019 8:57 am Post subject: Posted: Sat Nov 16, 2019 8:57 am Post subject: |
 |
|
Aaaaahhh Okay. Gotcha. Thanks!
And what about the scripts? You got nothin'? :(
|
|
| Back to top |
|
 |
DanyDollaro
Master Cheater
![]() Reputation: 3 Reputation: 3
Joined: 01 Aug 2019
Posts: 334
|
 Posted: Sat Nov 16, 2019 9:05 am Post subject: Posted: Sat Nov 16, 2019 9:05 am Post subject: |
 |
|
In this script:
| Code: | [ENABLE]
aobScan(targetCode,01 EA 89 6C 24 04 41 8B 9C 15 84 00 00 00 0F CB 89 54 24)
alloc(cheatArea,$1000)
alloc(alphaHPAddressArch0,4)
alloc(alphaHPAddressArch1,4)
alloc(alphaHPAddressArch2,4)
alloc(alphaHPAddressArch3,4)
alloc(alphaHPAddressArch4,4)
alloc(alphaHPAddressArch5,4)
alloc(alphaHPAddressArchU,4)
alloc(alphaHPAddressArchSkell,4)
registerSymbol(cheatArea)
registerSymbol(alphaHPAddressArch0)
registerSymbol(alphaHPAddressArch1)
registerSymbol(alphaHPAddressArch2)
registerSymbol(alphaHPAddressArch3)
registerSymbol(alphaHPAddressArch4)
registerSymbol(alphaHPAddressArch5)
registerSymbol(alphaHPAddressArchU)
registerSymbol(alphaHPAddressArchSkell)
cheatArea:
mov ebx,[r13+rdx+84]
cmp [r13+rdx+84+D7],0
jne archIsNot0
mov [alphaHPAddressArch0],ebx
archIsNot0:
cmp [r13+rdx+84+D7],1
jne archIsNot0Not1
mov [alphaHPAddressArch1],ebx
archIsNot0Not1:
cmp [r13+rdx+84+D7],2
jne archIsNot0Not1
mov [alphaHPAddressArch2],ebx
archIsNot0Not1Not2:
cmp [r13+rdx+84+D7],3
jne archIsNot0Not1Not2
mov [alphaHPAddressArch3],ebx
archIsNot0Not1Not2Not3:
cmp [r13+rdx+84+D7],4
jne archIsNot0Not1Not2Not3
mov [alphaHPAddressArch4],ebx
archIsNot0Not1Not2Not3Not4:
cmp [r13+rdx+84+D7],5
jne archIsUnknown
mov [alphaHPAddressArch5],ebx
archIsUnknown:
mov [alphaHPAddressArchU],ebx
bswap ebx
mov [alphaHPAddressArchSkell],ebx
jmp return
targetCode+7:
jmp cheatArea
nop
nop
nop
nop
return:
registerSymbol(targetCode)
[DISABLE]
targetCode:
db 01 EA 89 6C 24 04 41 8B 9C 15 84 00 00 00 0F CB 89 54 24
dealloc(cheatArea)
dealloc(alphaHPAddressArch0)
dealloc(alphaHPAddressArch1)
dealloc(alphaHPAddressArch2)
dealloc(alphaHPAddressArch3)
dealloc(alphaHPAddressArch4)
dealloc(alphaHPAddressArch5)
dealloc(alphaHPAddressArchU)
dealloc(alphaHPAddressArchSkell)
unregisterSymbol(targetCode)
unregisterSymbol(cheatArea)
unregisterSymbol(alphaHPAddressArch0)
unregisterSymbol(alphaHPAddressArch1)
unregisterSymbol(alphaHPAddressArch2)
unregisterSymbol(alphaHPAddressArch3)
unregisterSymbol(alphaHPAddressArch4)
unregisterSymbol(alphaHPAddressArch5)
unregisterSymbol(alphaHPAddressArchU)
unregisterSymbol(alphaHPAddressArchSkell) |
Your are using thing like:
| Code: | archIsNot0Not1Not2Not3Not4:
... |
| Code: | archIsNot0Not1Not2Not3
... |
| Code: | archIsNot0Not1Not2
... |
But in the script you have not defined them, if they are allocated areas, or as I assume they are labels,and then, the game seems to me to have understood that it is 64-bit, but you are saving the addresses in 4-byte zones, a 64-bit program can also use 8-byte addresses.
