 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
massil
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 31 Dec 2015
Posts: 13
|
 Posted: Fri Jan 01, 2016 8:30 am Post subject: problems with pointers in w8 and w10 Posted: Fri Jan 01, 2016 8:30 am Post subject: problems with pointers in w8 and w10 |
 |
|
Hi all, first at all Happy new years for allbody.
I'm new on this comunity and i will not write so much cause my english is really bad, but I try to write in the best way possible.
My problem is a browser game, when I do a search for a pointer in w7 I can find it but w8 and w10, once said pointer found by closing the browser or Reboot the computer the pointer changes and I have to re-and again seek. (translate of google).
Could someone tell me why is it?.
Thanks all.
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4697
|
 Posted: Fri Jan 01, 2016 10:35 am Post subject: Posted: Fri Jan 01, 2016 10:35 am Post subject: |
 |
|
Sometimes pointers work differently on different computers. That's why it's recommended to rescan a pointerlist on at least one different computer if you're going to be releasing that table.
What type of game is it? Flash? Unity? HTML/Javascript? If the game runs on a VM like flash, then you won't be able to find any reliable static pointers to anything useful.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
massil
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 31 Dec 2015
Posts: 13
|
 Posted: Fri Jan 01, 2016 11:28 am Post subject: Posted: Fri Jan 01, 2016 11:28 am Post subject: |
 |
|
The game is HTML/Javascript.
I look for pointers to float variable camera. The fact is that in all that I do win7 works and does not change the pointer, but win8 and w10, I can not keep this pointer.
For example, the value on float is 25 and the camera is too close. So i change 25 for 30. In w7 I created a trainer to make it easier and faster that i actually use.
Thanks Parkour
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4697
|
 Posted: Fri Jan 01, 2016 11:45 am Post subject: Posted: Fri Jan 01, 2016 11:45 am Post subject: |
 |
|
I'd recommend using an AoB injection on instructions that access the camera and change them to whatever you want.
You could also use the AoB injection to only copy the address of the camera into a registered symbol and add that to your table (injection copy).
If you really want a static pointer, though, then use the pointer scanner and rescan that list on different computers.
Tutorial on making scripts here.
Tutorial on injection copy / pointer scanner here.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
massil
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 31 Dec 2015
Posts: 13
|
 Posted: Fri Jan 01, 2016 12:09 pm Post subject: Posted: Fri Jan 01, 2016 12:09 pm Post subject: |
 |
|
I use always pointer scanner and rescan, but that i said before on w8 and w10, this values changes and i have to start again.
Thanks so much for those tutorials and i had read a lot and I can not because the instruction is (call.....)
Last edited by massil on Fri Jan 01, 2016 1:44 pm; edited 1 time in total |
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4697
|
 Posted: Fri Jan 01, 2016 12:28 pm Post subject: Posted: Fri Jan 01, 2016 12:28 pm Post subject: |
 |
|
So take the pointerscan file from your w7 computer and copy it onto your w8/w10 computer. Then rescan it again. If everything is invalid, then expand your search settings by increasing the max level and/or max offset, then repeat.
That instruction is not directly accessing your camera. That would mean the address of your camera is executable and is being run by the game.
PS: you forgot to censor the module names of the instructions' addresses.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
massil
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 31 Dec 2015
Posts: 13
|
 Posted: Fri Jan 01, 2016 1:40 pm Post subject: Posted: Fri Jan 01, 2016 1:40 pm Post subject: |
 |
|
| ParkourPenguin wrote: |
PS: you forgot to censor the module names of the instructions' addresses. |
Thats true i'm stupid haha, sorry.
