 |
Cheat Engine
The Official Site of Cheat Engine
|
| View previous topic :: View next topic |
| Author |
Message |
NanoByte
Expert Cheater
![]() Reputation: 1 Reputation: 1
Joined: 13 Sep 2013
Posts: 222
|
 Posted: Sun Jun 01, 2014 8:31 am Post subject: Calculating Bytes ? Posted: Sun Jun 01, 2014 8:31 am Post subject: Calculating Bytes ? |
 |
|
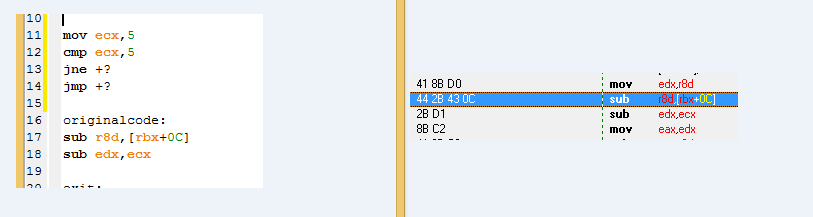
if you look to the right where it says
mov edx,r8d its 3 bytes but how did that came to be?
mov 1byte + edx 1byte + r8d 1byte?
now if u look at left where my code says
mov ecx,5
how many bytes would this be? its because i want to learn to use
jmp +6 //just an example
i know you can @f @b but i want to learn this too
| Description: |
|
| Filesize: |
8.88 KB |
| Viewed: |
7755 Time(s) |
|
|
|
| Back to top |
|
 |
Polynomial
Grandmaster Cheater
![]() Reputation: 5 Reputation: 5
Joined: 17 Feb 2008
Posts: 524
Location: Inside the Intel CET shadow stack
|
 Posted: Sun Jun 01, 2014 9:06 am Post subject: Posted: Sun Jun 01, 2014 9:06 am Post subject: |
 |
|
It's complicated. A full explanation of instruction encoding for x86-64 can be found here.
To start off, let's be clear about the instruction: it moves the value of the 32-bit R8D extended register into the 32-bit EDX register.
The tl;dr is that you have an extended register instruction prefix (known as REX), which is encoded as 0b0100WRXB. Basically, the REX prefix says that the instruction is using an extended register as one of its operands.
The 0b0100 translates to the first nybble (the 4 in 0x41) which specifies that it's a REX prefix. The second nybble contains the W, R, X, and B flags. In this case, you've got 0b0001 as your second nybble, which means that only the B flag is set. In this case, it specifies that the MODRM.rm operand field is extended. The "rm" operand field targets the operand, for a particular instruction, that can accept a register or memory (the official language is "direct or indirect"). Note that instructions (usually) only have one of these - you can't do "mov [eax], [ebx]" - so it's unambiguous.
If you look at the screenshot you gave, you'll notice that the prefixed instruction is encoded as (41) 8B D0, and further along you have an 8B C2 for a "mov eax, edx". The 8B is the mov opcode, for which the description is "mov r16/32, r/m16/32". This means that, by default, it moves either a 16 or 32-bit memory or register value into a 16 or 32-bit register. Now, remember that the B flag says that it marks the MODRM.rm operand field as extended. In this case, the second operand of the mov instruction is rm, so this states that the second operand is extended.
Now, onto the encoding of opcodes. This is done via the MODRM structure, which is an 8-bit value split into 3 sections: a 2-bit mod, a 3-bit reg, and a 3-bit rm. The values of these describe direct or indirect mode operands. The mod value splits the table into 4 rows, with 00, 01, and 10 describing different classes of indirect reference, and 11 describing direct reference. Think of the different indirect references as things like [reg+reg] and [reg+reg*4], etc.
In this case, your 0xD0 byte translates to mod=11, reg=010, rm=000. Since mod is 11, that means we're using direct register referencing (i.e. just reg rather than [reg]), so we just look at the register table. In the notation used in the table I linked, the bit before the dot is the extended flag (remember we found B was set in our REX prefix, to say that the rm operand is extended?). So, if we look up 0.010 for reg=010 on the 32-bit GP column, we find edx. If we then look up 1.000 for rm=000 on the 32-bit GP column again, we find r8d.
So now we know that our instruction is a mov, it takes direct registers as operands, its rm operand is extended, and it uses edx for its reg operand and r8d for its rm operand, so we can visualise that as "mov edx, r8d".
Hope that explains it sufficiently 
_________________
It's not fun unless every exploit mitigation is enabled.
Please do not reply to my posts with LLM-generated slop; I consider it to be an insult to my time. |
|
| Back to top |
|
 |
NanoByte
Expert Cheater
![]() Reputation: 1 Reputation: 1
Joined: 13 Sep 2013
Posts: 222
|
 Posted: Sun Jun 01, 2014 11:22 am Post subject: Posted: Sun Jun 01, 2014 11:22 am Post subject: |
 |
|
HOLY SHIT, you were not kidding when u said
My Brain is on Fire AAAAAAAARH!
|
|
| Back to top |
|
 |
justa_dude
Grandmaster Cheater
 Reputation: 23 Reputation: 23
Joined: 29 Jun 2010
Posts: 893
|
 Posted: Sun Jun 01, 2014 11:50 am Post subject: Posted: Sun Jun 01, 2014 11:50 am Post subject: |
 |
|
It's better to just use labels, imho. If your goal is to avoid labels so that you can more easily convert to trainers, then you ought to instead look into something like ASMJIT that will basically ape CE's AA and save you a lot of headaches troubleshooting injected machine code.
_________________
A nagy kapu mellett, mindig van egy kis kapu.
----------------------
Come on... |
|
| Back to top |
|
 |
mgr.inz.Player
I post too much
 Reputation: 222 Reputation: 222
Joined: 07 Nov 2008
Posts: 4438
Location: W kraju nad Wisla. UTC+01:00
|
 Posted: Sun Jun 01, 2014 11:51 am Post subject: Posted: Sun Jun 01, 2014 11:51 am Post subject: |
 |
|
I will pour some fuel into the fire
For example sub eax,edx can be represented by this:
- 29 D0
or this:
- 2B C2