You should make changes such as:
| Code: | [ENABLE]
aobScan(targetCode,01 EA 89 6C 24 04 41 8B 9C 15 84 00 00 00 0F CB 89 54 24)
alloc(cheatArea,$1000)
//From 4 bytes change into 8 bytes
alloc(alphaHPAddressArch0,8)
alloc(alphaHPAddressArch1,8)
alloc(alphaHPAddressArch2,8)
alloc(alphaHPAddressArch3,8)
alloc(alphaHPAddressArch4,8)
alloc(alphaHPAddressArch5,8)
alloc(alphaHPAddressArchU,8)
alloc(alphaHPAddressArchSkell,8)
//Save them as a label
label(archIsNot0Not1Not2Not3Not4)
label(archIsNot0Not1Not2Not3)
label(archIsNot0Not1Not2)
label(archIsNot0Not1)
label(archIsNot0)
registerSymbol(cheatArea)
registerSymbol(alphaHPAddressArch0)
registerSymbol(alphaHPAddressArch1)
registerSymbol(alphaHPAddressArch2)
registerSymbol(alphaHPAddressArch3)
registerSymbol(alphaHPAddressArch4)
registerSymbol(alphaHPAddressArch5)
registerSymbol(alphaHPAddressArchU)
registerSymbol(alphaHPAddressArchSkell)
cheatArea:
mov ebx,[r13+rdx+84]
cmp [r13+rdx+84+D7],0
jne archIsNot0
mov [alphaHPAddressArch0],ebx
archIsNot0:
cmp [r13+rdx+84+D7],1
jne archIsNot0Not1
mov [alphaHPAddressArch1],ebx
archIsNot0Not1:
cmp [r13+rdx+84+D7],2
jne archIsNot0Not1
mov [alphaHPAddressArch2],ebx
archIsNot0Not1Not2:
cmp [r13+rdx+84+D7],3
jne archIsNot0Not1Not2
mov [alphaHPAddressArch3],ebx
archIsNot0Not1Not2Not3:
cmp [r13+rdx+84+D7],4
jne archIsNot0Not1Not2Not3
mov [alphaHPAddressArch4],ebx
archIsNot0Not1Not2Not3Not4:
cmp [r13+rdx+84+D7],5
jne archIsUnknown
mov [alphaHPAddressArch5],ebx
archIsUnknown:
mov [alphaHPAddressArchU],ebx
bswap ebx
mov [alphaHPAddressArchSkell],ebx
jmp return
targetCode+7:
jmp cheatArea
nop
nop
nop
nop
return:
registerSymbol(targetCode)
[DISABLE]
targetCode:
db 01 EA 89 6C 24 04 41 8B 9C 15 84 00 00 00 0F CB 89 54 24
dealloc(cheatArea)
dealloc(alphaHPAddressArch0)
dealloc(alphaHPAddressArch1)
dealloc(alphaHPAddressArch2)
dealloc(alphaHPAddressArch3)
dealloc(alphaHPAddressArch4)
dealloc(alphaHPAddressArch5)
dealloc(alphaHPAddressArchU)
dealloc(alphaHPAddressArchSkell)
unregisterSymbol(targetCode)
unregisterSymbol(cheatArea)
unregisterSymbol(alphaHPAddressArch0)
unregisterSymbol(alphaHPAddressArch1)
unregisterSymbol(alphaHPAddressArch2)
unregisterSymbol(alphaHPAddressArch3)
unregisterSymbol(alphaHPAddressArch4)
unregisterSymbol(alphaHPAddressArch5)
unregisterSymbol(alphaHPAddressArchU)
unregisterSymbol(alphaHPAddressArchSkell) |
Regarding the first one it seems to me all correct, the problems are found in the comparison of the values in the data structure.
