 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
Menoetius
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 01 Jul 2018
Posts: 29
|
 Posted: Mon Jul 23, 2018 5:15 pm Post subject: Cheatengine Tutorial x86_x64: Pointer of a Pointer Problem Posted: Mon Jul 23, 2018 5:15 pm Post subject: Cheatengine Tutorial x86_x64: Pointer of a Pointer Problem |
 |
|
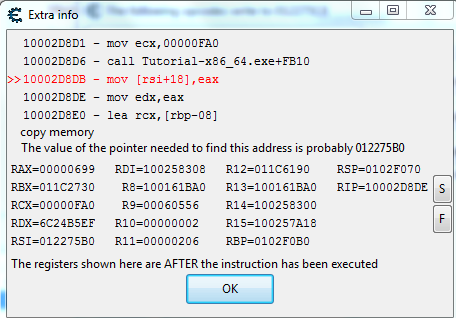
I've done cheat engine for a few years on and off, and I've completed the tutorial before, but I wanted to do it again just to refresh on stuff. When I get to the first pointer for problem 8 in the tutorial, I'm greeted with mismatching registers. I'm likely misunderstanding what it's telling me, but mov [rsi+18],eax seems to be off? I've seen numerous other tutorials and none have eax-->rsi or really any r-registers. Maybe Tutorial-x86_64.exe is the wrong to run on a 64bit windows 7. Whatever it is, the pointer I enter in doesn't work correctly and point to the address it's directed at. How many things am I doing wrong, and what can I do to remedy them?
RAX=00000D7F
RBX=011C2730
RCX=00000FA0
RDX=DD26C726
RSI=012275B0
RDI=100258308
RBP=0102F0B0
RSP=0102F070
RIP=10002D8DE
Probable base pointer =012275B0
10002D8D1 - mov ecx,00000FA0
10002D8D6 - call Tutorial-x86_64.exe+FB10
10002D8DB - mov [rsi+18],eax
10002D8DE - mov edx,eax
10002D8E0 - lea rcx,[rbp-08]
imgur com /a/QeLaj9v
| Description: |
|
| Filesize: |
40.28 KB |
| Viewed: |
4348 Time(s) |
|
_________________
Big Gun
#1
Shoot the Hell Outta You |
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 458 Reputation: 458
Joined: 09 May 2003
Posts: 25296
Location: The netherlands
|
 Posted: Mon Jul 23, 2018 11:16 pm Post subject: Posted: Mon Jul 23, 2018 11:16 pm Post subject: |
 |
|
in 64 bit applications R registers are the only possible registers between [address] specificators so that's good
you need to scan the memory for the value that rsi has
and remember, use find what accesses every time. Not only find what writes what MANY tutorials online tell you to
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
Menoetius
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 01 Jul 2018
Posts: 29
|
 Posted: Tue Jul 24, 2018 12:40 pm Post subject: Thanks, and I'll Welcome You With Another Question Posted: Tue Jul 24, 2018 12:40 pm Post subject: Thanks, and I'll Welcome You With Another Question |
 |
|
A'ight, thank you kindly for your reply and time and making this nifty program.
If I ever needed to ascertain the value of eax, what would the steps be, or can I quickly find the how to somewhere else? I haven't found much about them other than the intel processor manual.
_________________
Big Gun
#1
Shoot the Hell Outta You |
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 458 Reputation: 458
Joined: 09 May 2003
Posts: 25296
Location: The netherlands
|
 Posted: Tue Jul 24, 2018 12:50 pm Post subject: Posted: Tue Jul 24, 2018 12:50 pm Post subject: |
 |
|
eax is the lower 32-bit part of the 64-bit rax register
in the image above rax has the value 0000000000000699
the lower 32-bit contains the value 00000699 so eax has the value 0x699 (which is 1689 decimal)
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
Menoetius
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 01 Jul 2018
Posts: 29
|
 Posted: Tue Jul 24, 2018 1:40 pm Post subject: Ah, ha Posted: Tue Jul 24, 2018 1:40 pm Post subject: Ah, ha |
 |
|
That makes so much sense when you say that. I don't know why I was confused now.
I haven't had to do this before, and I have looked for this online and found no questions or answers akin to this, so I'm probably missing something obvious, but how would I change the Code Finder settings? I don't believe I've needed to, but I'd like to know how and possibly in what cases I may be required to.
I might actually need to change the codefinder settings, as mov rsi, [rsi] seems to point to itself. I attempted to break and trace in the instructions to no avail. What may I attempt next? Apologies for asking questions that may have been asked before, but I have certainly searched the internet before coming directly to the board to ask trivial questions. Pointers of pointers is always the most difficult for me, hopefully understandably.