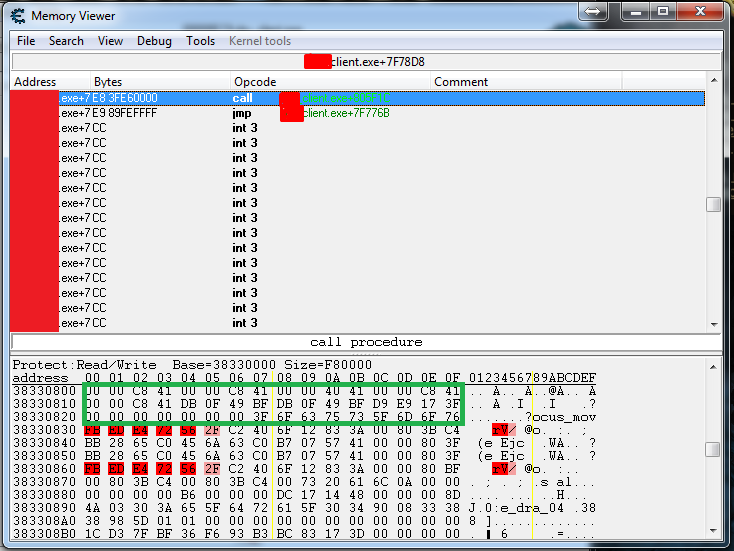
I tried to file w7 in W10 and no favorable results. With that kind of instruction, could not I use AoB injection?.
i would like change the green section:
| Description: |
|
| Filesize: |
69.54 KB |
| Viewed: |
6045 Time(s) |
|
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4697
|
 Posted: Fri Jan 01, 2016 1:54 pm Post subject: Posted: Fri Jan 01, 2016 1:54 pm Post subject: |
 |
|
That instruction is not directly accessing your camera.
Right click on the address of your camera in your table and select "Find out what writes to this address". Pick one of the instructions there and do an AoB injection on that.
If none show up that are writing to it after playing the game for a while, then right click it and select "Find out what accesses this address" and do an AoB injection on one of those.
If that green block of memory is static, then you can use createthread to change it to whatever you want. If it isn't static, then find a static reference to it (pointers) or make your own (injection copy, but you could do anything you want to that block in the script itself).
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
massil
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 31 Dec 2015
Posts: 13
|
 Posted: Fri Jan 01, 2016 3:04 pm Post subject: Posted: Fri Jan 01, 2016 3:04 pm Post subject: |
 |
|
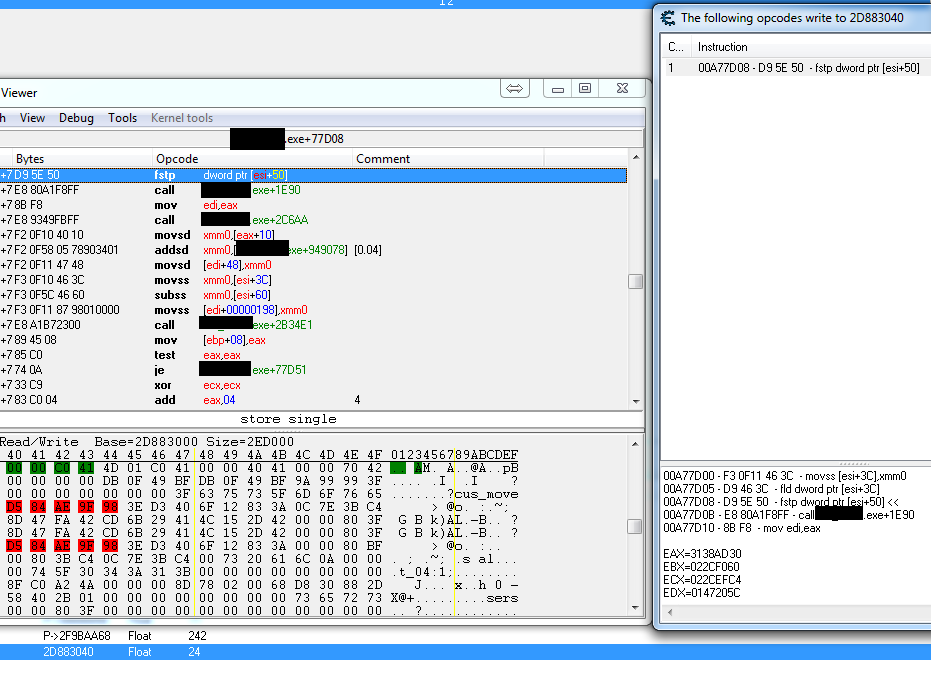
Forgive me I was showing the view of the pointer memory.