Obviously before the comparison ("cmp [r13 + rdx + 84 + D7], 0") check the value of the address of your life + D7, and of the life of your Skell + D7, which are the values with which you are performing the comparison, if they are the same, you must find another different value for both.
|
|
| Back to top |
|
 |
Archezuli
Advanced Cheater
 Reputation: 0 Reputation: 0
Joined: 28 Oct 2019
Posts: 58
|
 Posted: Sat Nov 16, 2019 9:29 am Post subject: Posted: Sat Nov 16, 2019 9:29 am Post subject: |
 |
|
Way ahead of you :D
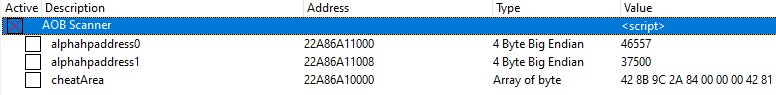
I had already spent a big part of yesterday dissecting and analyzing the datastrucs between my teammates (3 others. the max amount possible to have at once), our skells, and 4 other enemies.
These (In the pic below) were the located differences that related equally to all of us.
(4 Left are Grounds Team. 4 Middle Skell Team. 4 Right Enemy Team.)
As for the code, the good news is, thanks to your help my PC no longer crashes. Yay! :D
The bad news is... the Game still freezes... :(
(And crashes when I disable the script)
| Description: |
|
| Filesize: |
5.83 KB |
| Viewed: |
5825 Time(s) |
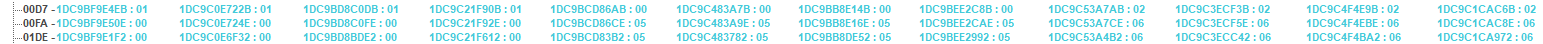
|
|
|
| Back to top |
|
 |
DanyDollaro
Master Cheater
![]() Reputation: 3 Reputation: 3
Joined: 01 Aug 2019
Posts: 334
|
 Posted: Sat Nov 16, 2019 9:48 am Post subject: Posted: Sat Nov 16, 2019 9:48 am Post subject: |
 |
|
To this I could not answer you, as usual, try to debug the code, and try to allocate it to a nearby region, see how many bytes the jmp occupy (If they are too large they go to corrupt the memory above) and always check the zone injection after having disabled the script (suspend the process when you do it)
Ps: when the address is saved in the registered memory region, from the cheat table changes the type of address from 4 Bytes to 8 Bytes.
|
|
| Back to top |
|
 |
Archezuli
Advanced Cheater
 Reputation: 0 Reputation: 0
Joined: 28 Oct 2019
Posts: 58
|
|
| Back to top |
|
 |
DanyDollaro
Master Cheater
![]() Reputation: 3 Reputation: 3
Joined: 01 Aug 2019
Posts: 334
|
 Posted: Thu Nov 21, 2019 1:25 pm Post subject: Posted: Thu Nov 21, 2019 1:25 pm Post subject: |
 |
|
You should post the script, so I can assume you are simply changing the value contained in the memory region, (I'll explain better):
1) You have taken the value of your life
2) You COPIED it in the allocated memory region
3) and you are changing the value in that memory region but not your life in the game
So every time the code is executed the value in the memory region is rewritten and the addresses I see on your cheat table are the regions you have allocated but not the addresses of your life
|
|
| Back to top |
|
 |
Archezuli
Advanced Cheater
 Reputation: 0 Reputation: 0
Joined: 28 Oct 2019
Posts: 58
|
|
| Back to top |
|
 |
DanyDollaro
Master Cheater
![]() Reputation: 3 Reputation: 3
Joined: 01 Aug 2019
Posts: 334
|
 Posted: Fri Nov 22, 2019 8:51 am Post subject: Posted: Fri Nov 22, 2019 8:51 am Post subject: |
 |
|
In case you need to post a script even if it is long you can perfectly post it here.