Thank you again preemptively whether or not you answer my questions again. You've been sincerely helpful and I'm really grateful for the CE program in general.
| Description: |
rsi loops back to itself
I understand [rsi] is the value of the previous one and need to find it before it was modified |
|
| Filesize: |
35.61 KB |
| Viewed: |
4297 Time(s) |
![mov rsi,[rsi].png](files/mov_rsi__rsi__431.png)
|
_________________
Big Gun
#1
Shoot the Hell Outta You
Last edited by Menoetius on Tue Jul 24, 2018 1:59 pm; edited 1 time in total |
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 458 Reputation: 458
Joined: 09 May 2003
Posts: 25296
Location: The netherlands
|
 Posted: Tue Jul 24, 2018 1:58 pm Post subject: Posted: Tue Jul 24, 2018 1:58 pm Post subject: |
 |
|
there are a few settings that affect the code finder.
the main ones are veh debug, override existing breakpoints and breakpoint methods
veh debug helps in case the default windows debugger is broken
overriding existing breakpoikts helps if all 4 hardware bp's are in use by the game. Downside is that the game will usually crashbwithon seconds so get the data as quickly as you need
breakpoint methods are useful in csse devug registers just won't work. page exceptions are almost as good as debug registers, but a lot slower
as for the screenshot you posted, while you say to ignore it, may require some explenation:
firstly you can read this as
| Code: |
mov rsi,[rsi+00000000]
|
which means the offset is 0 which is valid (many people get confused at that one)
now the special case here is that this instruction overwrites rsi with the value stored at the address the okd RSI represented
and since the register states are AFTER it has been executed the value of RSI is lost.
BUUUT no despair here, since you did a "find what accesses" on a specific address you KNOW what rsi+00000000 was. (the address)
so that address minus 00000000 is the original valie of RSI
hopefully this helps
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
Menoetius
Cheater
![]() Reputation: 0 Reputation: 0
Joined: 01 Jul 2018
Posts: 29
|
 Posted: Tue Jul 24, 2018 10:49 pm Post subject: Posted: Tue Jul 24, 2018 10:49 pm Post subject: |
 |
|
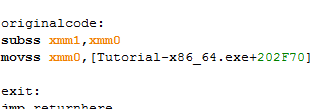
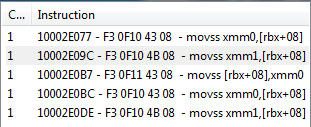
Finally waded through the Pointers problem, only to be left at the steps of splitting values/addresses from an opcode in x64? speak. I've looked around and no walkthroughs address xmm registers along with their respective operations. I've navigated through finding what this opcode writes to, and checking similarities. At first I was unable to find any, but noticed the value for 0014 was hidden in a small tab from pointer. When I tried to click the drop down CE crashed, so the next time I changed the value of the offset from 10 to 14 to display a nice set of 1s and 2s to differentiate teams. I then attempted to find out what accesses this code and whoo boy, I was greeted with this in Figure A. Going through their xmm registers I was able to discern that the second opcode had the value of xmm0={amount of health subtracted} that was being subtracted from the xmm1={current hp} register. All the opcodes look the almost the same, with a difference between it using xmm0 and xmm1 for its operations. However, and I've played around with a bunch of different opcodes like addss for xmm0,xmm1 and sometimes it didn't subtract directly or instadie after I made the
cmp [rbx+14],1
jne originalcode
{whatever operations I attempted}
What should I do next, and why do I appear to be the only one who has had this issue?
-------------------------------------------------------------------------------------
I finally managed to get it to work after hours of replacing opcodes. Turns out, subss was an effective equivalent of fsubr dword ptr [ebp-30], and I just needed to replace that with an addss, instead of replacing one of the movss xmm0,[rbx+08] or movss xmm1,xmm0. Just keep throwin enough stuff at it til it finally worked - aint that the way of life?
Thank you kindly for all your help, but I wish I understood why It was showing xmm and r-registers instead of most people's e-registers. I definitely recall it not being like this the first time I attempted the cheatengine tutorial. I hope to be able to have another welcoming questions forum in the future, and that this may help others who've encountered the same issues - unlike those who say "problem solved" without telling how.
[ENABLE]
//code from here to '[DISABLE]' will be used to enable the cheat
alloc(newmem,2048,"Tutorial-x86_64.exe"+2E0A1)
label(returnhere)
label(originalcode)
label(exit)
newmem: //this is allocated memory, you have read,write,execute access
//place your code here
cmp [rbx+14],1 //comparing teams's
jne originalcode //jumps to original code of sub
addss xmm1,xmm0 //if cmp = true, adds to hp instead of sub
jmp exit //exits properly SO IMPORTANT OR IT OFTEN DOES NOTHING
originalcode:
subss xmm1,xmm0
jmp exit //exits properly
exit:
movss xmm0,[Tutorial-x86_64.exe+202F70]
jmp returnhere
"Tutorial-x86_64.exe"+2E0A1:
jmp newmem
nop
nop
nop
nop
nop
nop
nop
returnhere: //contiunes rest of program
[DISABLE]
//code from here till the end of the code will be used to disable the cheat
dealloc(newmem)
"Tutorial-x86_64.exe"+2E0A1:
subss xmm1,xmm0
movss xmm0,[Tutorial-x86_64.exe+202F70]
//Alt: db F3 0F 5C C8 F3 0F 10 05 C3 4E 1D 00
| Description: |
|
| Filesize: |
3.55 KB |
| Viewed: |
4283 Time(s) |
|
| Description: |
|
| Filesize: |
6.88 KB |
| Viewed: |
4283 Time(s) |
|
_________________
Big Gun
#1
Shoot the Hell Outta You |
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 458
Reputation: 458 Reputation: 458
Reputation: 458 Reputation: 458
Reputation: 458


![mov rsi,[rsi].png](files/mov_rsi__rsi__431.png)