This is what I get with the direct address. Could i do anything?
| Description: |
|
| Filesize: |
61.28 KB |
| Viewed: |
5976 Time(s) |
|
Last edited by massil on Fri Jan 01, 2016 6:14 pm; edited 2 times in total |
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4697
|
 Posted: Fri Jan 01, 2016 5:22 pm Post subject: Posted: Fri Jan 01, 2016 5:22 pm Post subject: |
 |
|
Maybe. There are three main questions on whether or not you can do a code injection on a particular instruction:
1: Roughly how often is that instruction run? Your code will only be executed when that instruction is run, so if it only runs once or it runs every hour or something ridiculous like that, that would be bad.
2: Does that instruction access any other addresses? Right click on it in the disassembler and select "Find out what addresses this instruction accesses". If it does, then look for instructions that access the address of your camera and try to find an instruction that only accesses that address.
3: Is the AoB signature unique? You need to scan for an AoB representing the memory region around the instruction you want to modify in an AoB injection. To check this, set the type to Array of byte, make sure the writable and executable checkboxes are grey, and scan for the AoB signature. Try this signature:
D9 5E ?? E8 ?? ?? ?? ?? 8B ?? E8 ?? ?? ?? ?? F2 0F 10 40 ?? F2 0F 58 05
If more than 1 result pops up, it's not unique. If there are no results, then make sure you're scanning all memory (writable/executable checkboxes are grey) and that your signature is correct. That signature should be unique, unless the game allocated some memory exactly like this one somewhere else.
It's not a deal breaker if you can't find a unique signature in this case since this code is inside a module and probably won't change its location relative to it. AoB scans are still better because if the game updates there's a higher chance that this will still work.
You also need to make sure you have enough space for a jump, but that usually isn't a problem. However, in this case, using that instruction for the jump would make it kind of awkward with that call right afterwords. It's still possible, but it might be easier using a previous instruction. Could you scroll up a bit (around 10 instructions) on that window and post an image of that?
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
massil
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 31 Dec 2015
Posts: 13
|
 Posted: Fri Jan 01, 2016 6:06 pm Post subject: Posted: Fri Jan 01, 2016 6:06 pm Post subject: |
 |
|
Thanks so much Parkour, i get something with this script:
[ENABLE]
aobscanmodule(INJECT,XXX.exe,D9 5E 50 E8 80 A1 F8 FF) // should be unique
alloc(newmem,$1000)
label(code)
label(return)
newmem:
code:
fstp dword ptr [esi+50]
add [esi+50],1011111
call XXX.exe+1E90
jmp return
INJECT:
jmp code
nop
nop
nop
return:
registersymbol(INJECT)
[DISABLE]
INJECT:
db D9 5E 50 E8 80 A1 F8 FF
unregistersymbol(INJECT)
dealloc(newmem)
I have search like u tell me on step 3 and the Signature is unique.I was reading the tutorials and i did what i can.
One of my biggest problems is that most do not understand the instructions (dword, jump ...).
I would like to ask you one more thing about what I want to change, but I will not be very insistent.
|
|
| Back to top |
|
 |
ParkourPenguin
I post too much
 Reputation: 152 Reputation: 152
Joined: 06 Jul 2014
Posts: 4697
|
 Posted: Fri Jan 01, 2016 7:28 pm Post subject: Posted: Fri Jan 01, 2016 7:28 pm Post subject: |
 |
|
One minor thing that could be a problem would be that call XXX.exe+1E90 you have will probably crash the game if the game has an update since the location of that function would probably change. Also, if that call used an r/m32 instead of a rel32 and the module was loaded into a different spot of memory when you restart the game, it would crash when you disable the script. It's using the rel32 version, though, so no worries (until you update the game).