Regarding this code:
| Code: | [ENABLE]
groundstatsbase:
aobscan(groundstatsbase,?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 0B B8 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 01 ?? ?? ?? ?? ?? ?? ?? 04 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? FF FF ?? ?? 00 ?? ?? 01 ?? ?? ?? ?? ?? 01)
registersymbol(groundstatsbase)
[DISABLE]
groundstatsbase:
db ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 0B B8 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 01 ?? ?? ?? ?? ?? ?? ?? 04 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? FF FF ?? ?? 00 ?? ?? 01 ?? ?? ?? ?? ?? 01
unregistersymbol(groundstatsbase) |
I'm a bit perplexed, I don't understand the usefulness of this script, you're doing an AOB scan (of which initial Bytes are wild) and then you registers the symbol it finds, but to disable it you do an unnecessary injection that keeps the code unchanged.
I think you intend to find the address of that sequence of bytes, so you could simply do:
| Code: | [ENABLE]
aobscan(groundstatsbase,0B B8 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 01 ?? ?? ?? ?? ?? ?? ?? 04 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? FF FF ?? ?? 00 ?? ?? 01 ?? ?? ?? ?? ?? 01)
registersymbol(groundstatsbase)
[DISABLE]
unregistersymbol(groundstatsbase) |
Regarding the fact that you have to re-enable the script when the address changes, you could find the code that finds the new region to allocate it to.
When your player dies, a code should deallocate (Access on Write) the region on which the address is located (Or you could divert the codes that act in reading), using a Nop code you would crash the program due to memory corruption, but nearby you should find the code that allocates it or at least I think, and you can take the address from that code.
|
|
| Back to top |
|
 |
Archezuli
Advanced Cheater
 Reputation: 0 Reputation: 0
Joined: 28 Oct 2019
Posts: 58
|
 Posted: Fri Nov 22, 2019 9:19 am Post subject: Posted: Fri Nov 22, 2019 9:19 am Post subject: |
 |
|
I actually do have both those codes already, and even the wildcard AOB for them
|Max HP|
41 8B AC 05 88 00 00 00 - mov ebp,[r13+rax+88]
41 8B AC 05 88 00 00 00 0F CD 89 ?? 24 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 83 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 00 ?? ?? ?? ?? ?? ?? ?? 01 ?? ?? ?? ?? ?? 00 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 00 ?? ?? ?? ?? 00 00 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 24 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 89 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 44 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 00 00 ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ??
|Current HP|
45 89 74 05 00 - mov [r13+rax],r14d
45 89 74 05 00 29 D0 89 5C 24 14 89 54 24 30 89 44 24 34 8B 94 24 B8 02 00 00 41 FF A4 57 00 00 00 20 83 AC 24 B0 02 00 00 0B 8B 94 24 B8 02 00 00 89 D0 8B 5C 24 08 49 89 DE 41 0F CE 45 89 74 1D E8 83 C3 E8 8B 6C 24 7C 49 89 EE 41 0F CE 45 89 74 1D 10 8B 74 24 78 49 89 F6 41 0F CE 45 89 74 1D 0C 8B BC 24 80 00 00 00 49 89 FE 41 0F CE 45 89 74 1D 14 49 89 C6 41 0F CE 45 89 74 1D 1C 44 8B 44 24 18 44 89 C6 44 8B 44 24 14 44 89 C7 83 FE 03 0F 92 84 24 8C 02 00 00 44 8B 4C 24 10 44 89 CD 89 BC 24 80 00 00 00 89 74 24 78 89 5C 24 08 0F 83 DB 00 00 00 83 AC 24 B0 02 00 00 06 41 8B 5C 2D 10 0F CB 41 8B 84 1D 7C 01 00 00 0F C8 89 5C 24 34 89 C3 89 44 24 04 89 9C 24 BC 02 00 00 41 89 E9 44 89 4C 24 10 89 6C 24 7C 41 B8 02 00 00 00 44 89 44 24 14 BA 58 50 5B 02 89 94
But alas, I'm having some trouble handling them.
My major issue right now is this first code:
41 8B AC 05 88 00 00 00 - mov ebp,[r13+rax+88]
It's... moving the value of an address to a registry, I assume...?
But I'm not used to that format and I'm having trouble scripting around it. it's usually | mov [addressmathhere],registryhere |. Not the other way around...