_________________
|
|
| Back to top |
|
 |
justa_dude
Grandmaster Cheater
 Reputation: 23 Reputation: 23
Joined: 29 Jun 2010
Posts: 893
|
 Posted: Sun Jun 01, 2014 11:55 am Post subject: Posted: Sun Jun 01, 2014 11:55 am Post subject: |
 |
|
| mgr.inz.Player wrote: | I will pour some fuel into the fire
For example sub eax,edx can be represented by this:
- 29 D0
or this:
- 2B C2
:twisted: |
Yar, or worse yet some instruction mnemonics will assemble into machine code of differing length depending on the location to which they are assembled.
_________________
A nagy kapu mellett, mindig van egy kis kapu.
----------------------
Come on... |
|
| Back to top |
|
 |
Polynomial
Grandmaster Cheater
![]() Reputation: 5 Reputation: 5
Joined: 17 Feb 2008
Posts: 524
Location: Inside the Intel CET shadow stack
|
 Posted: Sun Jun 01, 2014 12:07 pm Post subject: Posted: Sun Jun 01, 2014 12:07 pm Post subject: |
 |
|
| mgr.inz.Player wrote: | | For example sub eax,edx can be represented by 29 D0 or 2B C2 |
While this is true, it's not really complicated to translate. The same rules apply. It just means you have to be careful if you ever try to scan for an instruction - you have to disassemble and scan for the textual representation rather than assemble and scan for the bytes.
Also, it's important to note that 29 is used when there's a lock prefix, or when you're doing "sub [reg], reg". The 2B opcode isn't valid with a lock prefix and is used for doing "sub reg, [reg]".
Interestingly, there doesn't appear to be a "sub reg, [reg]" opcode that is valid with a lock prefix.
_________________
It's not fun unless every exploit mitigation is enabled.
Please do not reply to my posts with LLM-generated slop; I consider it to be an insult to my time. |
|
| Back to top |
|
 |
mgr.inz.Player
I post too much
 Reputation: 222 Reputation: 222
Joined: 07 Nov 2008
Posts: 4438
Location: W kraju nad Wisla. UTC+01:00
|
 Posted: Sun Jun 01, 2014 12:21 pm Post subject: Posted: Sun Jun 01, 2014 12:21 pm Post subject: |
 |
|
^^^ exactly 
29 (SUB r/m32,r32) and 2B (SUB r32,r/m32), both can be used for SUB r32,r32
Many register-register operations have two encodings.
_________________
|
|
| Back to top |
|
 |
NanoByte
Expert Cheater
![]() Reputation: 1 Reputation: 1
Joined: 13 Sep 2013
Posts: 222
|
 Posted: Sun Jun 01, 2014 1:33 pm Post subject: Posted: Sun Jun 01, 2014 1:33 pm Post subject: |
 |
|
Smile and wave
| Description: |
|
| Filesize: |
20.95 KB |
| Viewed: |
7679 Time(s) |

|
|
|
| Back to top |
|
 |
|
|
You cannot post new topics in this forum
You cannot reply to topics in this forum
You cannot edit your posts in this forum
You cannot delete your posts in this forum
You cannot vote in polls in this forum
You cannot attach files in this forum
You can download files in this forum
|
|

 Reputation: 23
Reputation: 23 Reputation: 222
Reputation: 222 Reputation: 23
Reputation: 23 Reputation: 222
Reputation: 222