Anyway, what's going on is this:
jmp is easy. It's like telling the computer "I want you to go over here and execute this code". In this case, you're overriding the old instructions and telling the computer to go execute your new code. After your new code is done running, there's a jmp back to the spot after the first jmp so the application can continue running normally.
Now for fstp. There's a thing called the FPU stack that stores floating point numbers (i.e. float & double). The instruction fstp dword ptr [esi+50] takes whatever's on the top of that stack and stores it into the address esi+50, then it removes that number from the stack. The dword ptr part just means that you're working with a data size of 4 bytes, so that would be a float. If it said qword ptr, then you'd be working with 8 bytes, so you'd me moving a double.
If you want to add a number to that float, you can use fadd dword ptr m32 to do that just before the fstp. Unfortunately, there's no addressing mode of fadd that uses an imm32, so you have to store your value in memory somewhere. However, that isn't the best way to do it in this case.
A better way IMO would be to pop that value off the FPU stack and move your own value directly into the address. Like so:
| Code: | [ENABLE]
aobscanmodule(INJECT,XXX.exe,D9 5E 50 E8 80 A1 F8 FF)
alloc(newmem,1024)
label(myFOV)
label(return)
registersymbol(INJECT)
registersymbol(myFOV)
newmem:
fstp st(0) // pops old value off the FPU stack
push eax // backs up eax
mov eax,[myFOV] // moves new value into eax
mov [esi+50],eax // moves new value into destination
pop eax // restores backup of eax
call XXX.exe+1E90 // original code
jmp return
db CC CC CC CC // padding; ignore
myFOV:
dd (float)30.0 // the new value
INJECT:
jmp code
nop
nop
nop
return:
[DISABLE]
INJECT:
db D9 5E 50 E8 80 A1 F8 FF
unregistersymbol(INJECT)
unregistersymbol(myFOV)
dealloc(newmem) |
If this script is enabled, you can specify the FOV via that registered symbol. Just click on "Add Address Manually", put in myFOV for the address, change the type to float, and you can change it as you want.
If you have any questions, feel free to ask. I'm happy to answer them.
_________________
I don't know where I'm going, but I'll figure it out when I get there. |
|
| Back to top |
|
 |
massil
Newbie cheater
![]() Reputation: 0 Reputation: 0
Joined: 31 Dec 2015
Posts: 13
|
 Posted: Sat Jan 02, 2016 4:32 am Post subject: Posted: Sat Jan 02, 2016 4:32 am Post subject: |
 |
|
I tried it on my w10 and my way works perfectly. After rebooting my computer I went back into the game and was still running.
That is, if I add code at the end of a value before it is shown, I can change it. If not, the game crash.
Following one of the tutorials you sent me, I managed to find the value of the camera.
| Code: |
[ENABLE]
aobscanmodule(INJECT XXX.exe,D9 5E 50 E8 80 A1 F8 FF) // should be unique
alloc(newmem,$1000)
label(code)
label(return)
globalalloc(_camera,4)
newmem:
code:
fstp dword ptr [esi+50]
mov [_camera],esi
call XXX.exe+1E90
jmp return
INJECT:
jmp code
nop
nop
nop
return:
registersymbol(INJECT)
[DISABLE]
INJECT:
db D9 5E 50 E8 80 A1 F8 FF
unregistersymbol(INJECT)
dealloc(newmem)
|
If i add address manually I get its value (25):
With respect to my question, I just solved my myself right now.
I wanted to modify a pointer close to this value, so changing the assembly [esi + 50] by [esi + 60], I get and modify the desired value.
Thank you so much for your help Parkour,You're a great guy.
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 152
Reputation: 152 Reputation: 152
Reputation: 152 Reputation: 152
Reputation: 152 Reputation: 152
Reputation: 152 Reputation: 152
Reputation: 152 Reputation: 152
Reputation: 152