I was trying to upgrade my script to replace that script to something like | mov groundstatsbase,[r13+rax+88] | instead, so instead of moving the HP to another address, it would keep it on the "groundstatsbase" address (AKA the one it's already in.). but the AA window gives me an error with everything I tried to get around that idea. and thus I'm neither sure what is wrong and why, nor how to correct it. (naturally)
I still have a lot of trouble handling scripts on that regard. I see OP Codes handling registries for everything, yet it seems I cannot use them on the same ways as any other address|value, when at all.
As for everything else you said:
- lol I tried that before, remember? I told you I tried posting a script but it was too long and got cut off in the middle.
I think that was back on the first one or two pages...
- The idea is just that, I wanted to find the HP address. and now I have it. Now I just need to make it stay around in the Cheat Table for as long as the script is active, even if I die.
The initial wildcard bytes are just to keep on the right address. since IMO it's easier than having to calculate all the +7 or +3 or whatever many bytes I would otherwise need to add|subtract after the "return" lines and similar.
- The injection was, oddly enough, far from unnecessary.
Running without it was one of the many things I tried that crashed horribly the game along with my PC, it made horrid screeching noises from the game noises until it froze completely. and then I had to reset :D
But I'll try without it again, just in case I'm misremembering.
|
|
| Back to top |
|
 |
DanyDollaro
Master Cheater
![]() Reputation: 3 Reputation: 3
Joined: 01 Aug 2019
Posts: 334
|
 Posted: Fri Nov 22, 2019 11:02 am Post subject: Posted: Fri Nov 22, 2019 11:02 am Post subject: |
 |
|
I don`t know the reason for which you can`t assemble that code.
The istruction:
| Code: | | 41 8B AC 05 88 00 00 00 - mov ebp,[r13+rax+88] |
Copy the value pointed by the expression "r13+rax+88" into the register EBP.
an istruction like "mov groundstatsbase,[r13+rax+88]" is impossible to assemble, since as a first operand you are using a constant value, and as if you were trying to assemble an instruction like:
You`re moving the value of EAX to... where? nowhere, it should be:
where the value "70000" is used as the address.
And obviously you can't even assemble the instruction:
| Code: | | mov [groundstatsbase], [r13 + rax + 88] |
because you are moving two memory regions, both expressions "[groundstatsbase]" and "[r13 + rax + 88]" are reffering to addresses (In assembly the values must move through the registers)
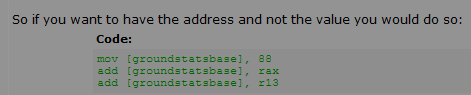
So if you want to have the address and not the value you would do so:
| Code: | push 88
pop [groundstatsbase]
add [groundstatsbase], rax
add [groundstatsbase], r13 |
Last edited by DanyDollaro on Fri Nov 22, 2019 5:02 pm; edited 1 time in total |
|
| Back to top |
|
 |
Archezuli
Advanced Cheater
 Reputation: 0 Reputation: 0
Joined: 28 Oct 2019
Posts: 58
|
 Posted: Fri Nov 22, 2019 11:32 am Post subject: Posted: Fri Nov 22, 2019 11:32 am Post subject: |
 |
|
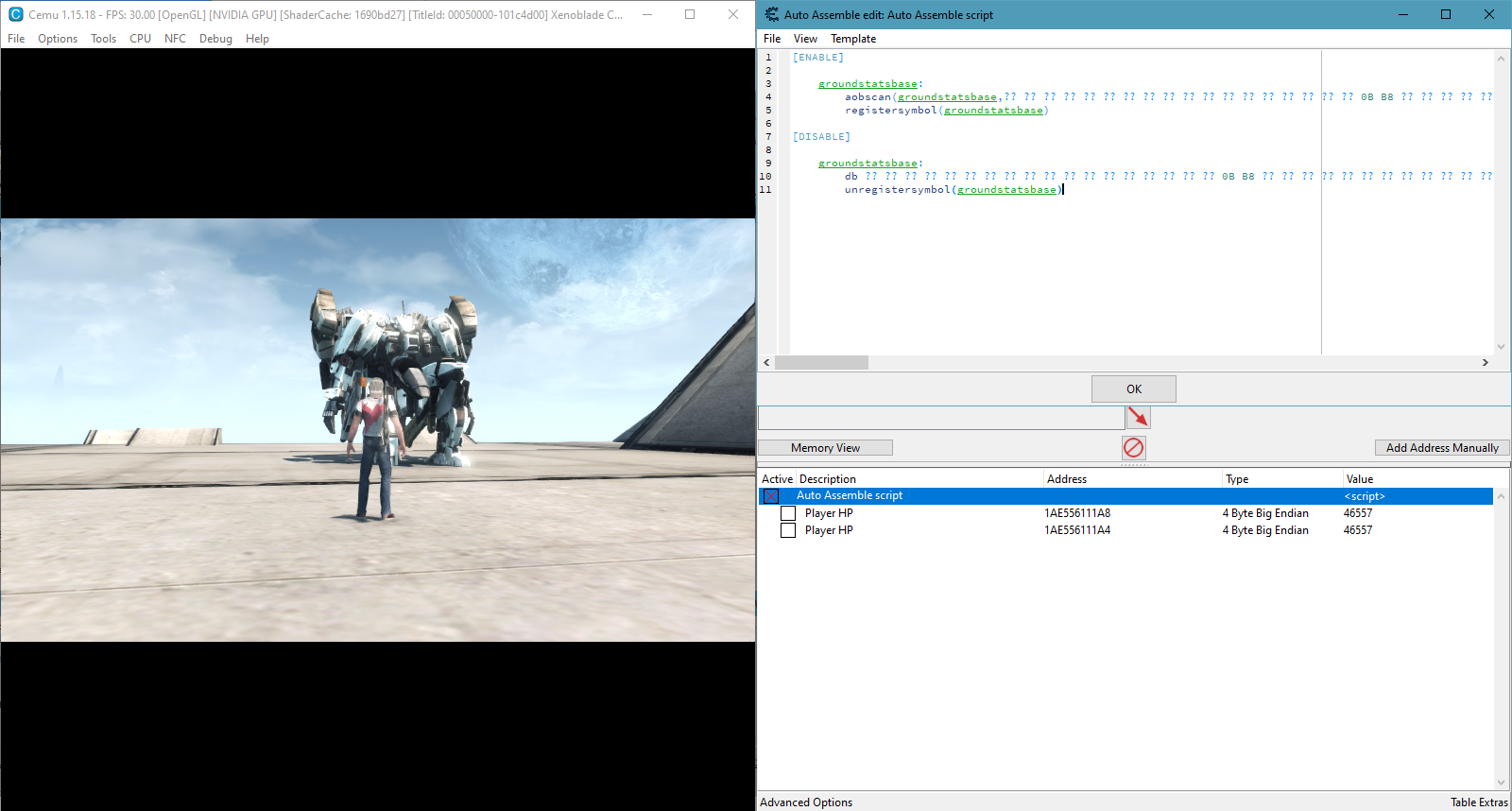
Dude this is all fascinating...
But I'm a bit lost on that last part (See pic below)
If it's not much to ask, could you maybe explain me a bit more|better why|how does that work?
How are those values added? do they copy the address of the registries to the [groundstatsbase] as value?
And if so, could I maybe use that to form the system in a separate address, and then apply the address value of it to [groundstatsbase]? would that work|make it so that it always points to the HP value? even if it changes?
| Description: |
|
| Filesize: |
2.96 KB |
| Viewed: |
5313 Time(s) |
|
|
|
| Back to top |
|
 |
DanyDollaro
Master Cheater
![]() Reputation: 3 Reputation: 3
Joined: 01 Aug 2019
Posts: 334
|
 Posted: Fri Nov 22, 2019 12:06 pm Post subject: Posted: Fri Nov 22, 2019 12:06 pm Post subject: |
 |
|
| Quote: | | do they copy the address of the registries |
The registers are small memories contained within a CPU and their read and write access is very, very, very fast, and obviously these registers are not part of the RAM and do not have an address.
As I said before:
| Quote: |
You`re moving the value of EAX to... where? nowhere, it should be:
where the value "70000" is used as the address. |
The symbol "groundstatsbase" is an address.
let's say that the registered symbol corresponds to the address 0x12345678, if you assemble an istruction like:
| Code: | | mov eax, groundstatsbase |
it is as if I were assembling:
| Code: | | mov eax, 0x12345678 |
Consequently after its execution you will have:
EAX = 0x12345678
While if you try to assemble the code:
| Code: | mov eax, 1
mov [groundstatsbase], eax |
which would be equal to:
| Code: | mov eax, 1
mov [0x12345678], eax |
You say to move the value of EAX to the value pointed by 0x12345678.
I also report this user reply on stack overflow:
| Description: |
| https://stackoverflow.com/questions/10362511/basic-use-of-immediates-vs-square-brackets-in-yasm-nasm-x86-assembly |
|
| Filesize: |
33.3 KB |
| Viewed: |
5306 Time(s) |
![ASM [].png](files/asm____823.png)
|
|
|
| Back to top |
|
 |
Archezuli
Advanced Cheater
 Reputation: 0 Reputation: 0
Joined: 28 Oct 2019
Posts: 58
|
 Posted: Fri Nov 22, 2019 1:54 pm Post subject: Posted: Fri Nov 22, 2019 1:54 pm Post subject: |
 |
|
| Quote: | The symbol "groundstatsbase" is an address.
let's say that the registered symbol corresponds to the address 0x12345678, if you assemble an istruction like:
Code:
| Code: | | mov eax, groundstatsbase |
it is as if I were assembling:
Code:
| Code: | | mov eax, 0x12345678 |
Consequently after its execution you will have:
EAX = 0x12345678 |
Wait what?!?
Shouldn't the value of 0x12345678 be on EAX after that instead...? or is that what you meant...? '~' "
| Quote: |
While if you try to assemble the code:
Code:
| Code: | mov eax, 1
mov [groundstatsbase], eax |
which would be equal to:
Code:
| Code: | mov eax, 1
mov [0x12345678], eax |
|
Yeah, that part I understood already.
| Quote: | And obviously you can't even assemble the instruction:
Code:
| Code: | | mov [groundstatsbase], [r13 + rax + 88] |
because you are moving two memory regions, both expressions "[groundstatsbase]" and "[r13 + rax + 88]" are reffering to addresses (In assembly the values must move through the registers)
So if you want to have the address and not the value you would do so:
Code:
| Code: | mov [groundstatsbase], 88
add [groundstatsbase], rax
add [groundstatsbase], r13 |
|
Okay, so...
first, why do you use mov on 88, but add on rax and r13? (I know what the codes do, I just don't understand why you need to use different ones between those two for numbers and registries.)
Theoretically, shouldn't "mov" also work with something like "rax"? thus making the register empty and moving its value to [groundstatsbase]?
And on the other side, shouldn't "add" also be possible with 88? but essentially doing the same as "mov", since 88 isn't registered|saved anywhere?
And lastly, would | add [groundstatsbase], 88+rax+r13 | work?
[EDIT:]
Yo, quick addendum:
Nothing. f@!(%n. Works.
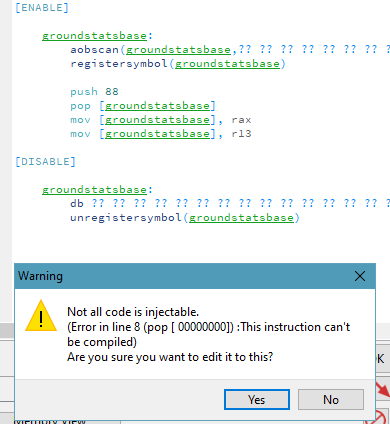
This?
mov [groundstatsbase], 88
add [groundstatsbase], rax
add [groundstatsbase], r13
Error on mov.
This?
lea rbx,[rax+r13+88]
mov [groundstatsbase],rbx
Error on mov.
Labeling groundstatsbase first?
error.
allocating space for it?
error.
Declaring it anywhere?
error.
They all. give. the same. error.
they go something like "error on line blahblahblah (whichever first line where [groundstatsbase] is found), the instruction blahblahblah [ 00000000] blahblahblah cannot be injected."
That [ 00000000] being where [groundstatsbase] is found.
Ps, I don't know if that's the exact number of zeroes.
Last edited by Archezuli on Fri Nov 22, 2019 6:07 pm; edited 1 time in total |
|
| Back to top |
|
 |
DanyDollaro
Master Cheater
![]() Reputation: 3 Reputation: 3
Joined: 01 Aug 2019
Posts: 334
|
 Posted: Fri Nov 22, 2019 5:00 pm Post subject: Posted: Fri Nov 22, 2019 5:00 pm Post subject: |
 |
|
| Quote: | | Shouldn't the value of 0x12345678 be on EAX after that instead...? or is that what you meant...? |
i mean, EAX is equal to 0x12345678.
You should learn Assembly better than you know...
You can pefectly google the istruction "mov" and better understand how it works,
First of all, this istruction don`t mov the value, but copy it.
Look at this code:
| Code: | mov eax, A // EAX is equal to 0x0A or 10 decimal
mov [Address], eax //EAX preserves its value and COPY it on the value pointed by address (the old value in Addres has been OVERWRITTEN) |
After executing this code EAX will always be equal to 10 decimal.
About this fact:
| Code: | push 88
pop [groundstatsbase]
add [groundstatsbase], rax
add [groundstatsbase], r13 |
Yes you can use "Add" and "Mov" indifferently but think about it...
Considering a 32 bit program it will use the registers like: EAX, EBX, ECX...
And they are 4 Byte registers, the maximum value that can be contained in 4 Bytes is 0xFFFFFFFF or 4.294.967.295 decimal, and considering this code:
| Code: | mov eax, FFFFFFFF
inc eax // inc = increment |
Do you know what happens? that after increasing the EAX register it will return to 0.
Now, the code:
| Code: | | mov ebp,[r13+rax+88] |
is executed many times per second together with:
| Code: | push 88
pop [groundstatsbase]
add [groundstatsbase], rax
add [groundstatsbase], r13 |
In case 1 - I use ADD instructions only:
| Code: | push 88
pop [groundstatsbase]
add [groundstatsbase], rax
add [groundstatsbase], r13 |
The value of the register is saved in the allocated memory region so initially the executed code will be fine, but if executed a second time it will obtain the double value of what it was before, making the pointer unstable.
In case 2 - I use MOV instructions only:
| Code: | push 88
pop [groundstatsbase]
mov [groundstatsbase], rax
mov [groundstatsbase], r13 |
Simply, the mov instruction overwrites the value of the first operand so the pointer value will always be equal to r13
Ps: the istruction
| Code: | | mov [groundstatsbase], 88 |
will be replace whit
| Code: | push 88
pop [groundstatsbase] |
My mistake, sorry
about this:
| Code: | | mov [groundstatsbase],rbx |
I think the problem lies in the definition of groundstatsbase, Maybe you have misallocated it, make sure you've written before:
| Code: | | alloc(groundstatsbase, 8) |
|
|
| Back to top |
|
 |
Archezuli
Advanced Cheater
 Reputation: 0 Reputation: 0
Joined: 28 Oct 2019
Posts: 58
|
 Posted: Fri Nov 22, 2019 6:09 pm Post subject: Posted: Fri Nov 22, 2019 6:09 pm Post subject: |
 |
|
Ahhhh okay... got it... x.x
But...
| Quote: | I think the problem lies in the definition of groundstatsbase, Maybe you have misallocated it, make sure you've written before:
Code:
| Code: | | alloc(groundstatsbase, 8) |
|
Tried already. :P
| Quote: | Labeling groundstatsbase first?
error.
allocating space for it?
error.
Declaring it anywhere?
error.
|
Also:
| Description: |
|
| Filesize: |
15.02 KB |
| Viewed: |
5255 Time(s) |
|
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 0
Reputation: 0 Reputation: 0
Reputation: 0 Reputation: 0
Reputation: 0 Reputation: 0
Reputation: 0 Reputation: 0
Reputation: 0 Reputation: 0
Reputation: 0 Reputation: 0
Reputation: 0 Reputation: 0
Reputation: 0


![ASM [].png](files/asm____823.png)
